Added
Spot potential attacks with Login Failed (no Account ID) event type
March 7th, 2024
🔔New feature alert! We've made it easier for you to spot credential stuffing attacks.
- Spot credential stuffing attacks! When users attempt to access your platform by inputting a username and password that does not exist, you will see a 🚫 Login Failed attempt with no Account ID in Explorer.
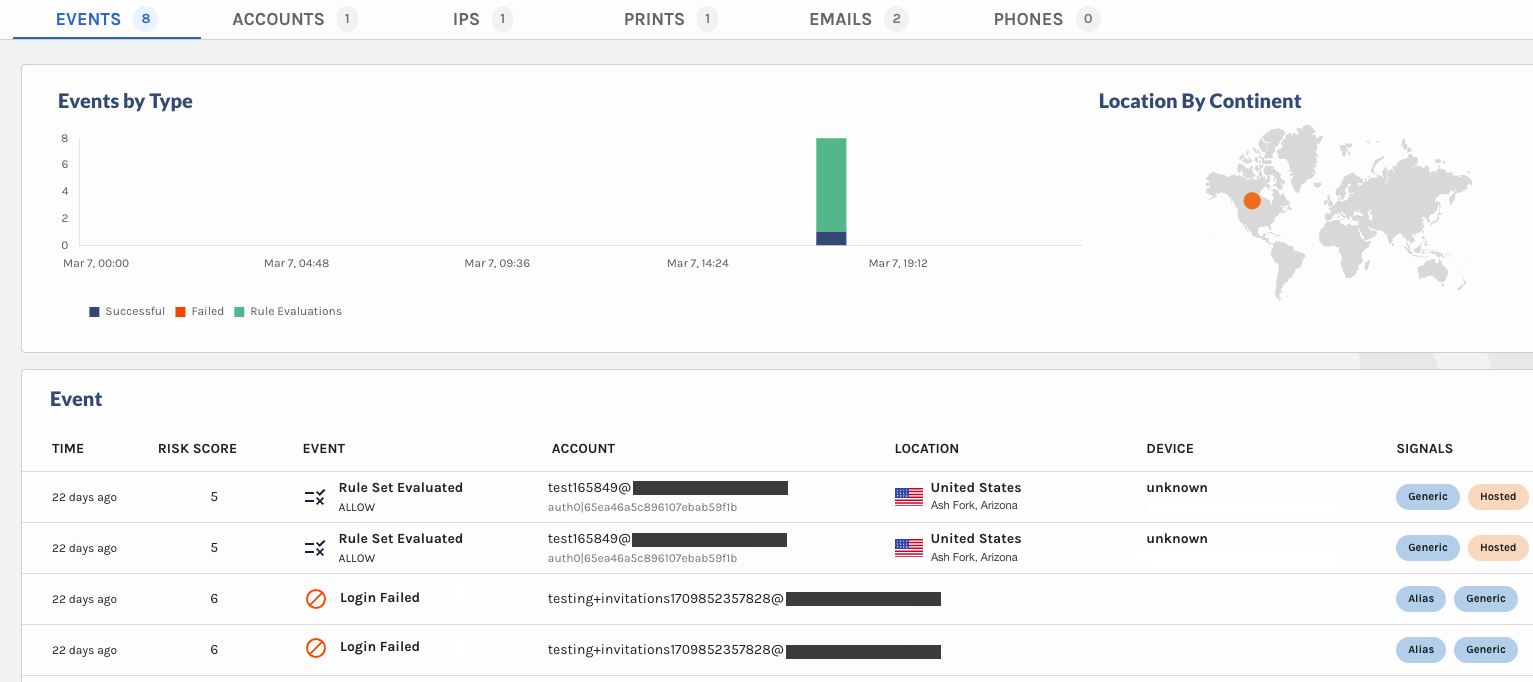
The last two rows of this Events table shows 🚫 Login Failed attempts with no Account ID, signs of a potential credential stuffing attack
⚠️ Note that if you open up the Events side panel and then try to see the Email in the SignalPrint graph, it will not display because there is no Account ID associated.
- Perhaps you want to learn more about an account while looking at Events in Explorer. Click on the Account cell in the Events table and see the Account side panel for more details.
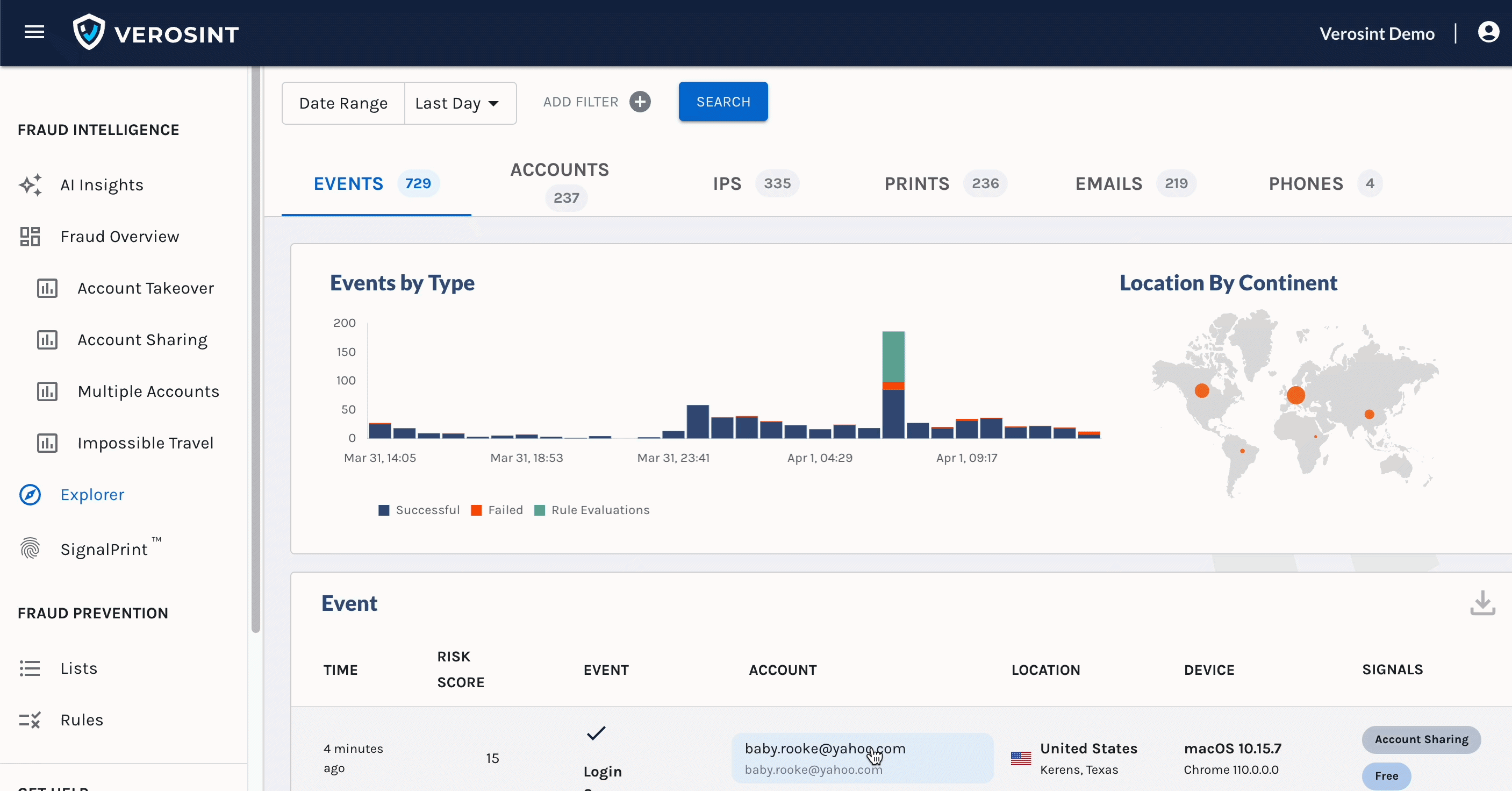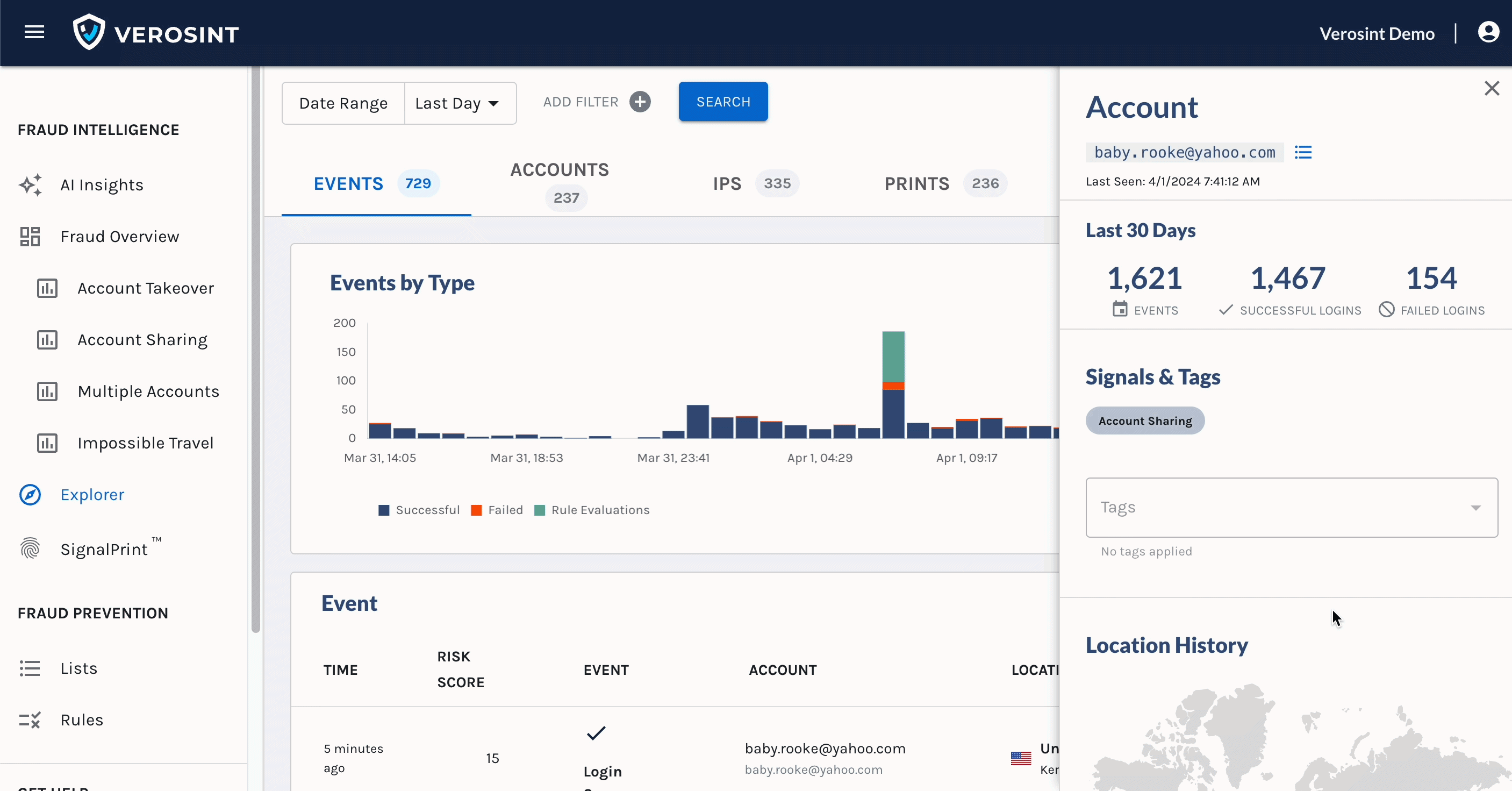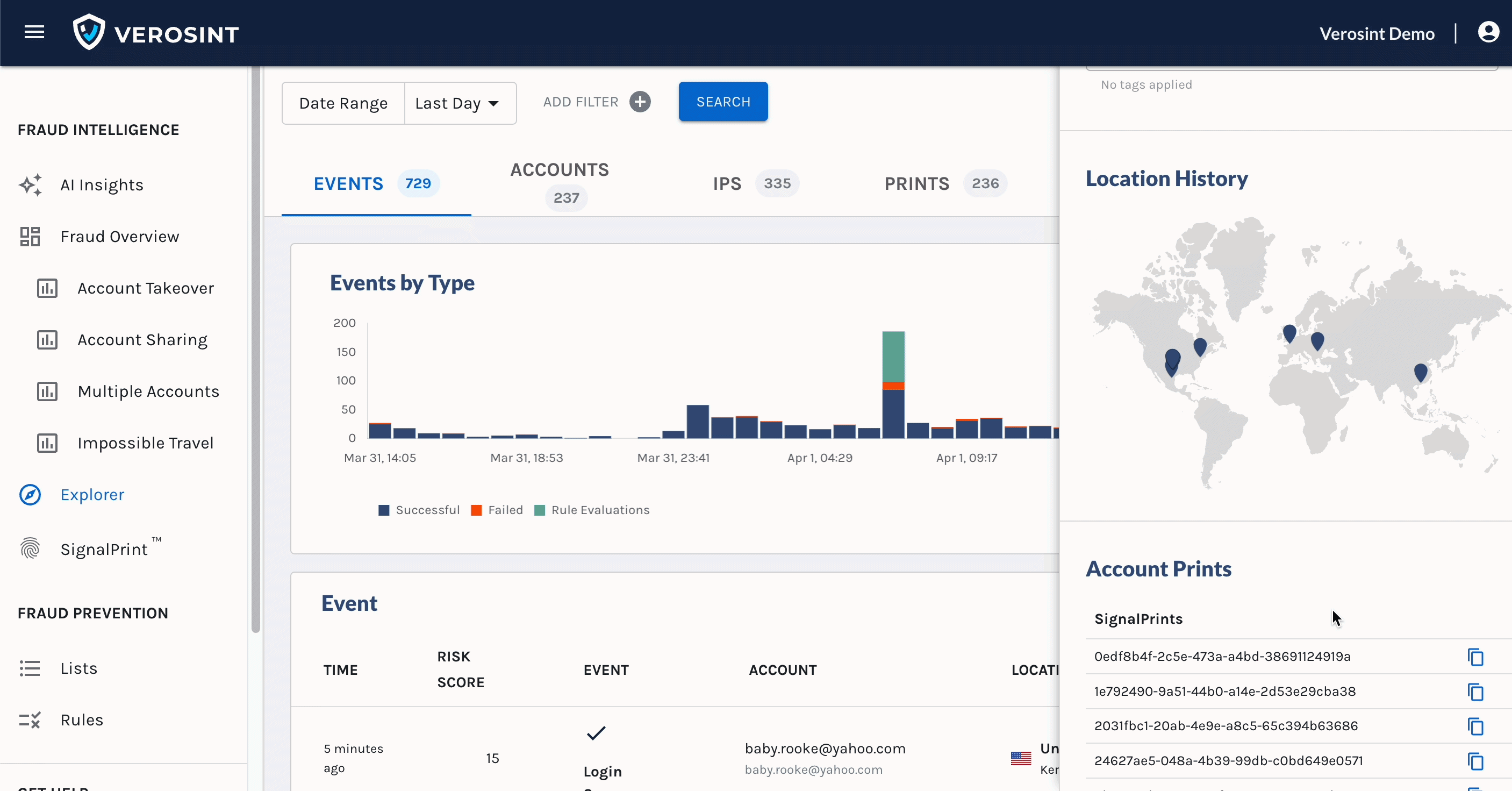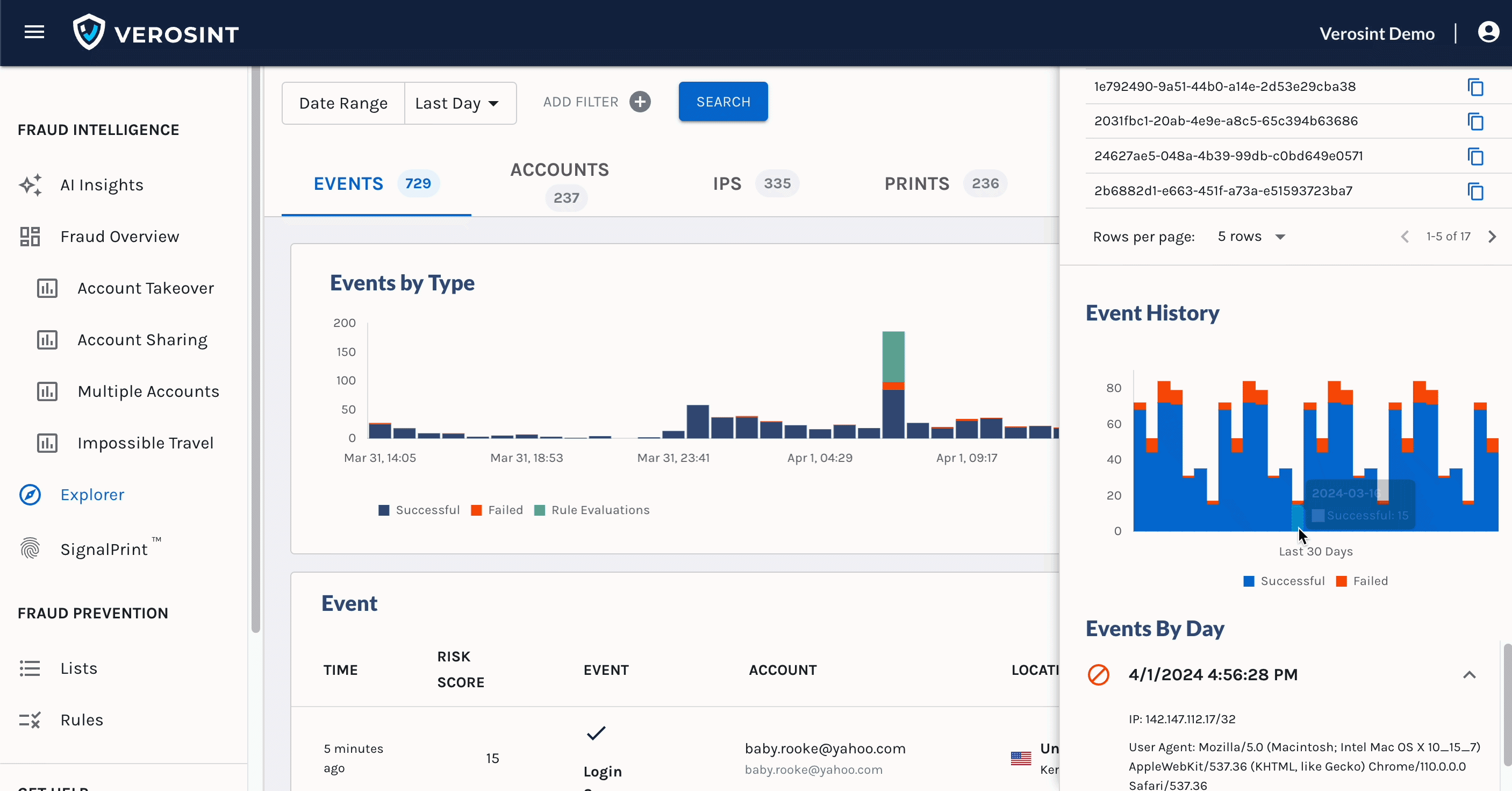
Access the Account side panel from the Events table