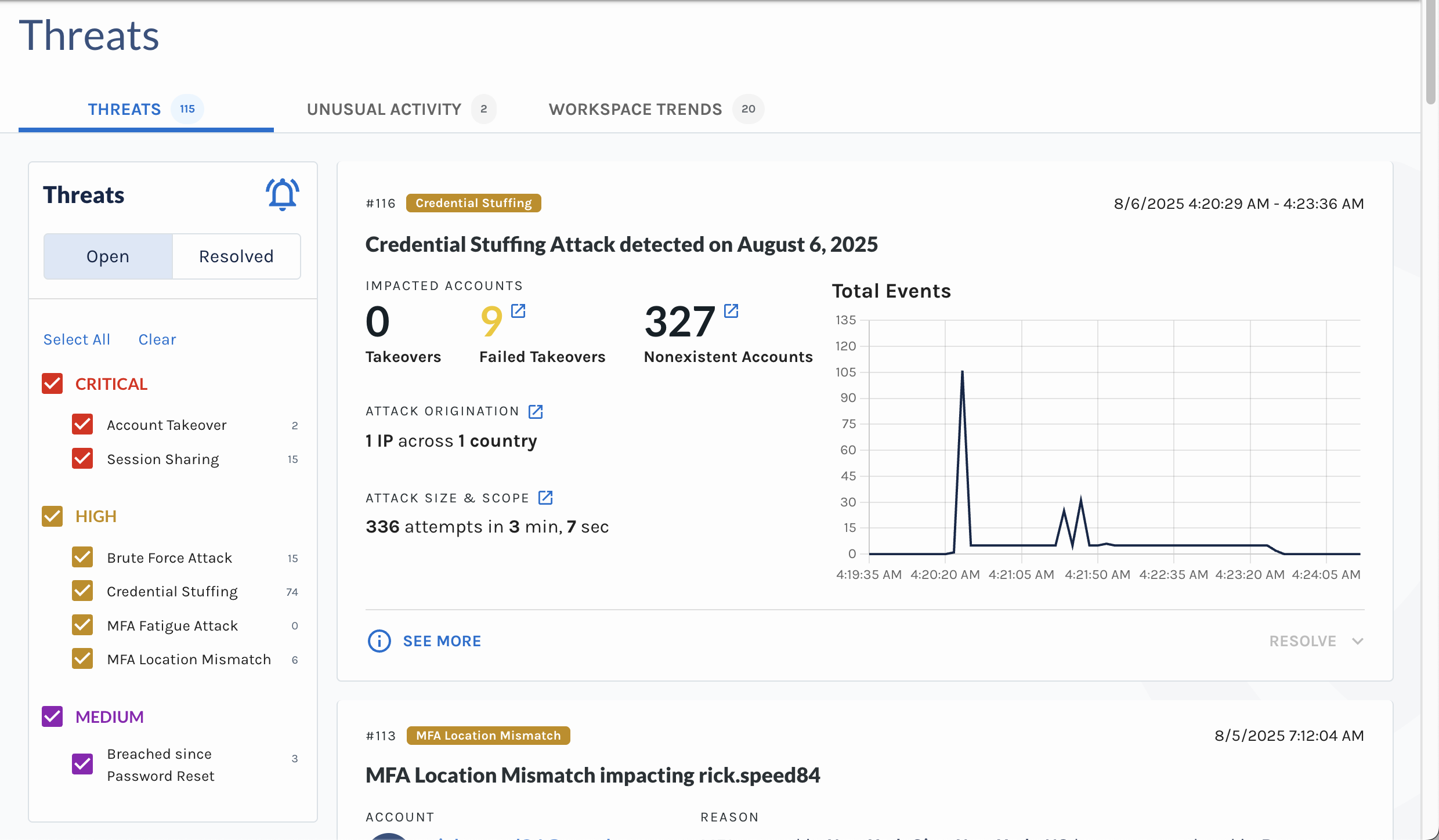
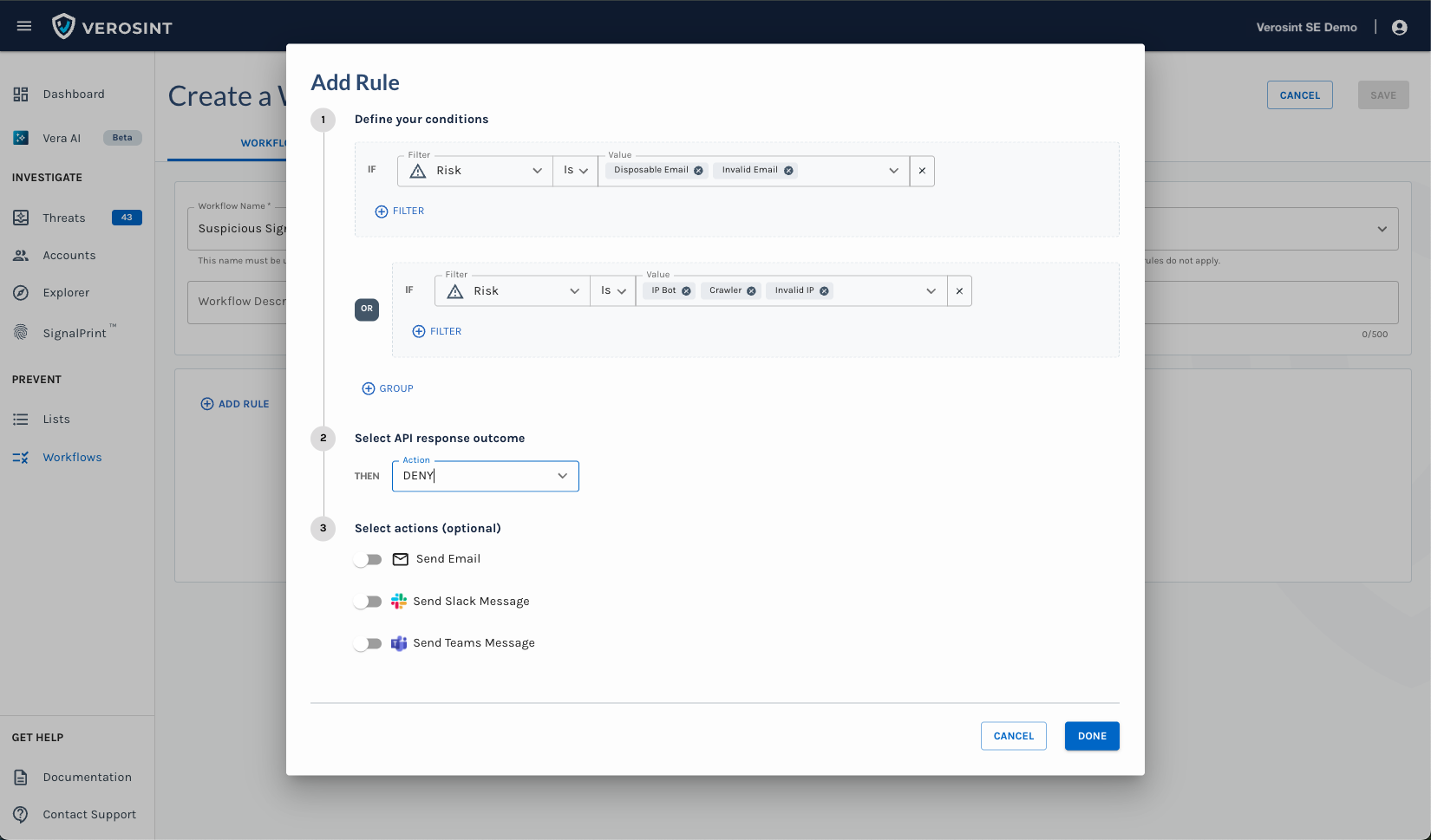
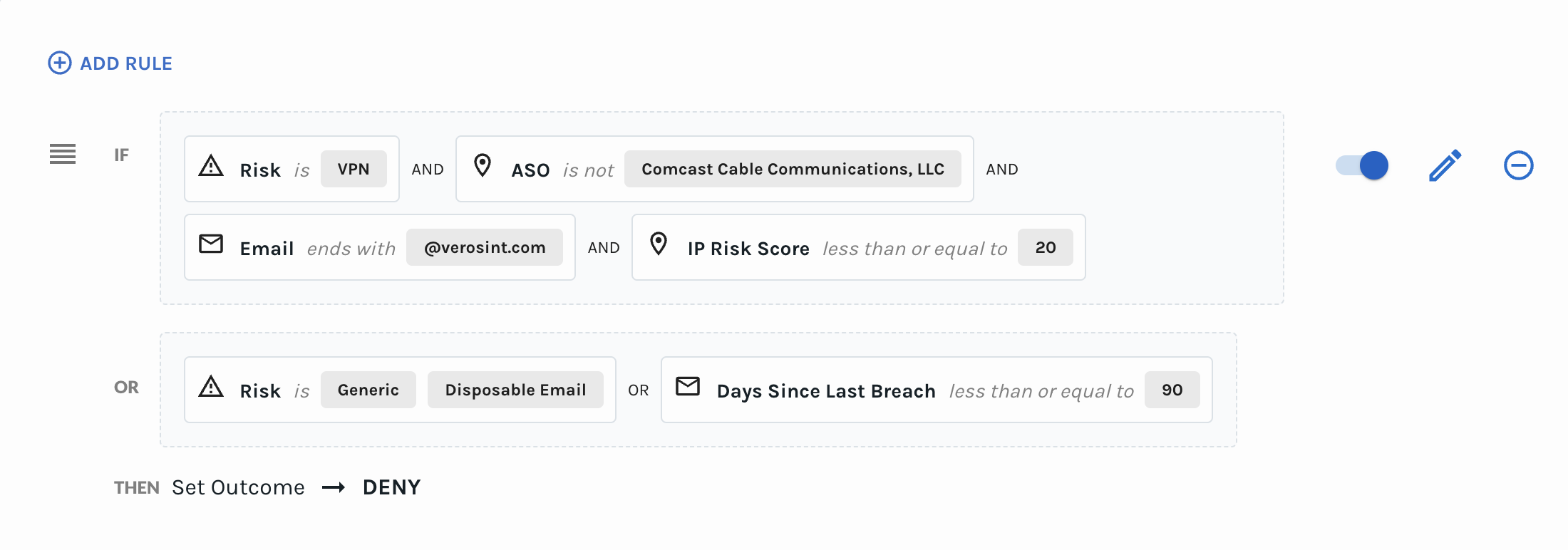
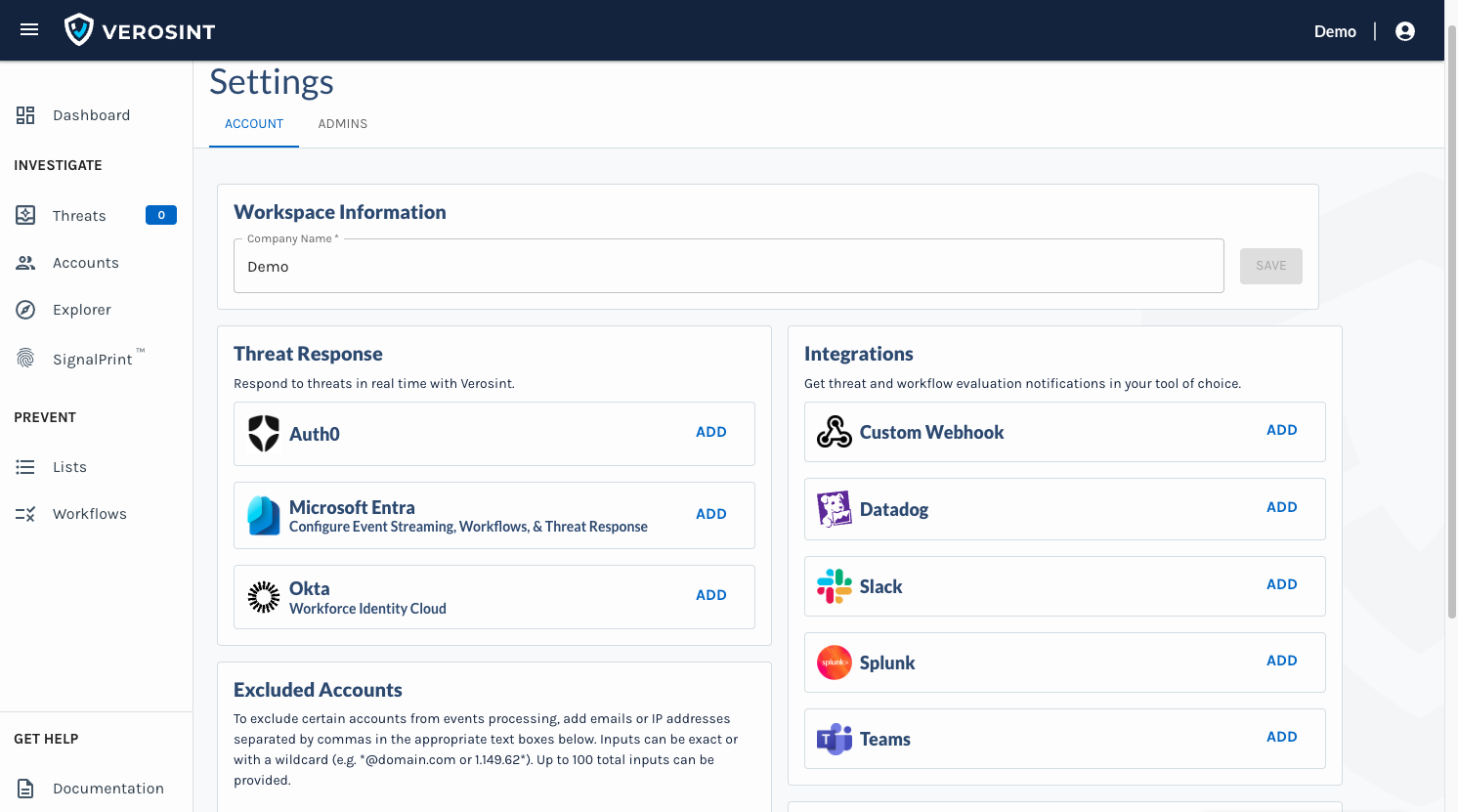
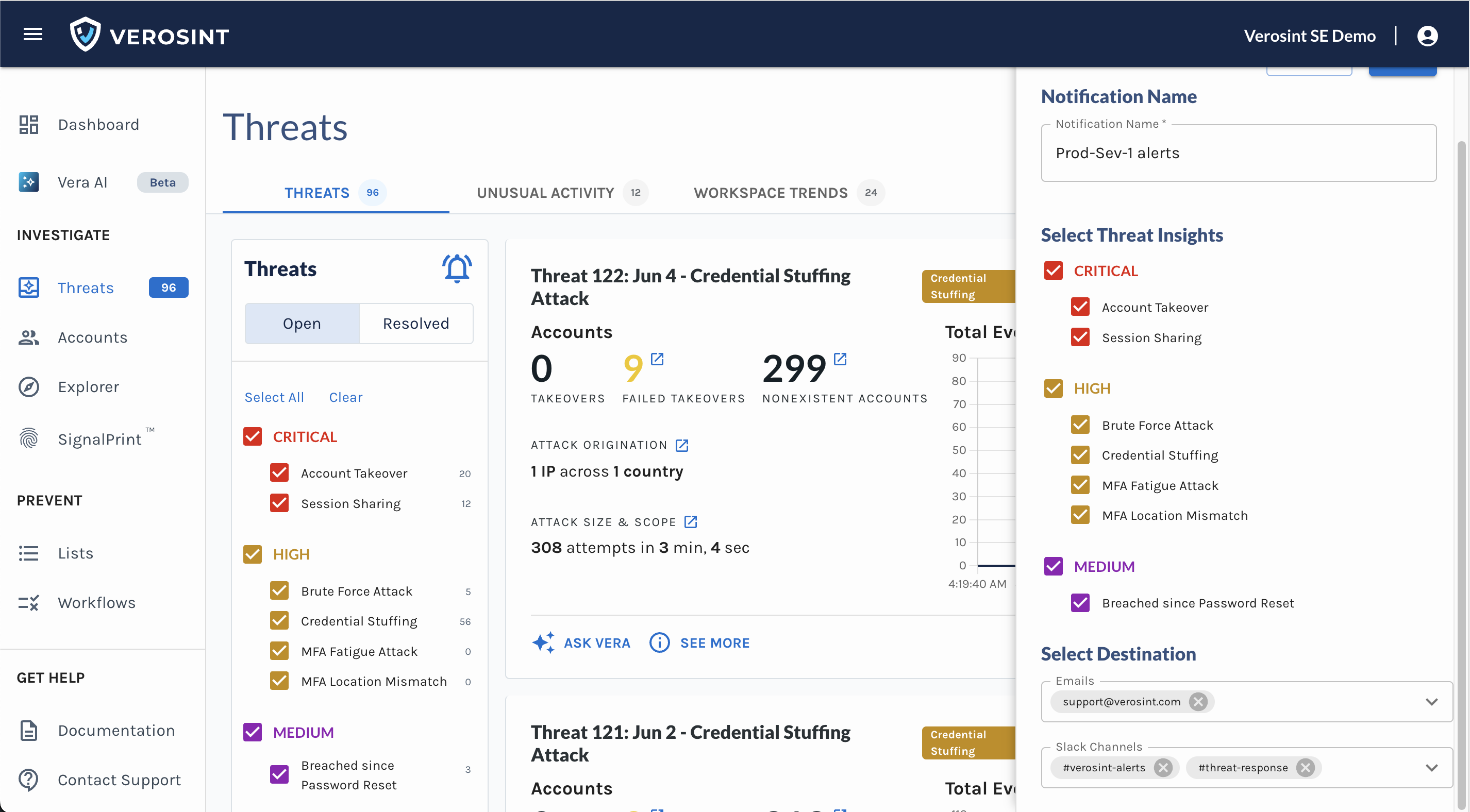
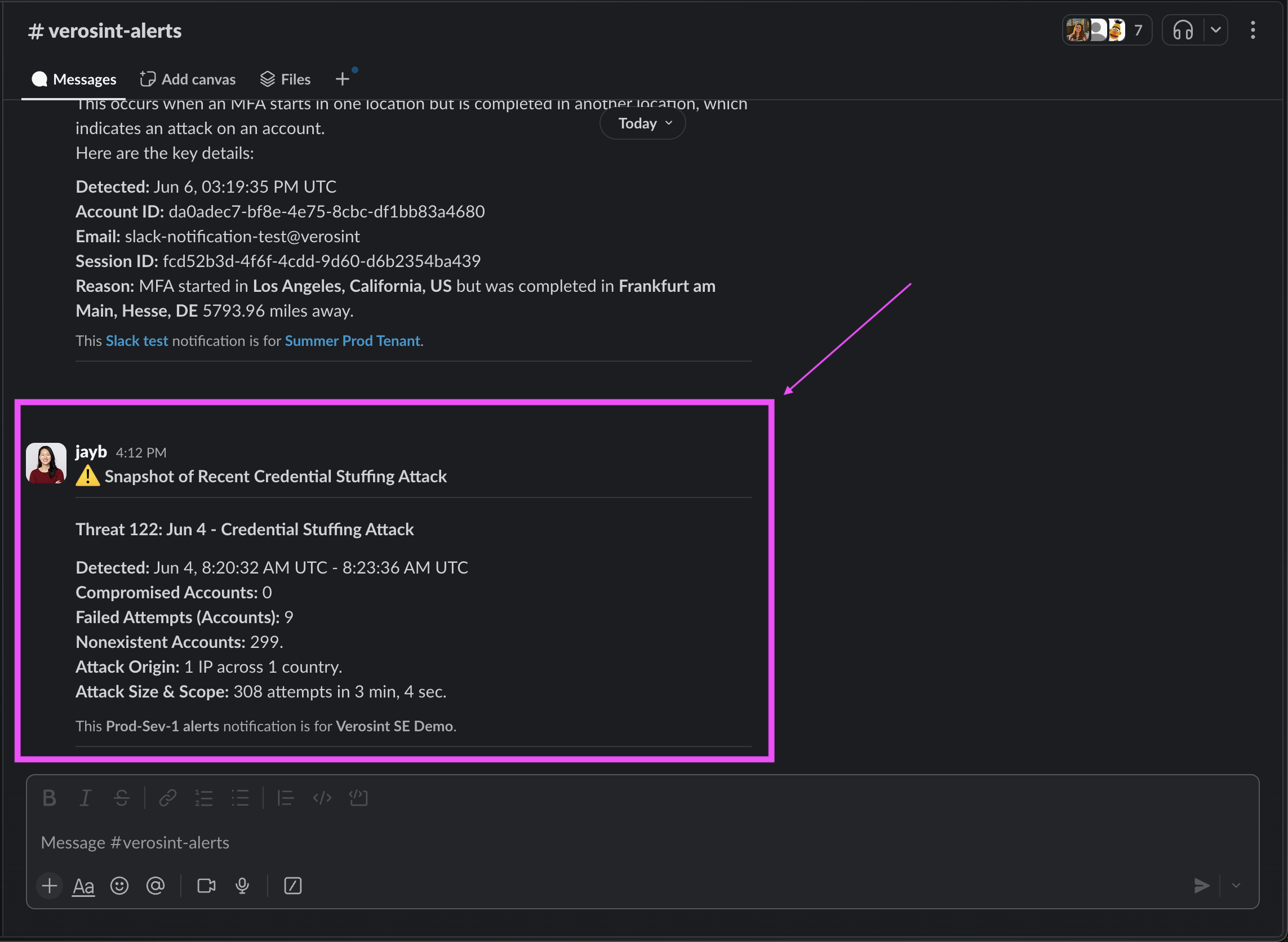
🌟 New Feature Alert 🌟
Verosint now allows admins to create and manage API keys directly in the workspace, making it easier to rotate keys and maintain security best practices.
What's New?
-
Create API Keys: Admins can create and name up to 10 active API keys per workspace.
-
Revoke API Keys: Admins can revoke keys at any time. Deactivated keys are timestamped in the Deactivated column.
-
Role-Based Access: Role-based access puts API key management in the right hands—protecting security while empowering the right teams to move faster.
- Admins: Create, revoke, and view keys.
- Analysts: View and copy keys.
- Read-only users: Cannot access the API Keys page.
-
Sorting the API Key Table: Sort your API keys by Name, Created Date, or Deactivated Date for easier management.
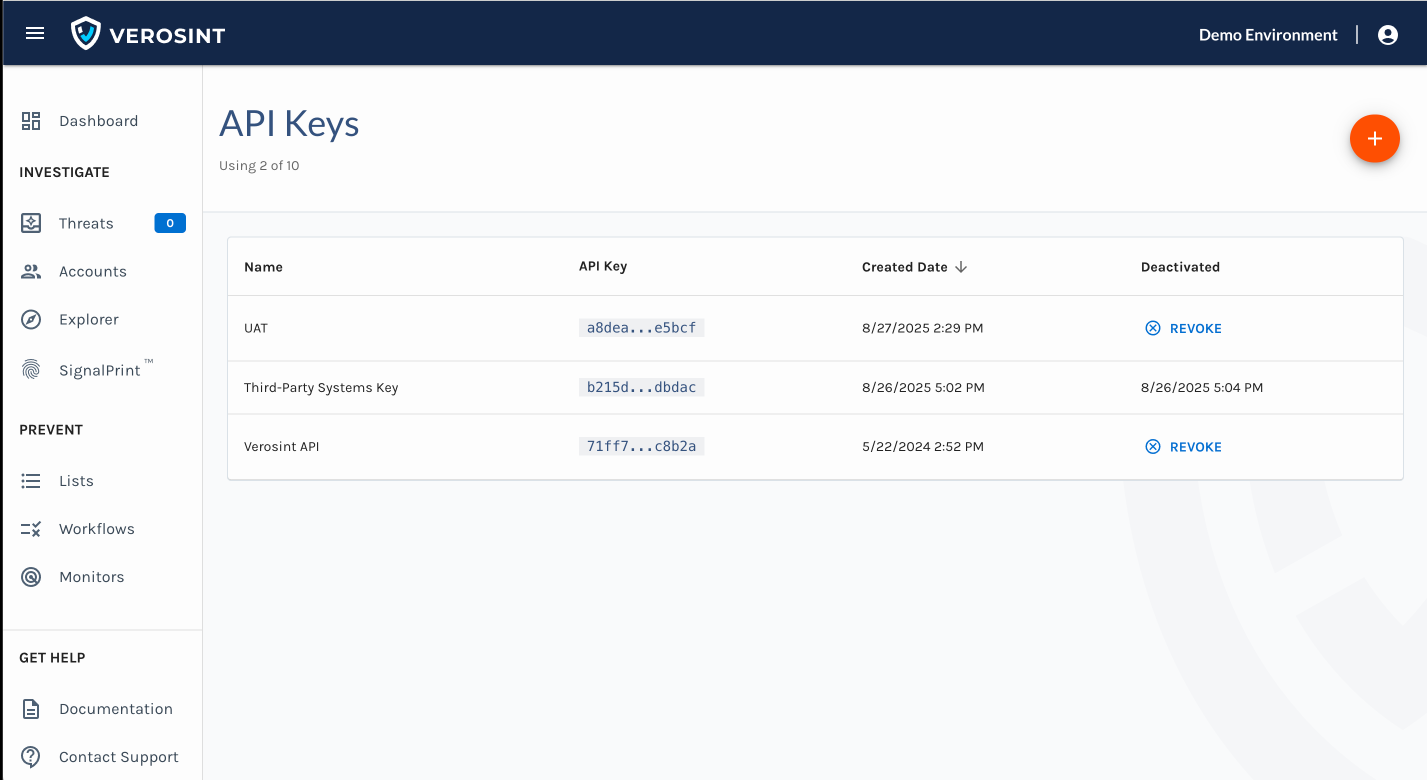
Why Does This Matter?
- 🔐Security: Easily rotate API keys to follow best practices.
- ⚙️Control: Admins maintain full control over API keys, while analysts can access keys needed for workflows.
- 👁️Transparency: Clear visibility into when keys are created or deactivated, reducing risk of unauthorized access.