🌟 New Feature Alert 🌟
What's New?
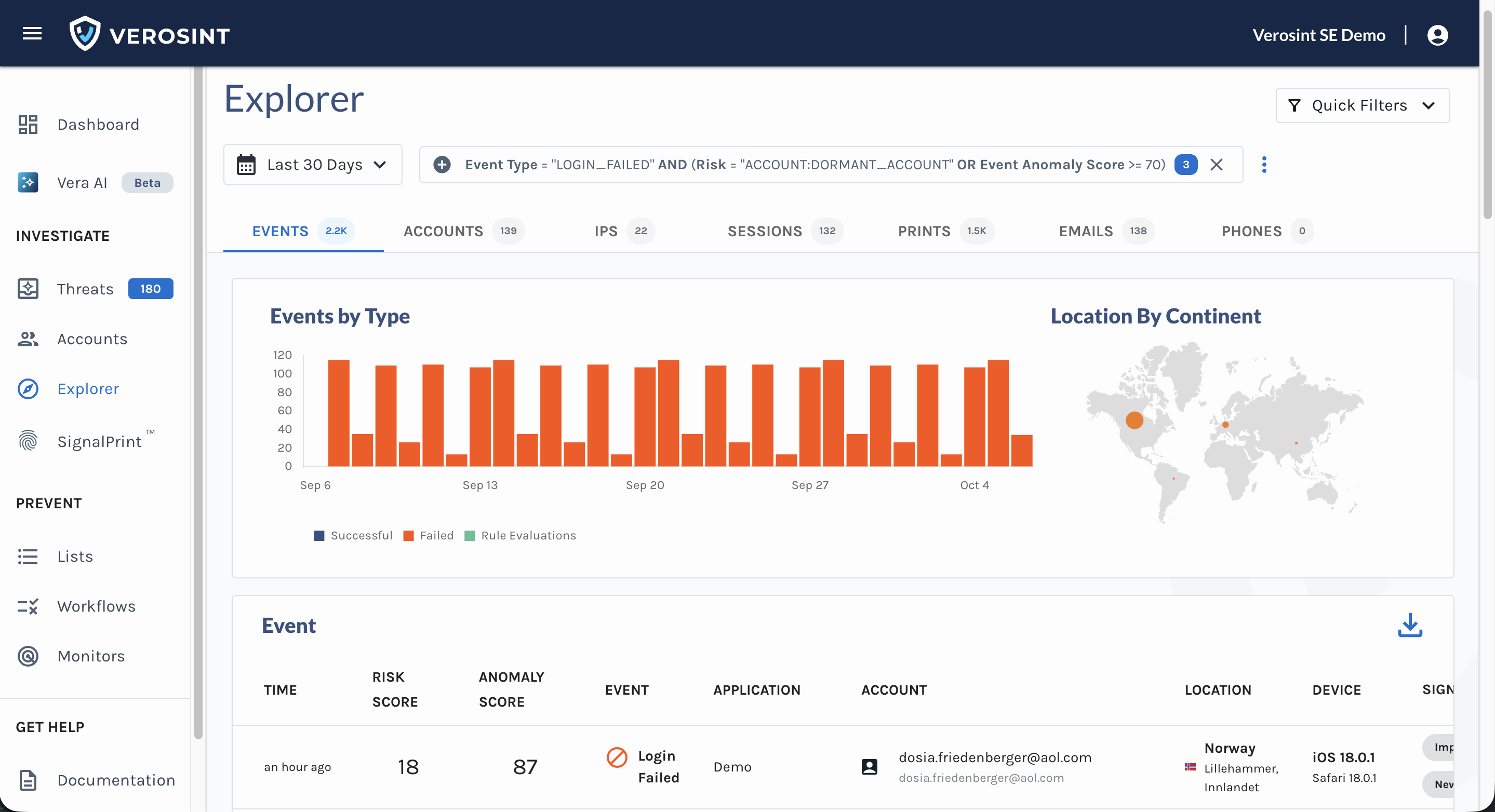
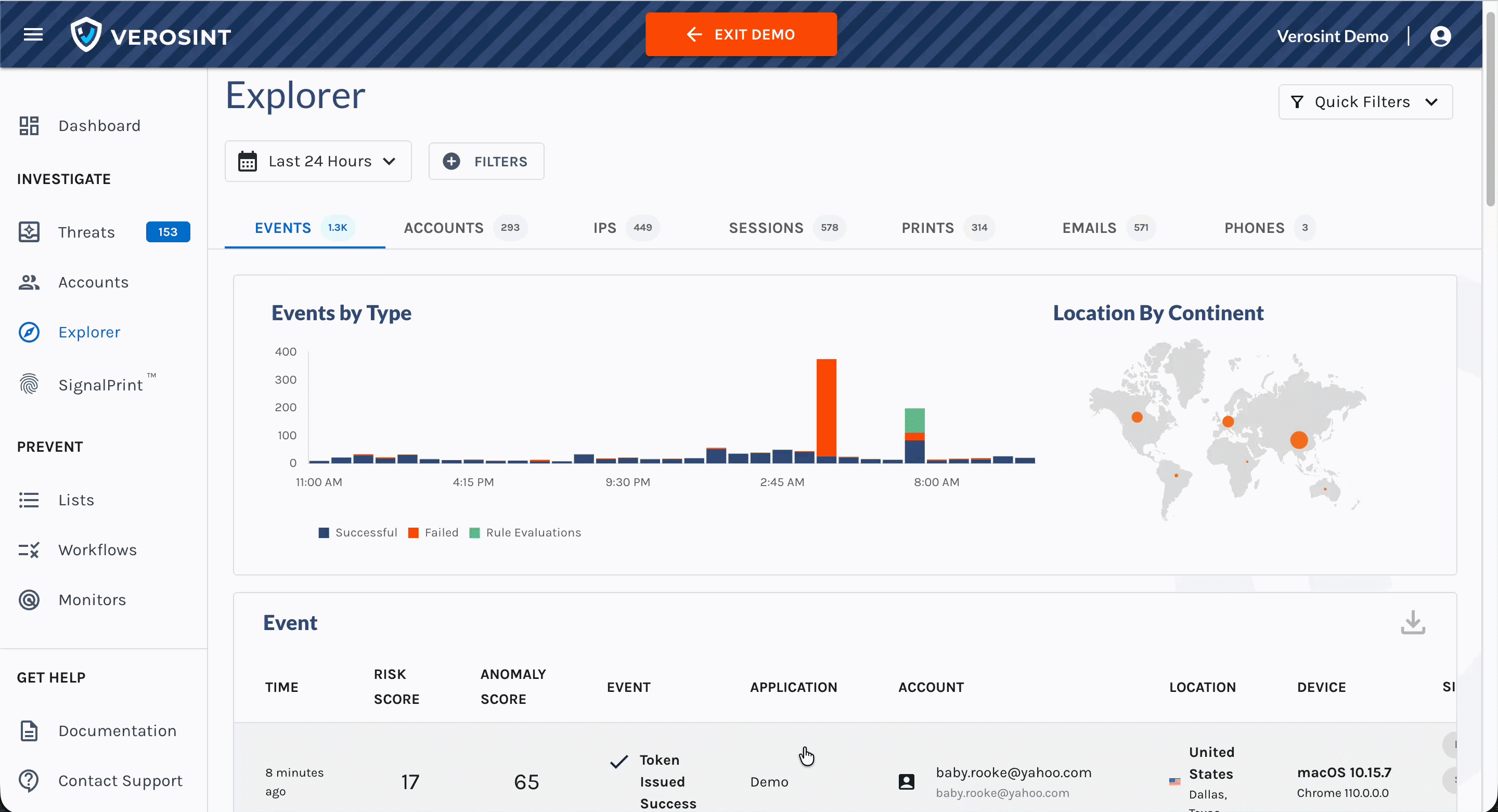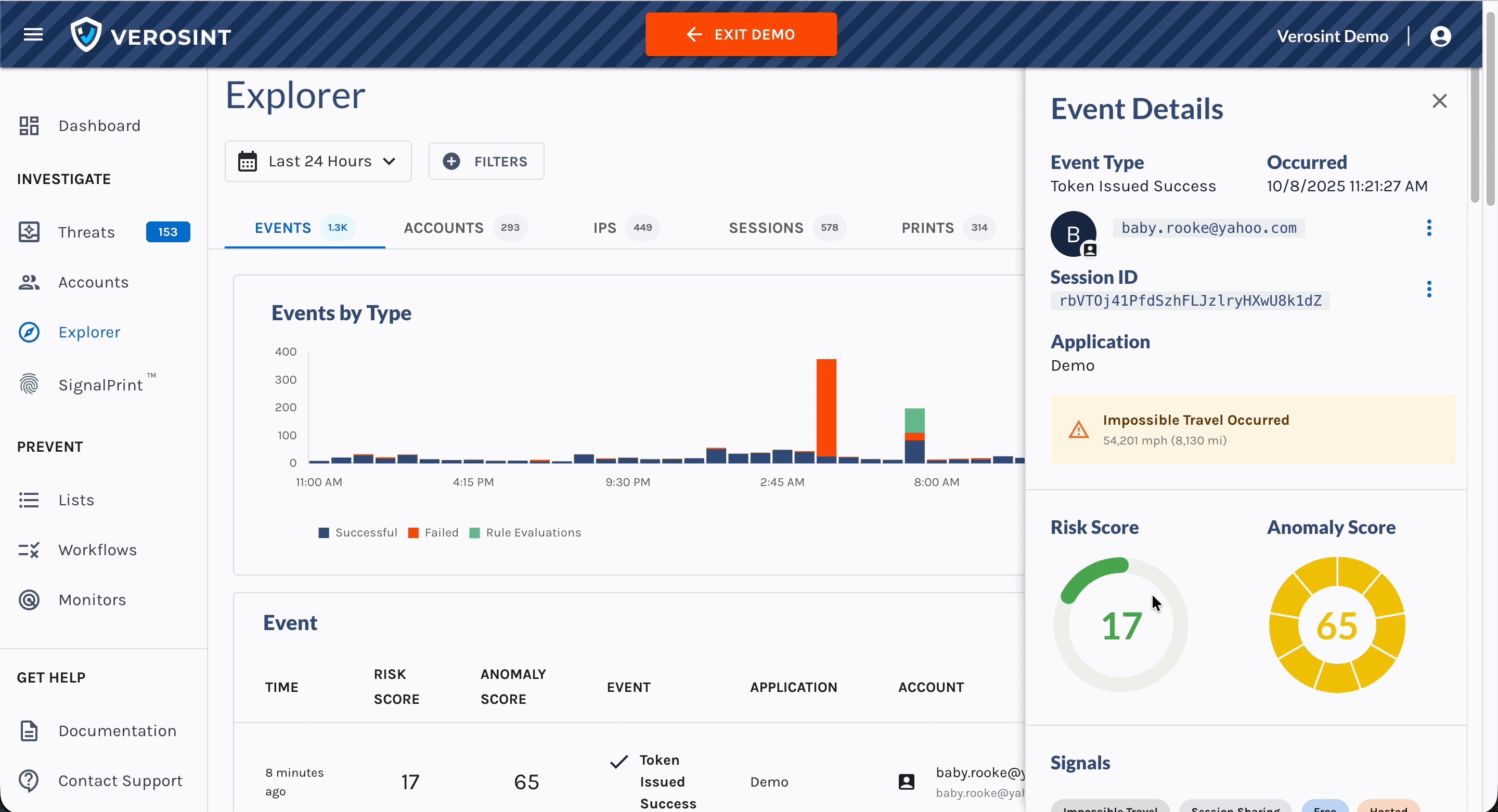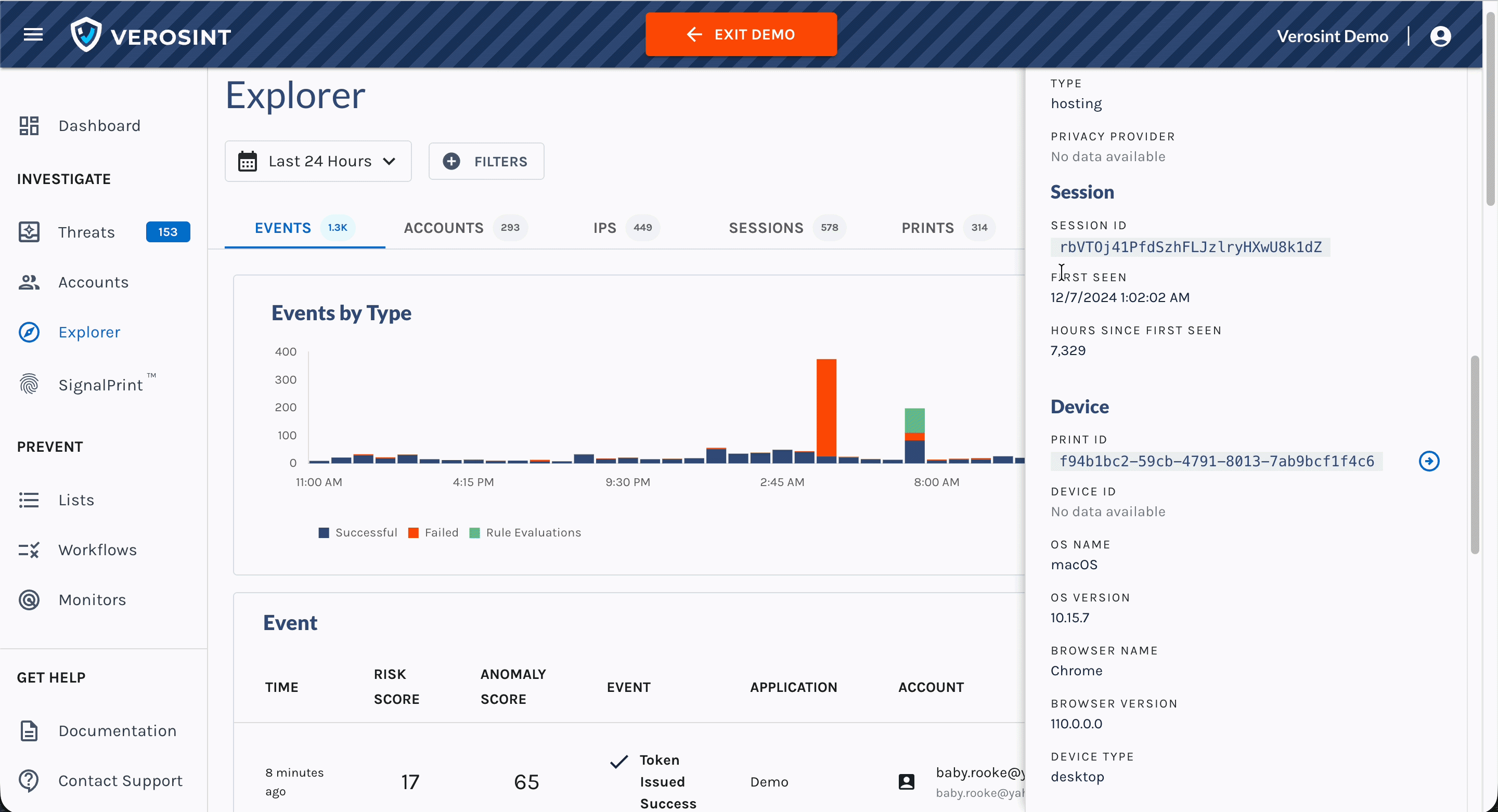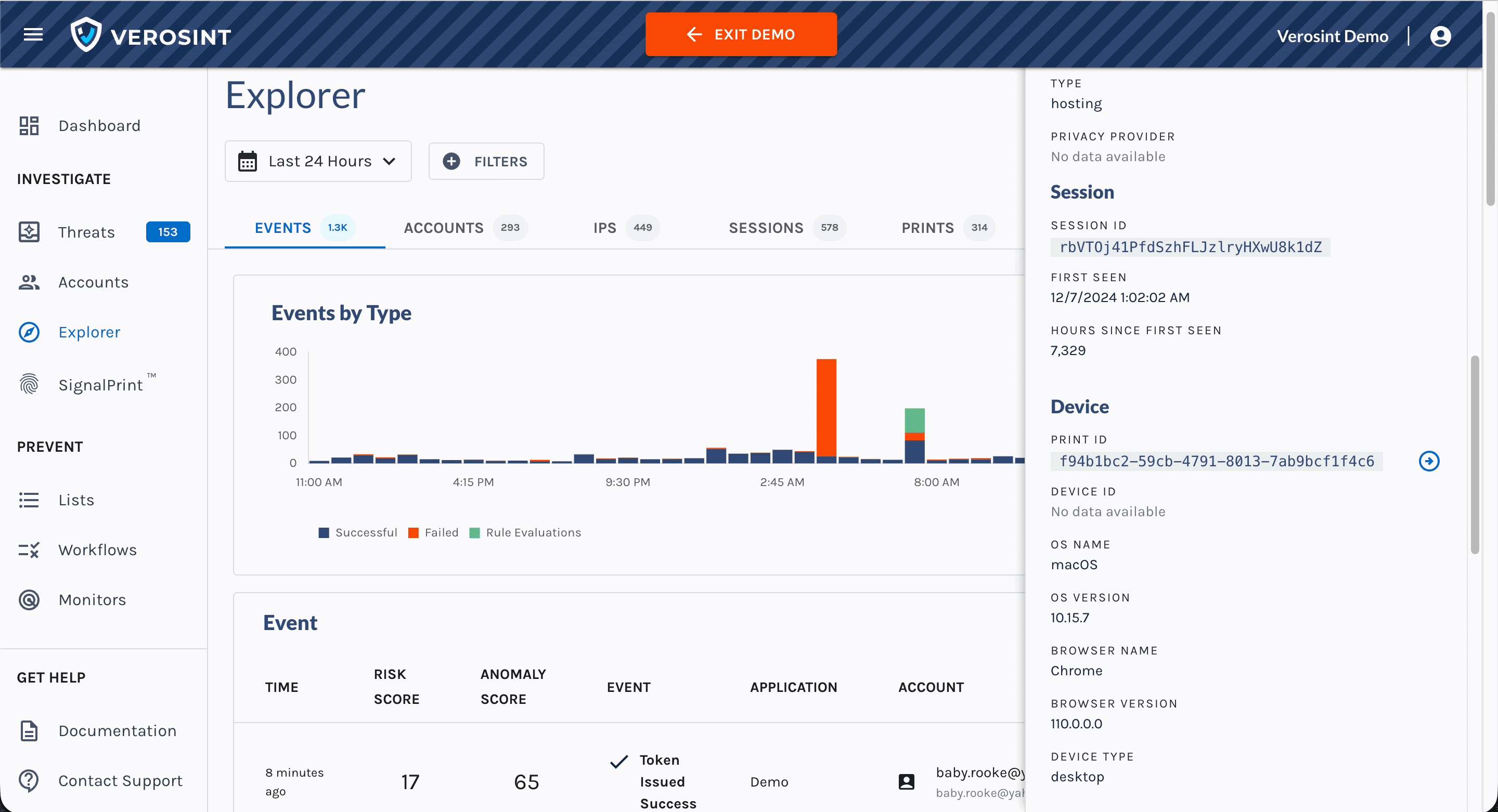
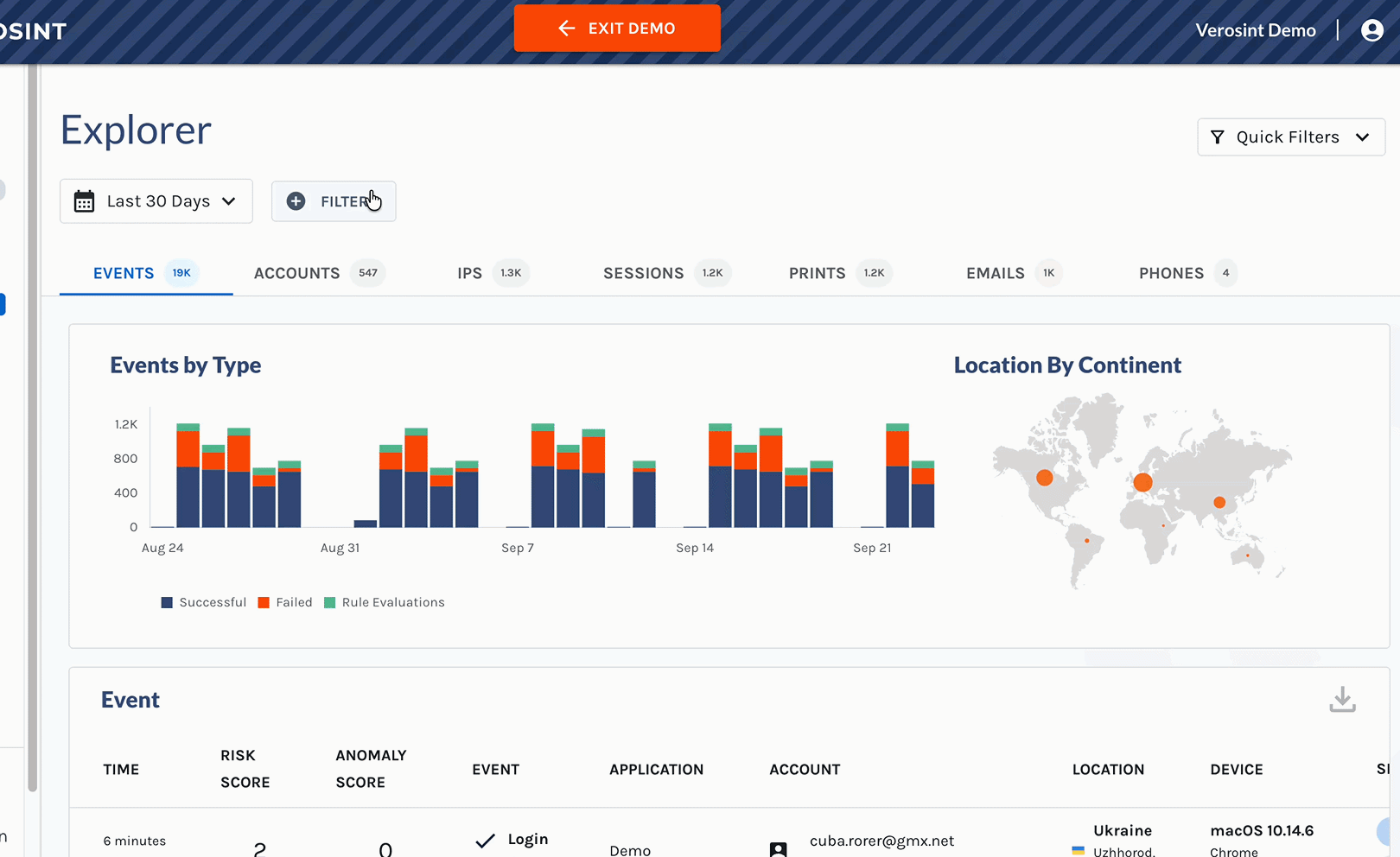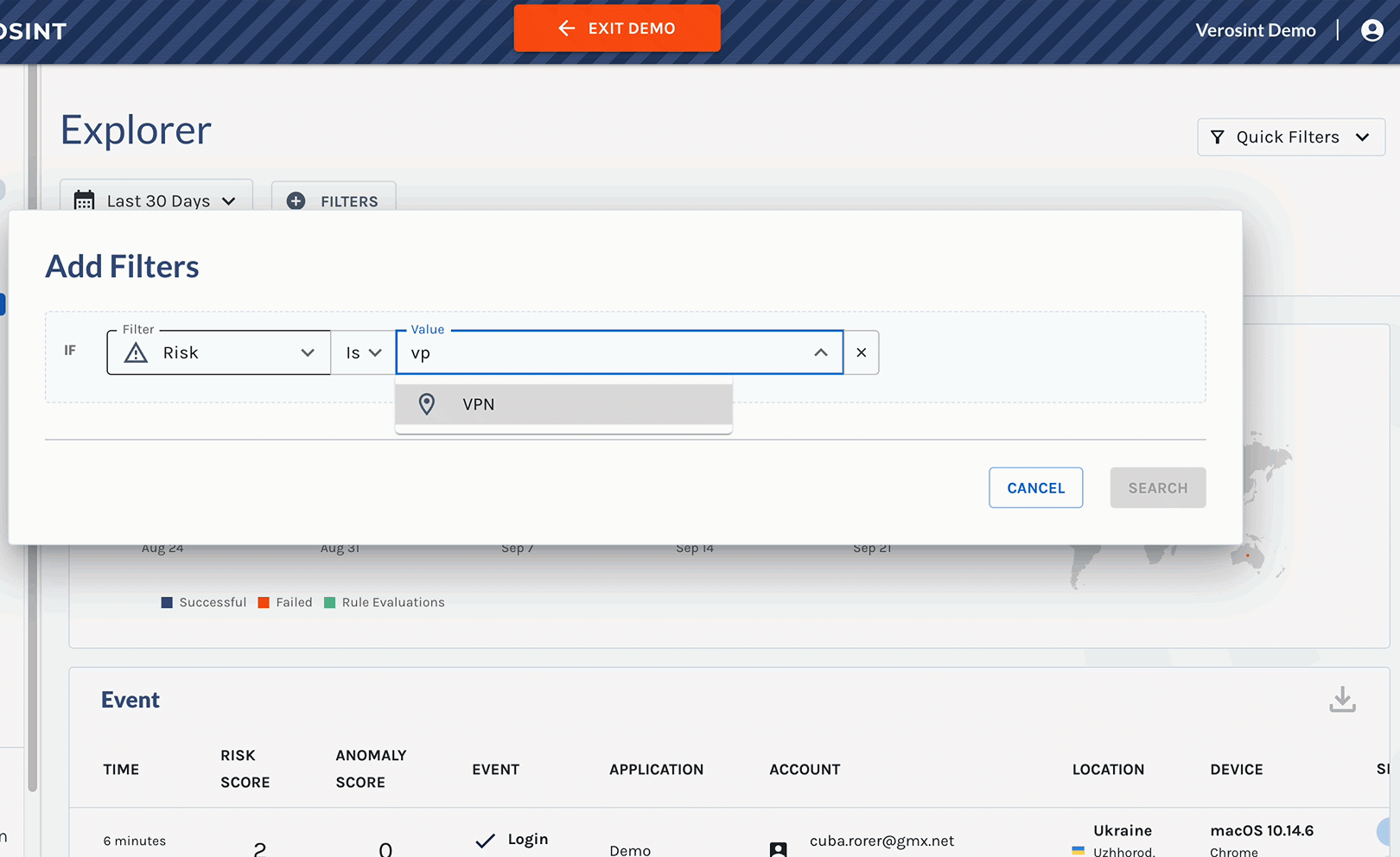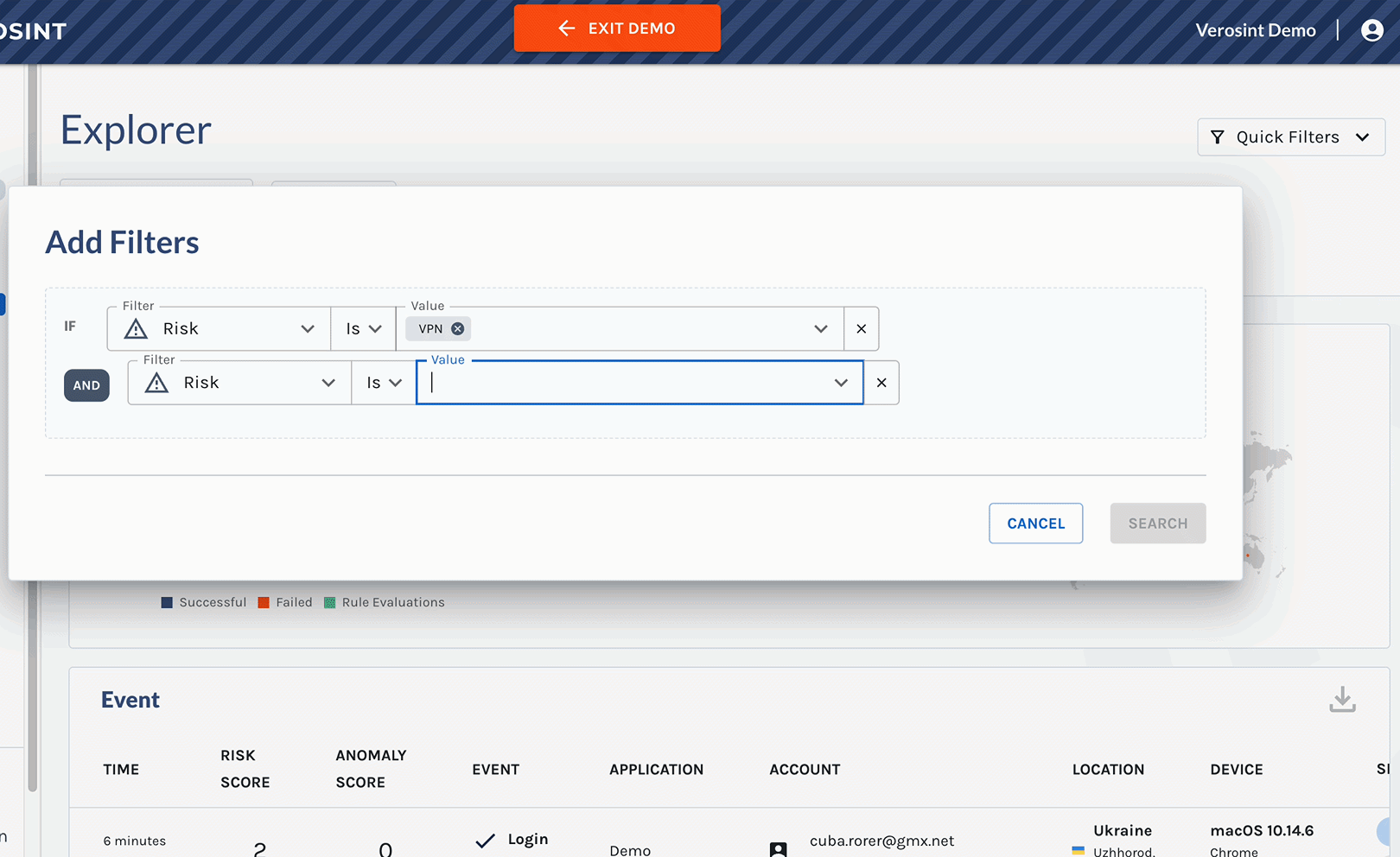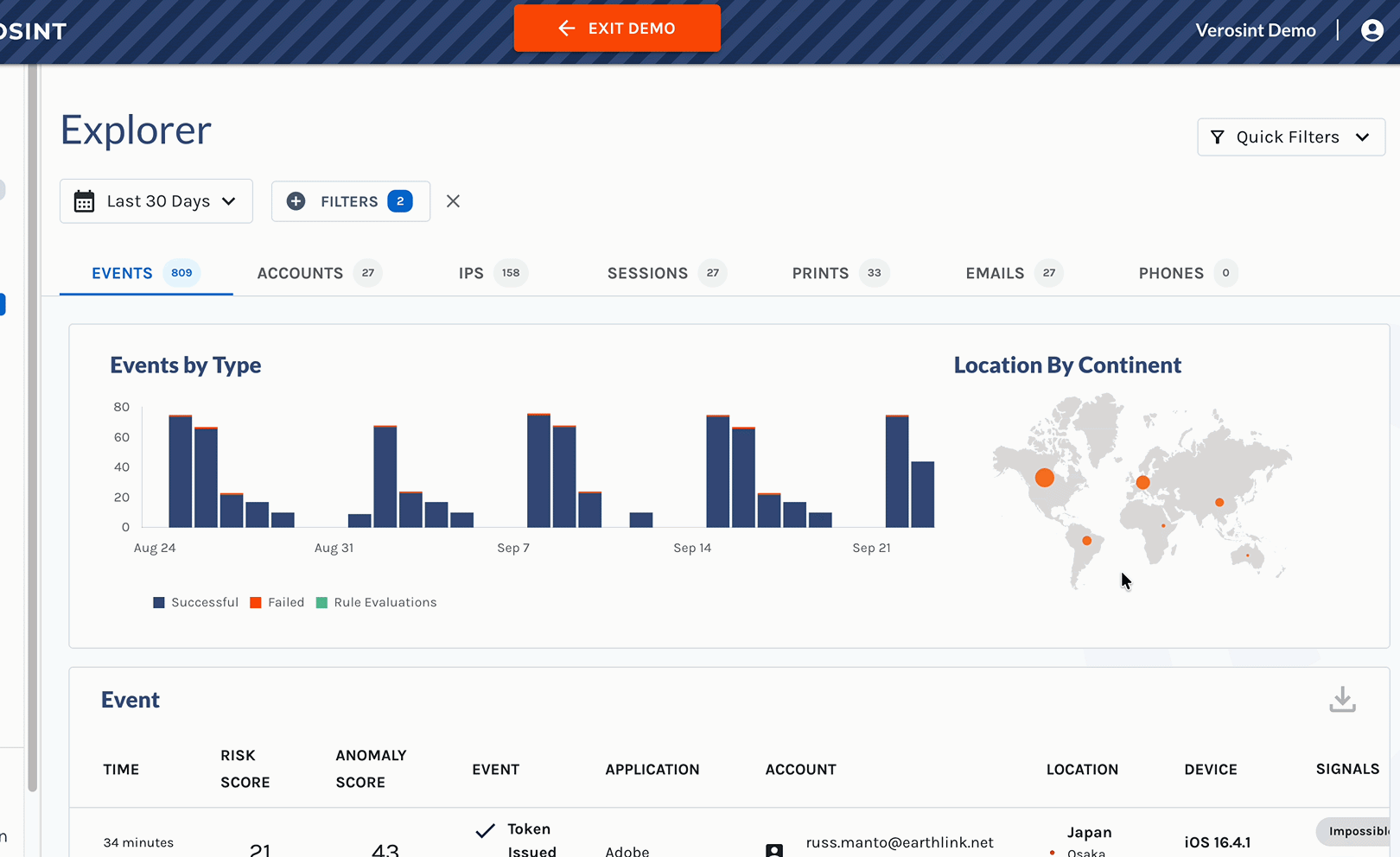
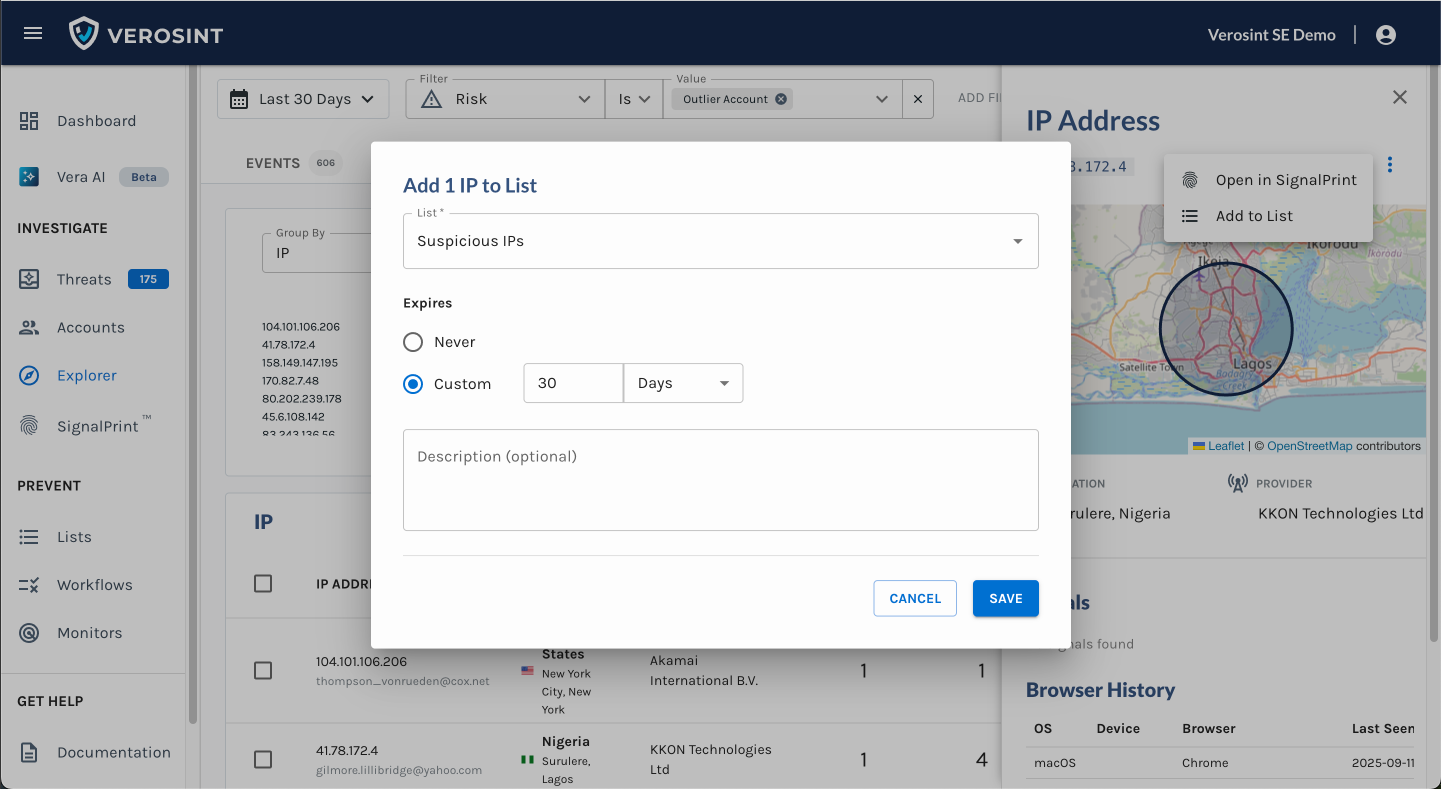
We’ve introduced a new Composite Score, designed to give you a faster and clearer view of an event’s overall risk profile. This score brings together both the Risk Score and Anomaly Score metrics into a single, easy-to-interpret value so you can quickly understand the riskiness of an event.
- View the Composite Score directly in Event Explorer
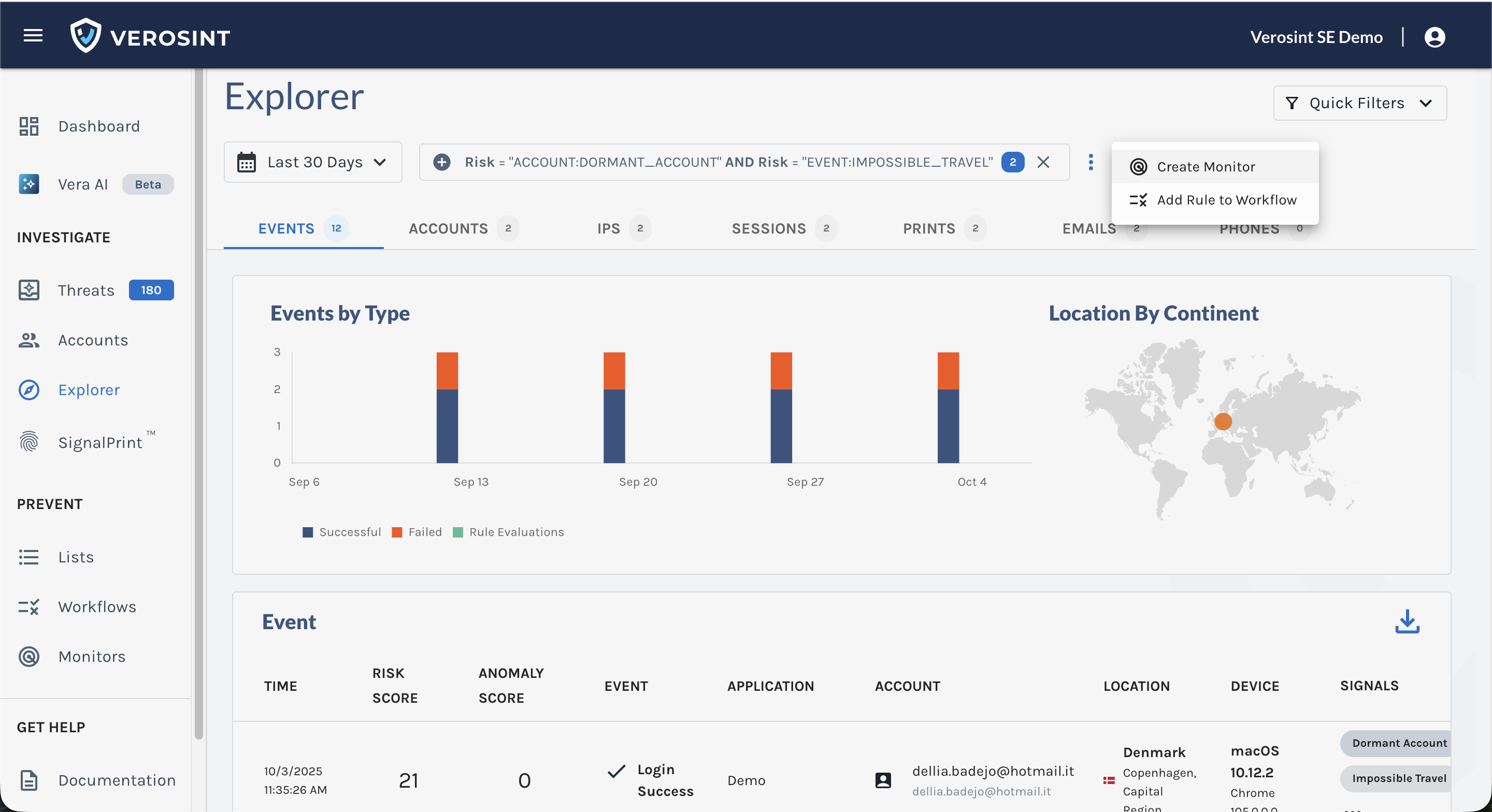
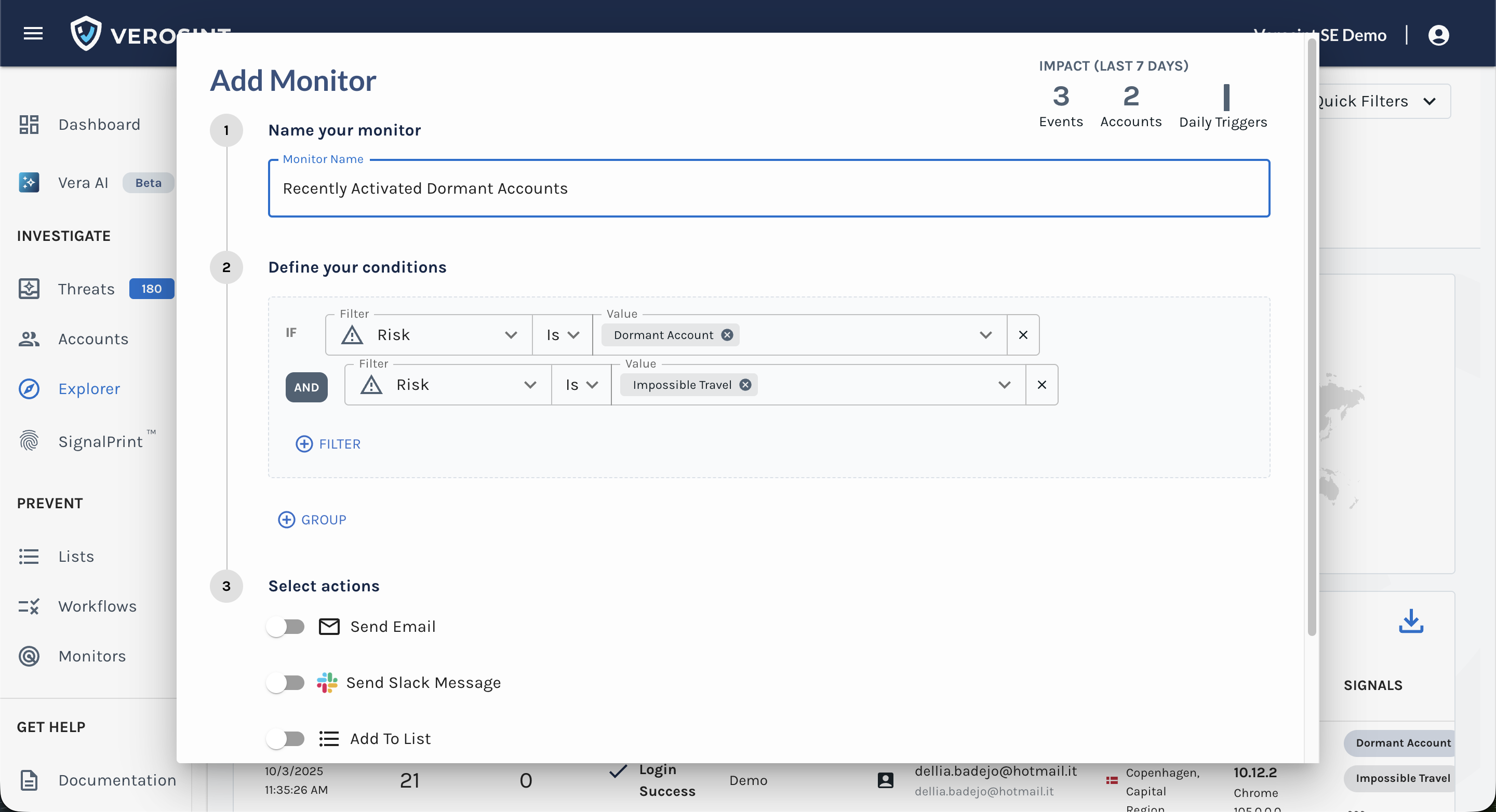
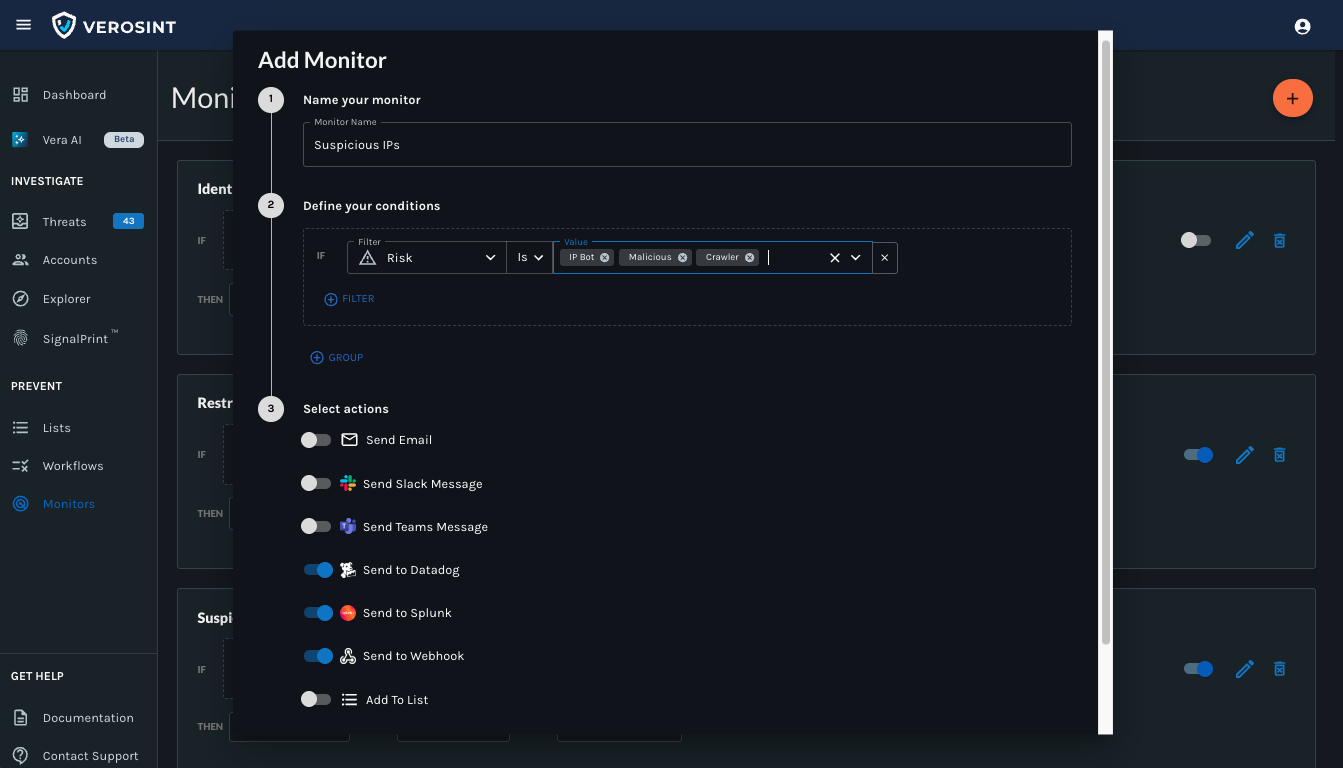
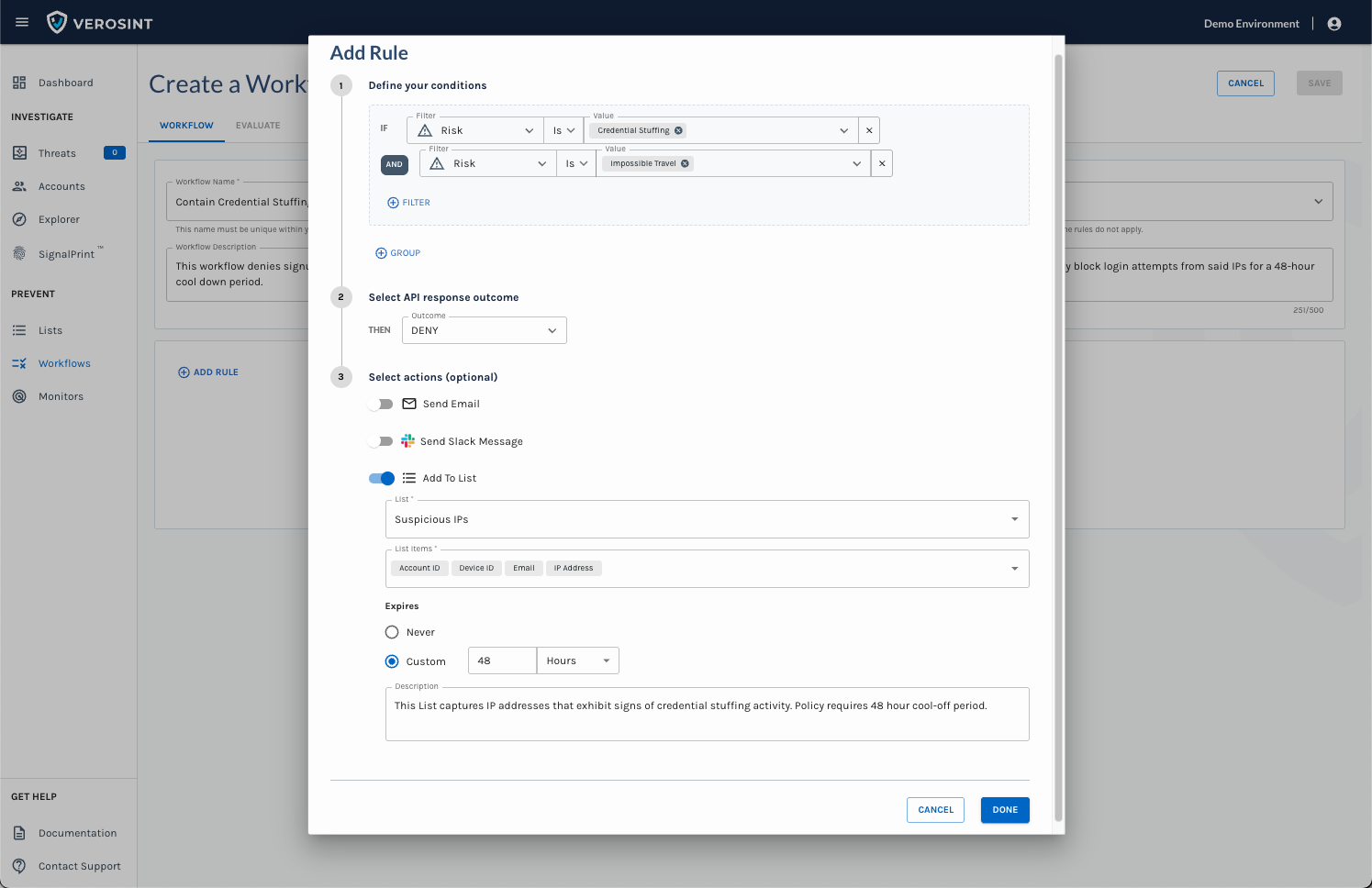
- Use the Composite Score in Rules and Monitors to automatically flag risky behavior
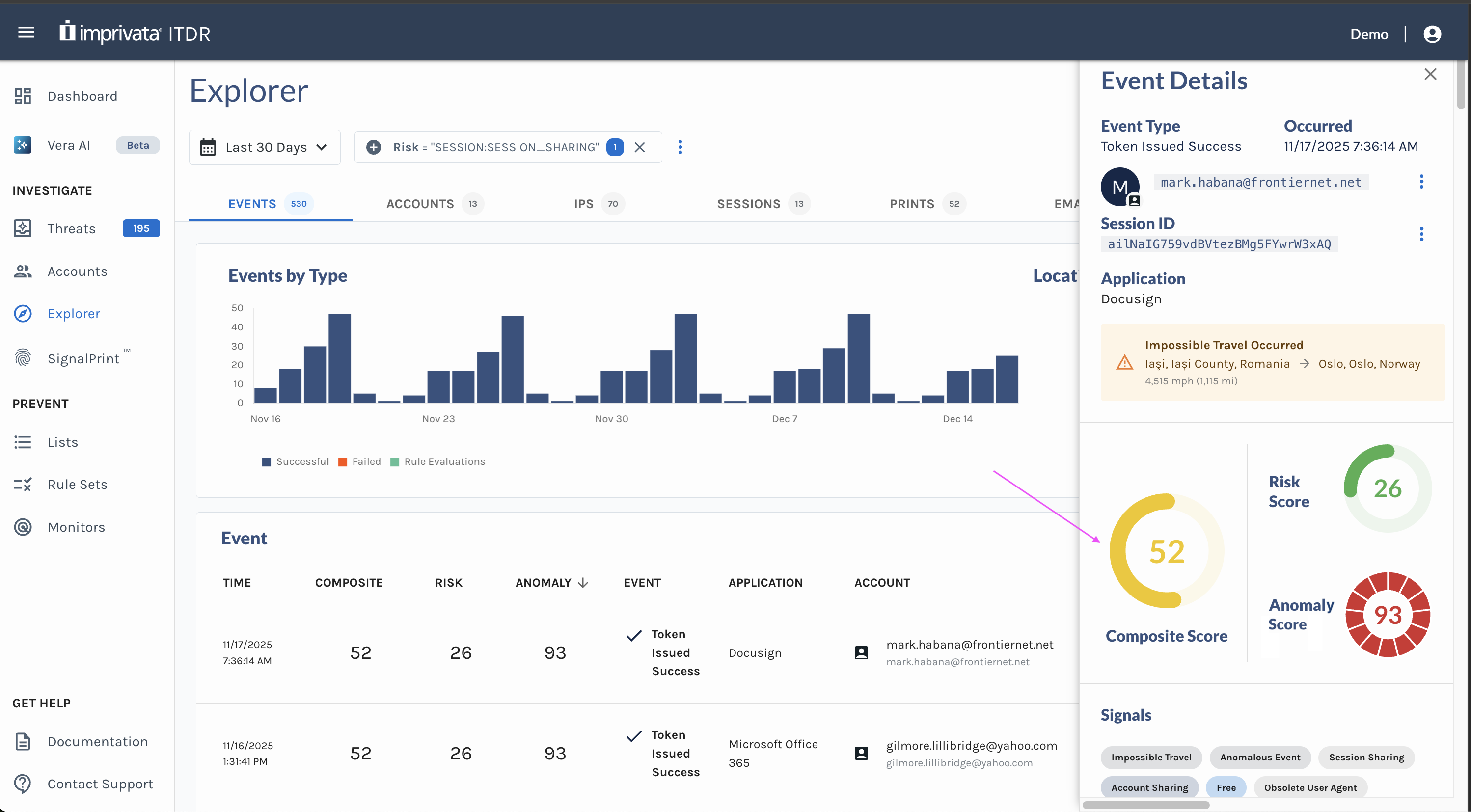
Composite Score in the Event Explorer
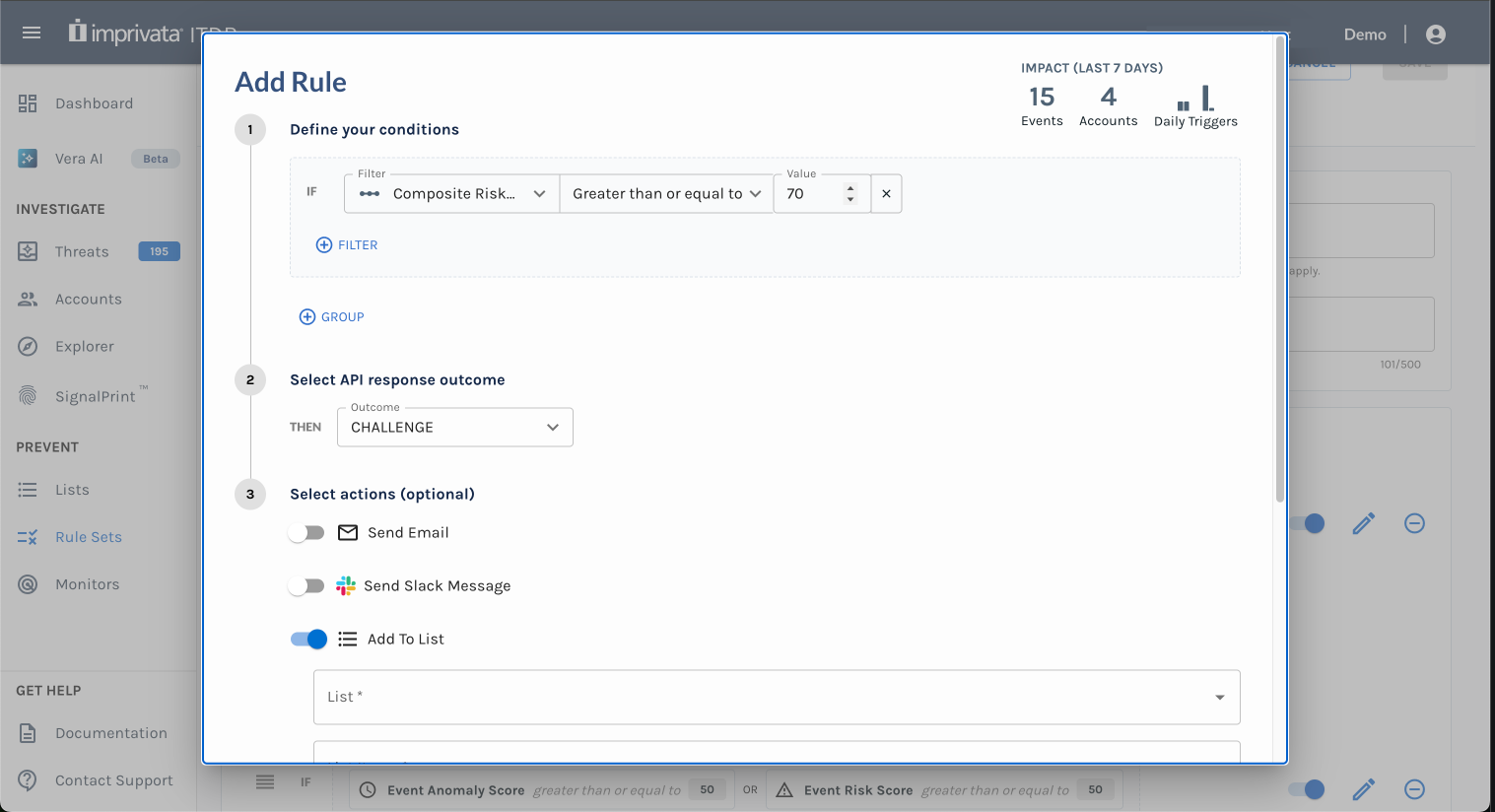
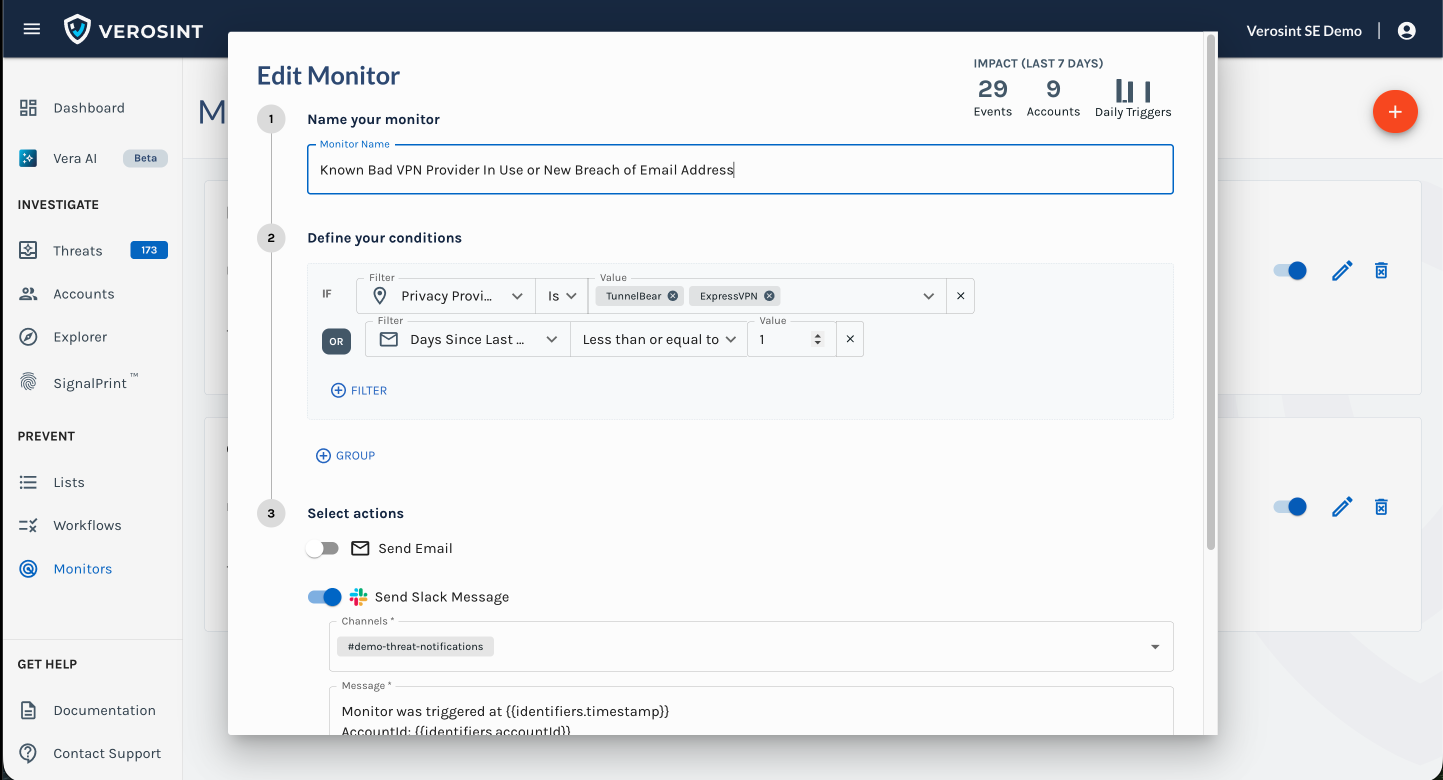
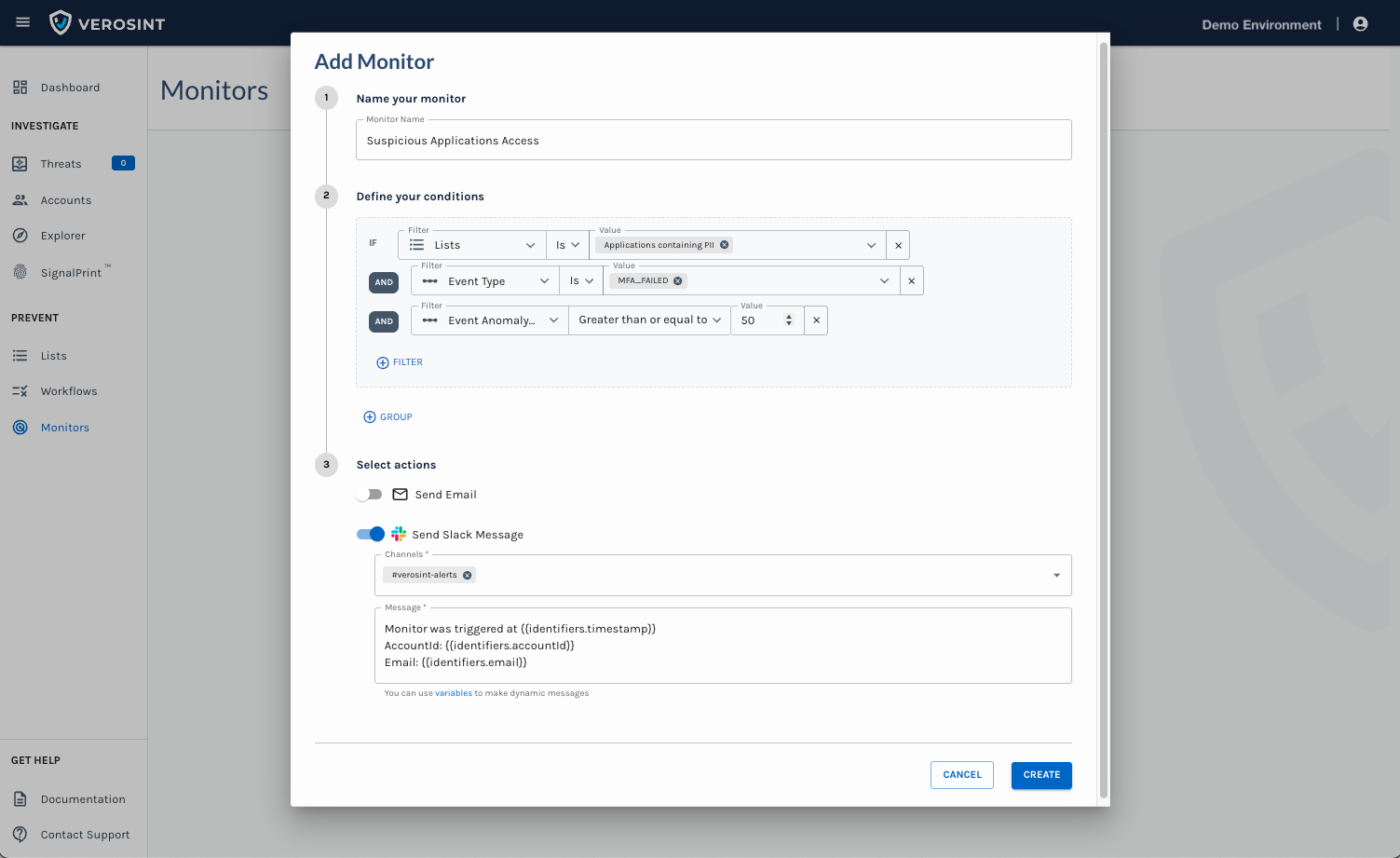
Use the Composite Risk Score in Rules
Why Does This Matter?
With the Composite Risk Score, you can:
- Identify high-risk events at a glance in Event Explorer
- Streamline how your team responds by reducing the time spent interpreting separate signals
- Flag risky behavior automatically when using Rule Sets or Monitors
Check it out now to enhance your monitoring and response efficiency.