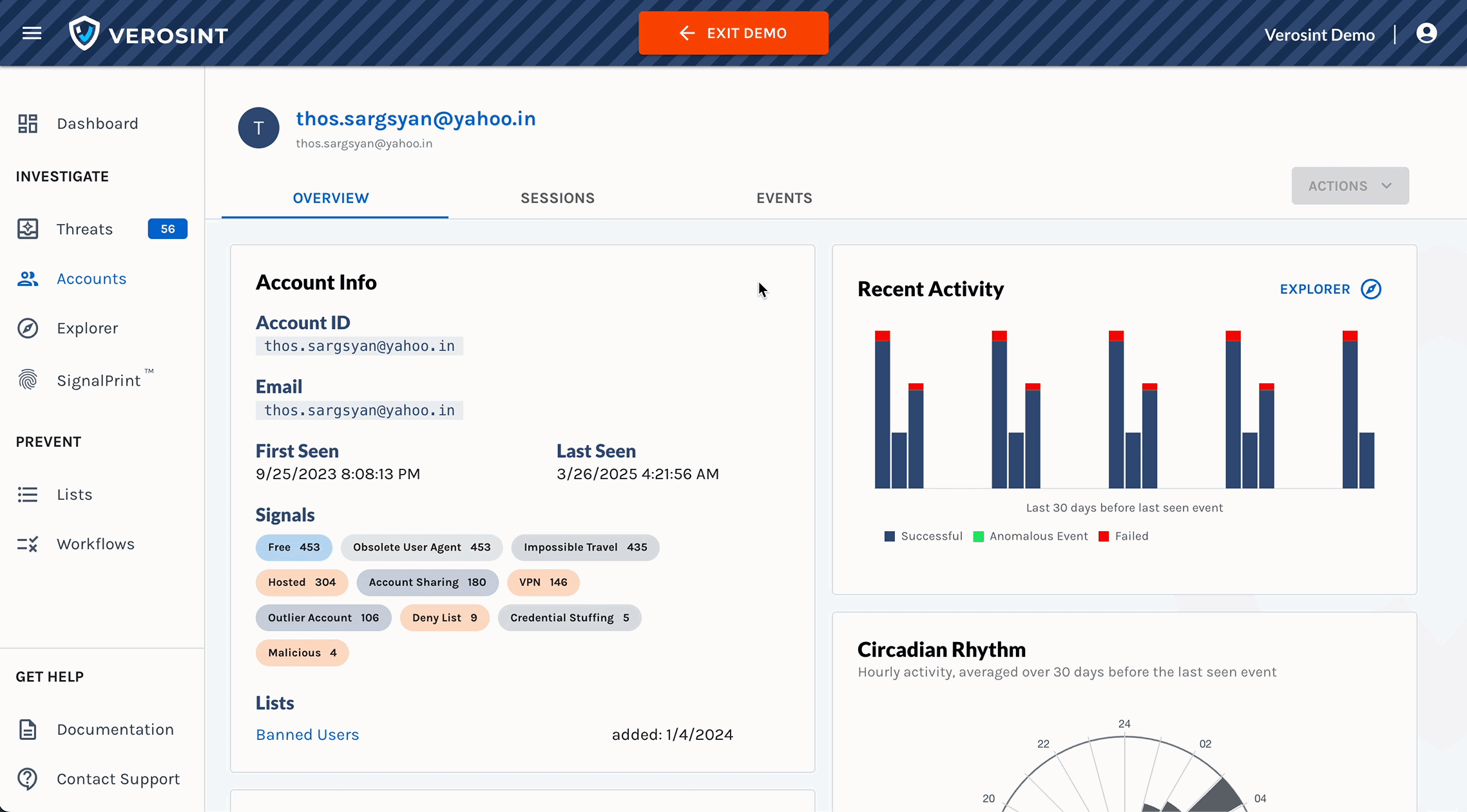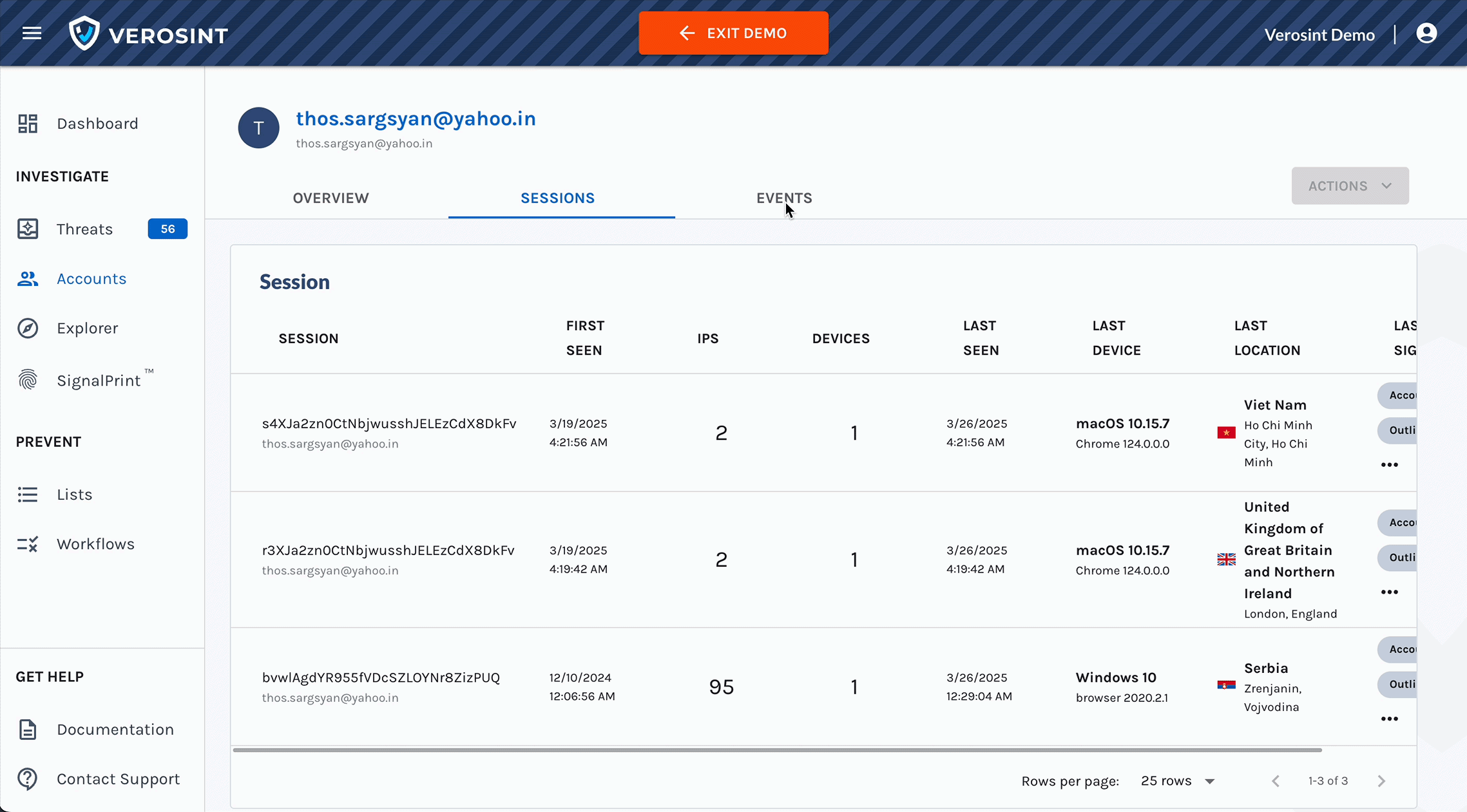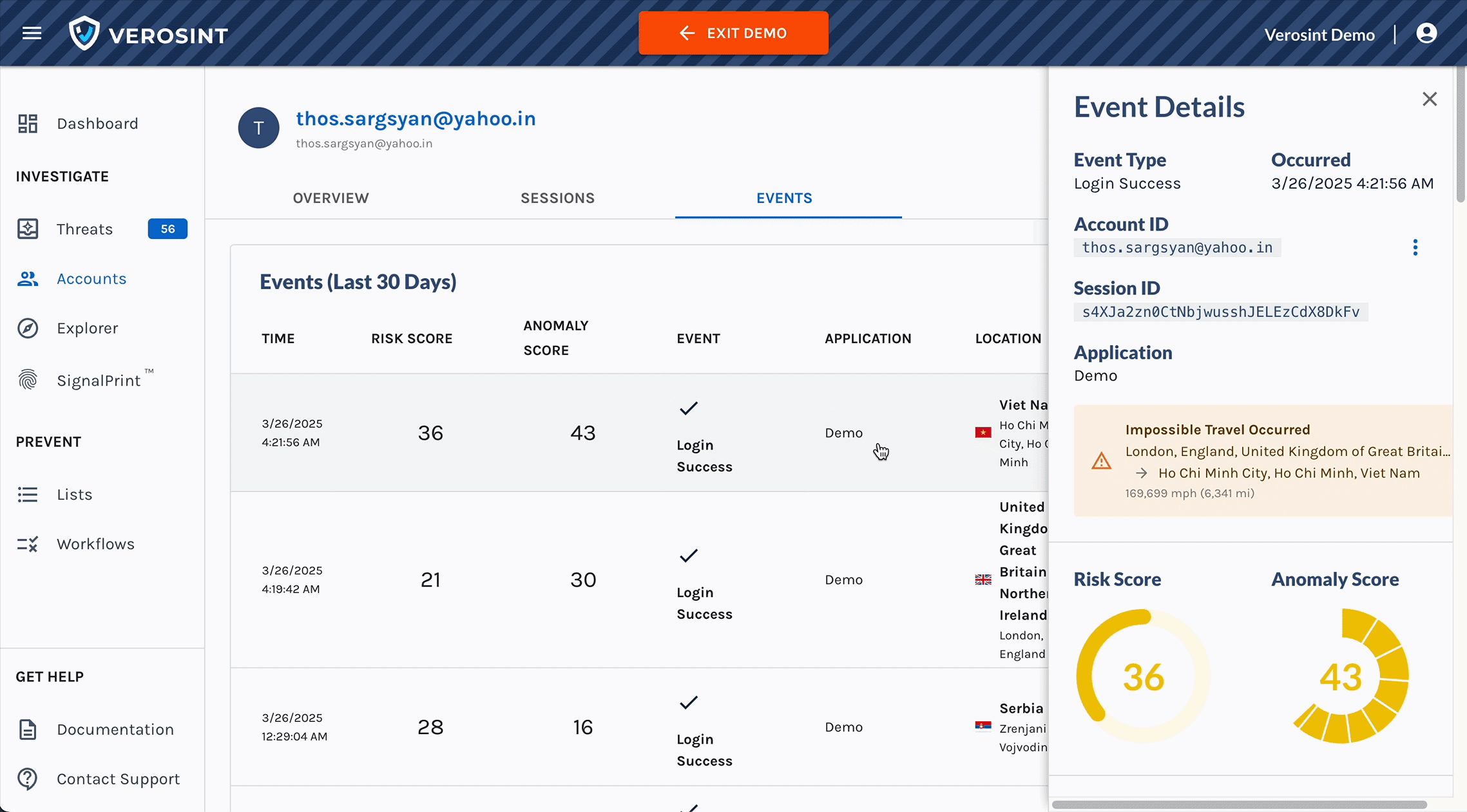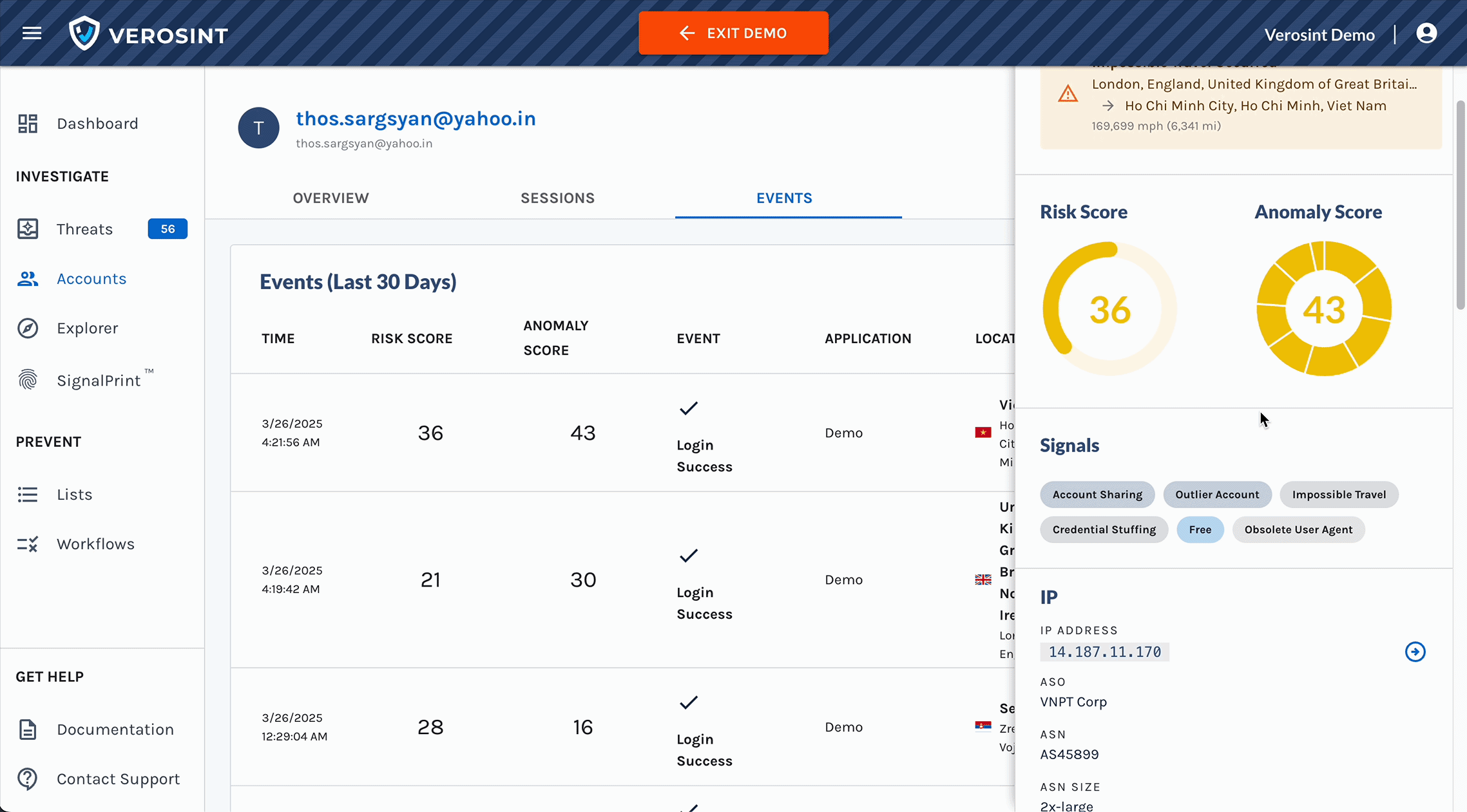
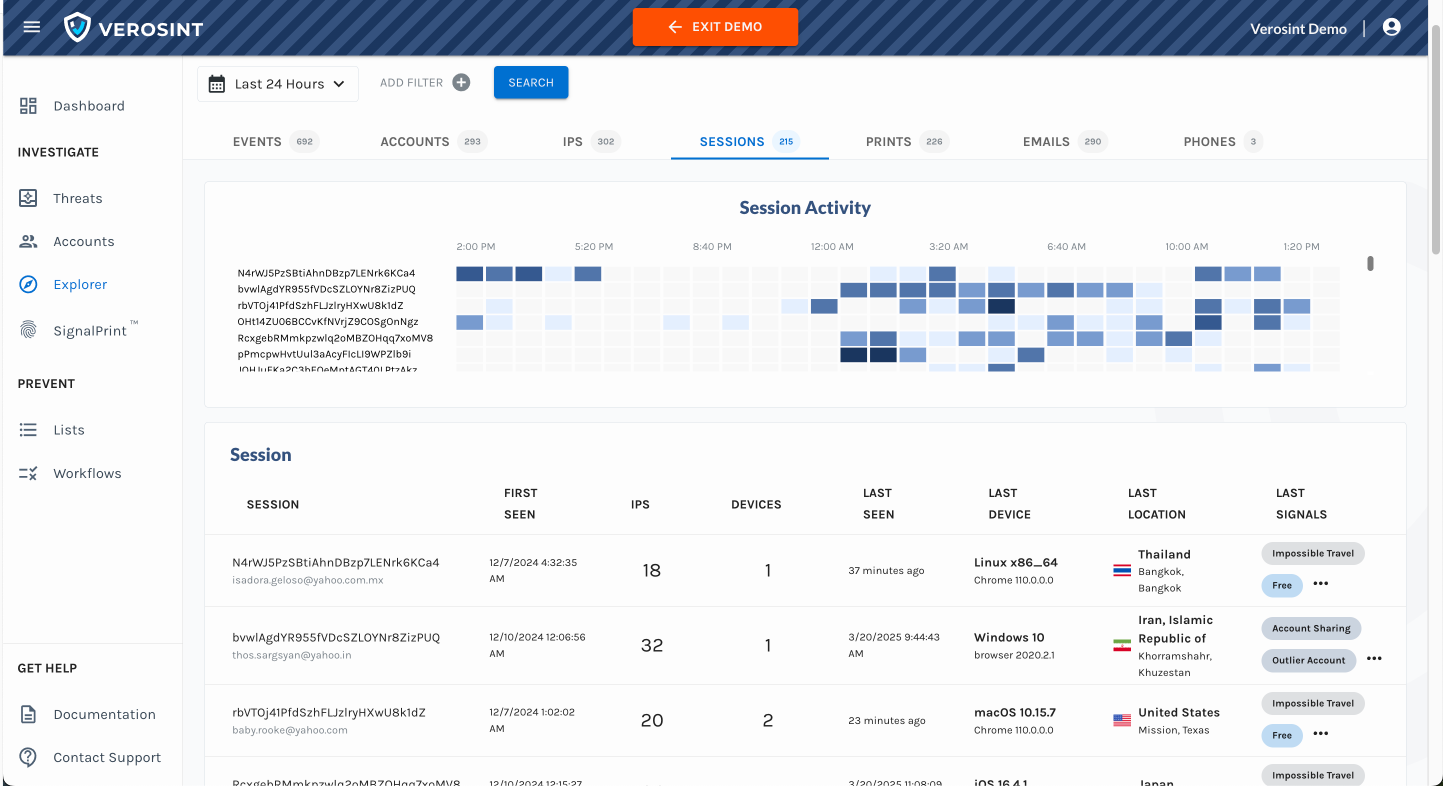
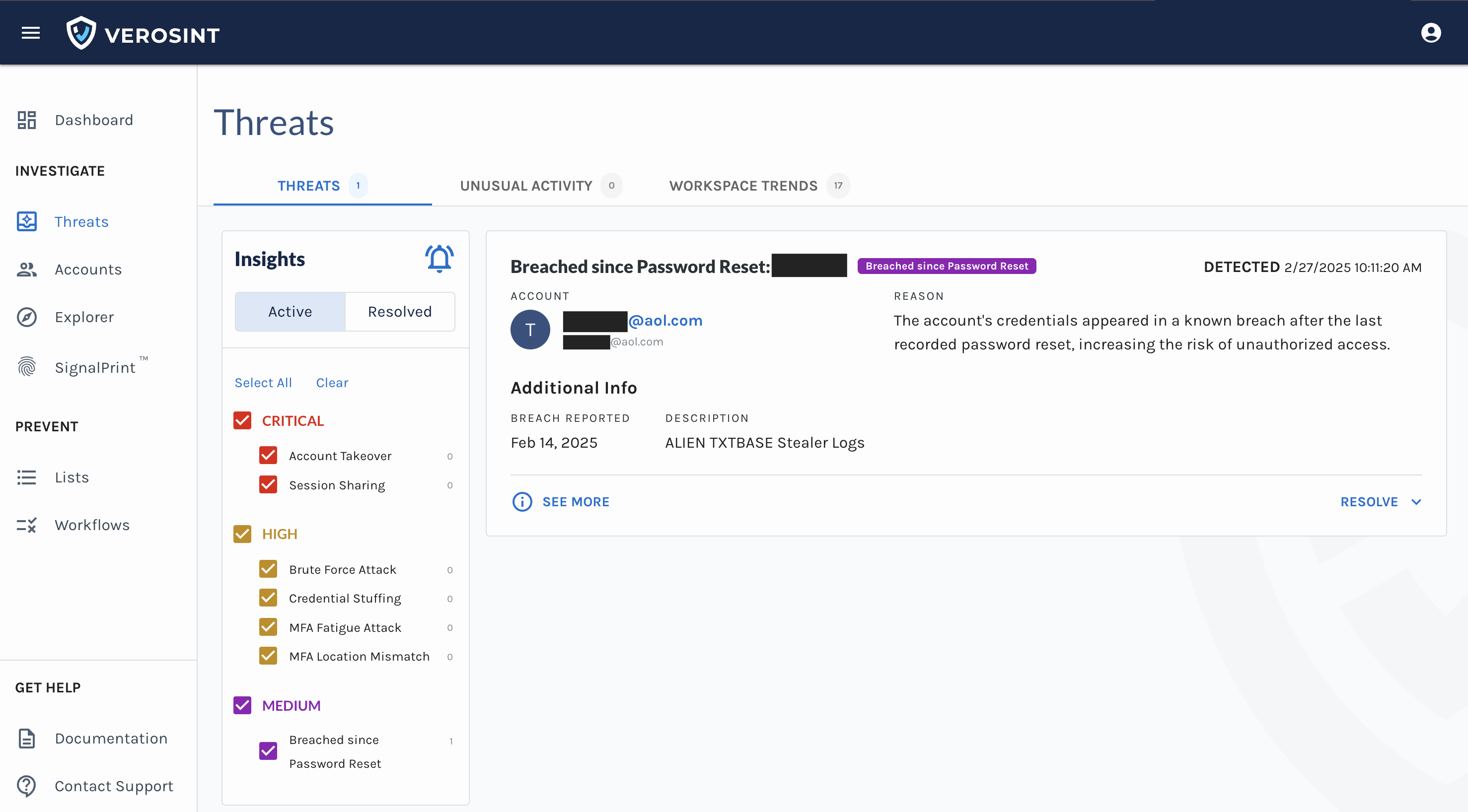
Meet Vera, the first agentic AI security analyst purpose-built for Identity Threat Detection and Response.
Vera is now available in beta through our early access program.
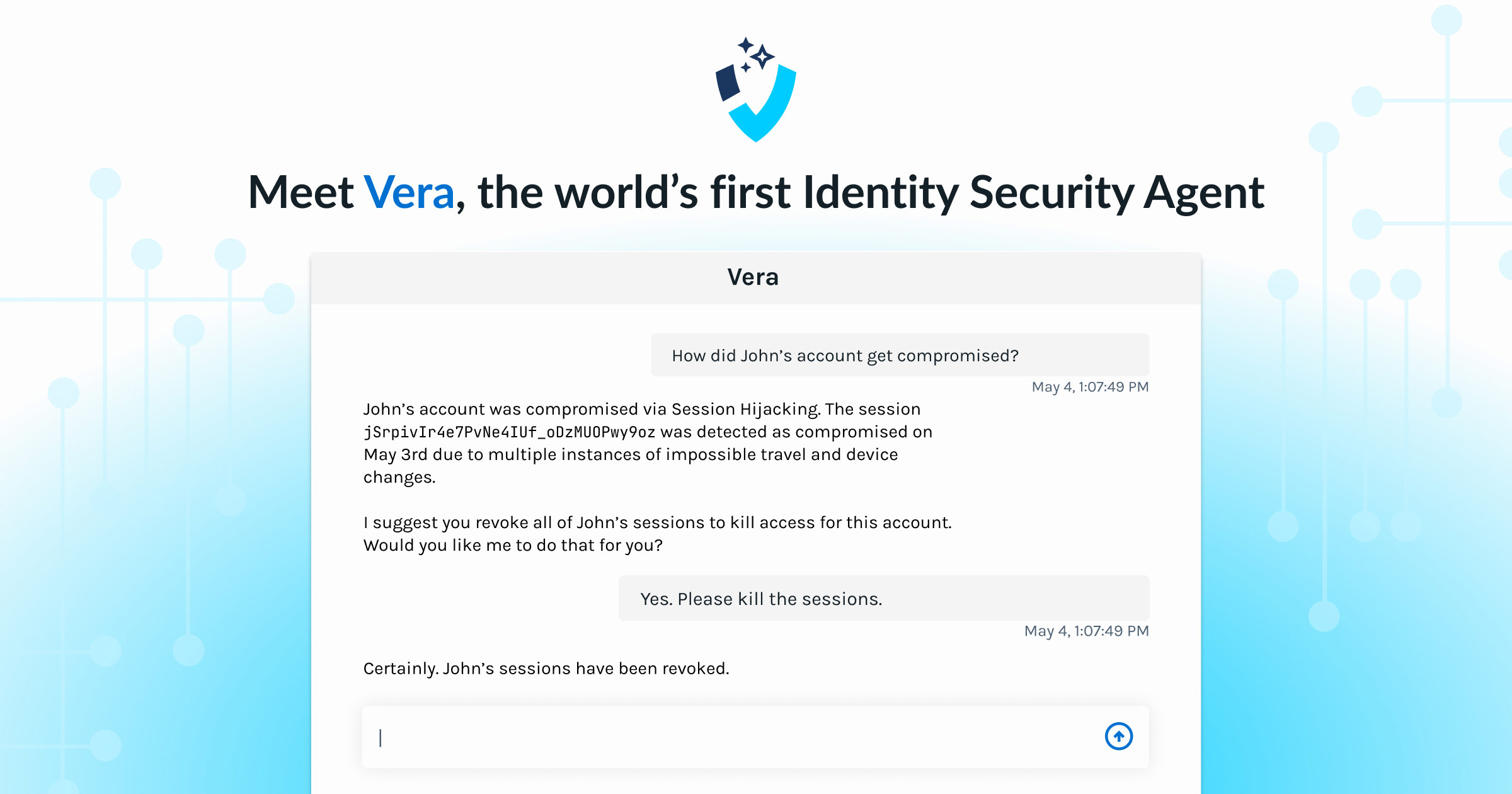
Vera is an agentic AI security analyst that:
- Understands your environment and user behavior
- Detects and triages threats in real time
- Acts directly inside your collaboration tools (Slack, Teams)
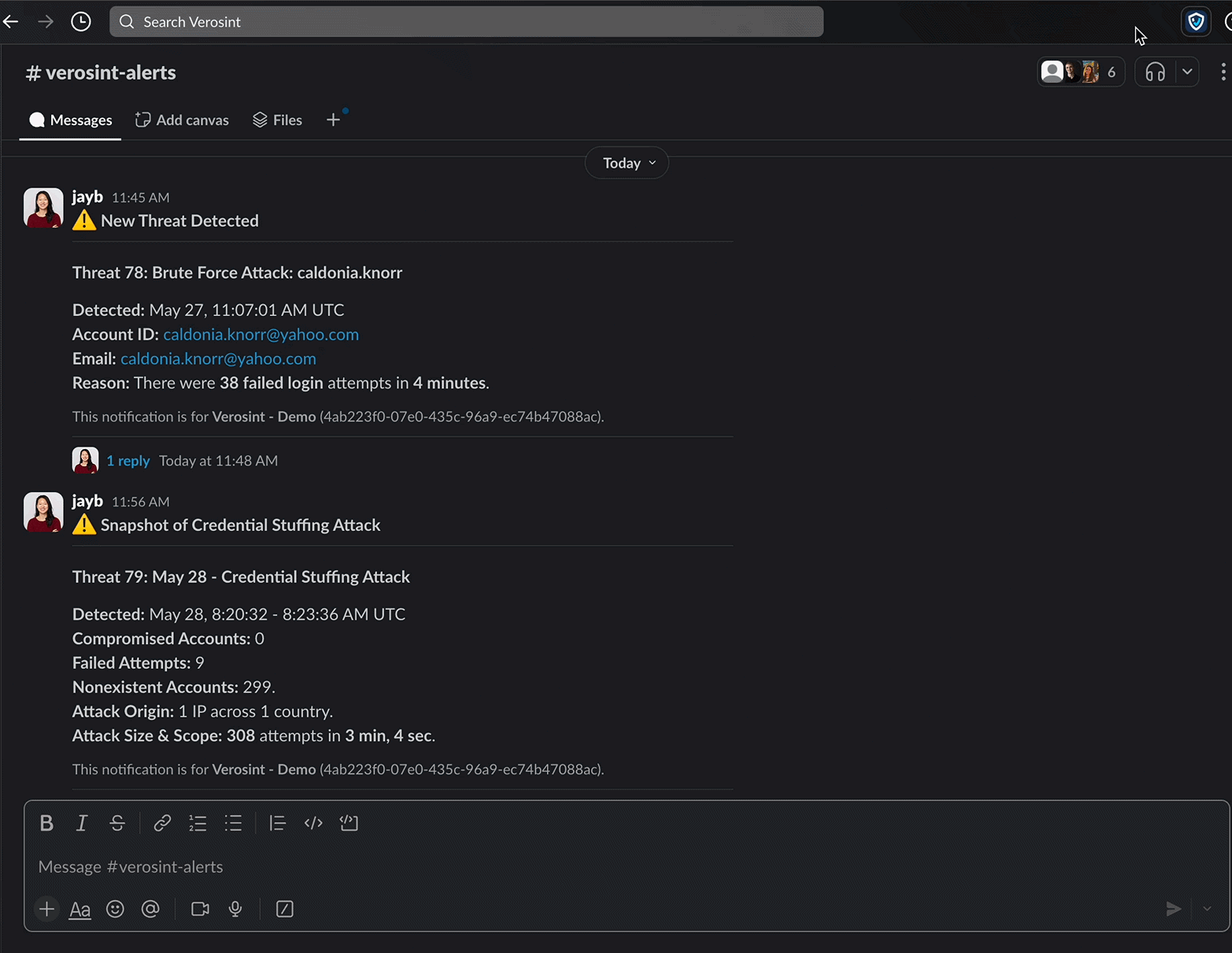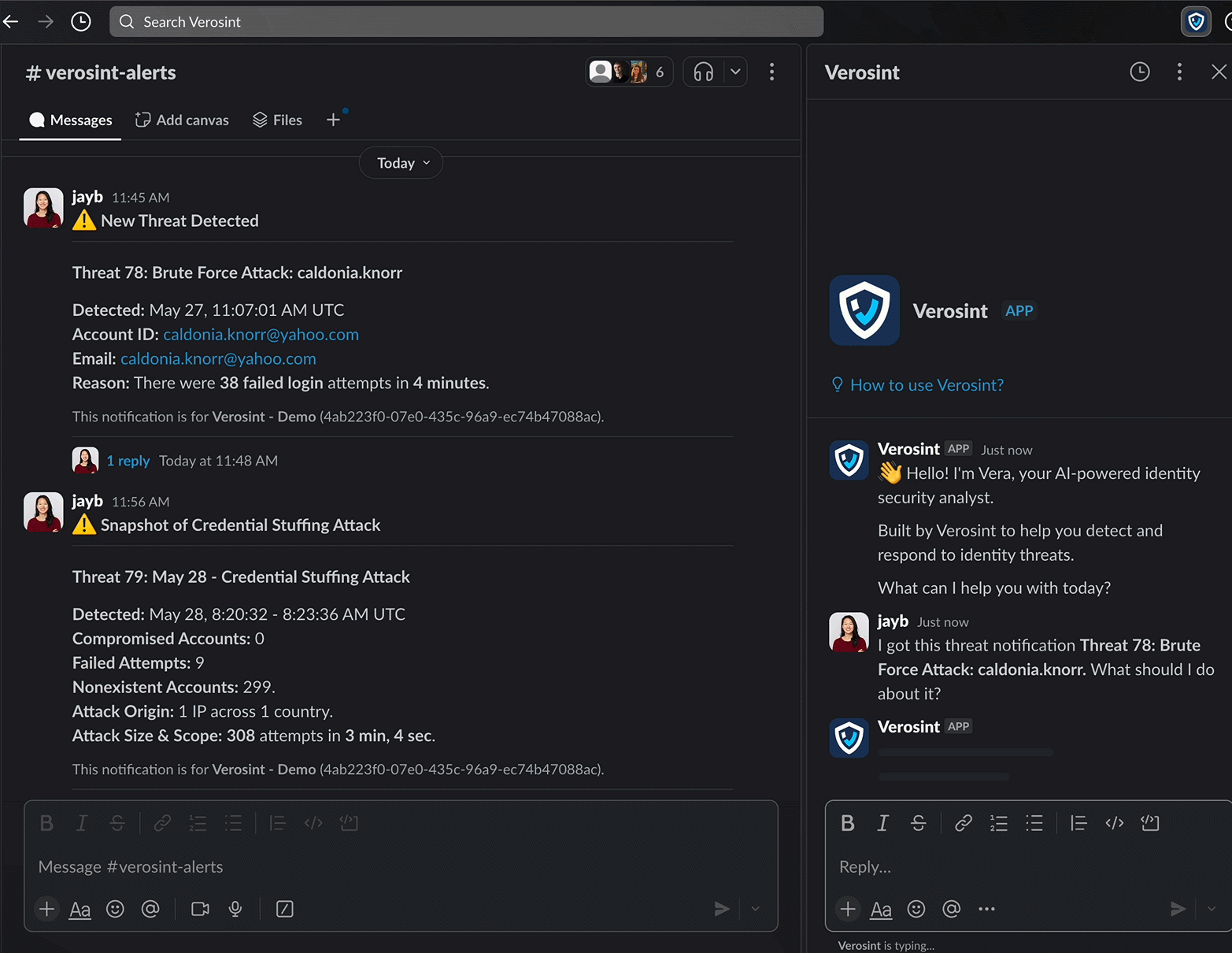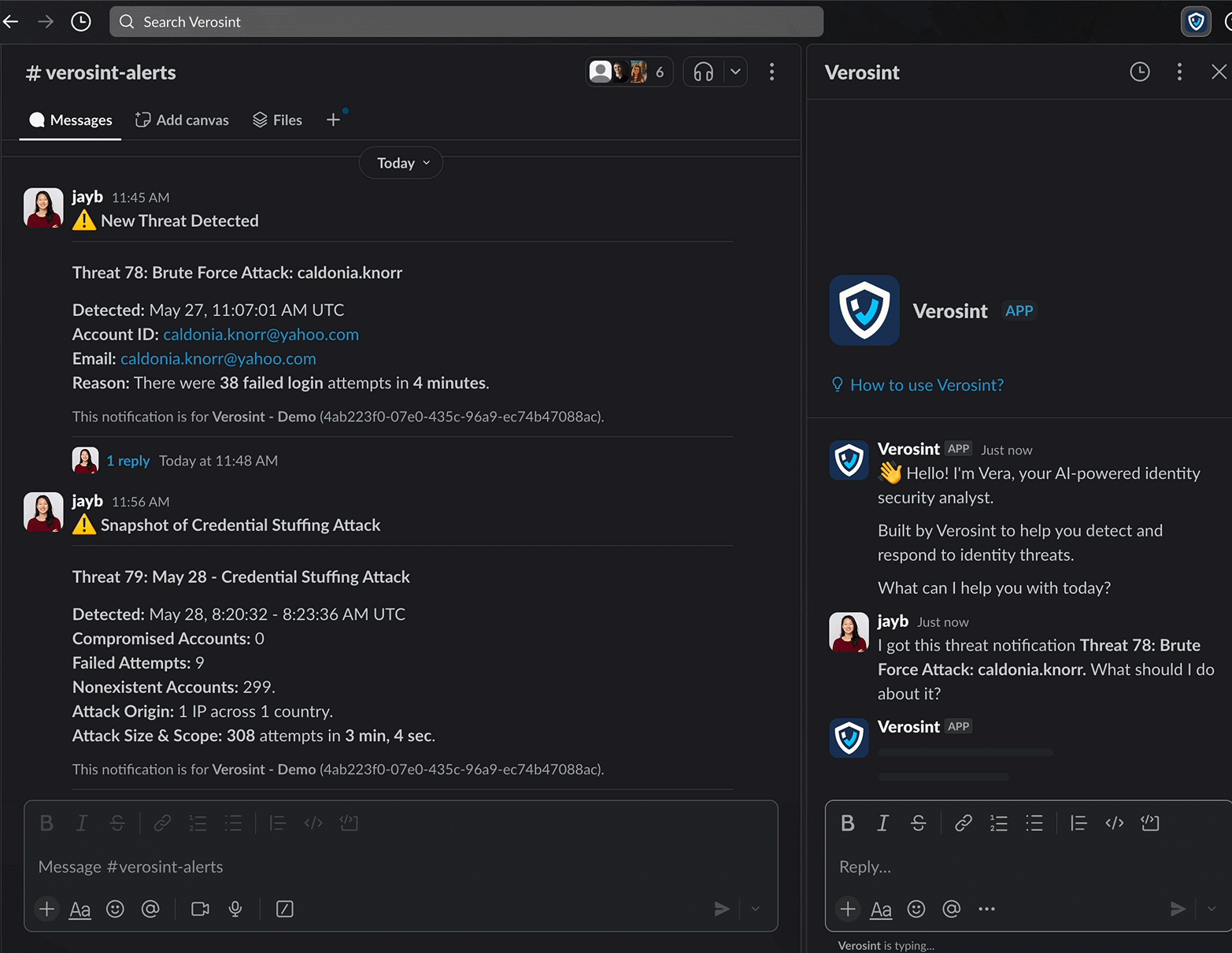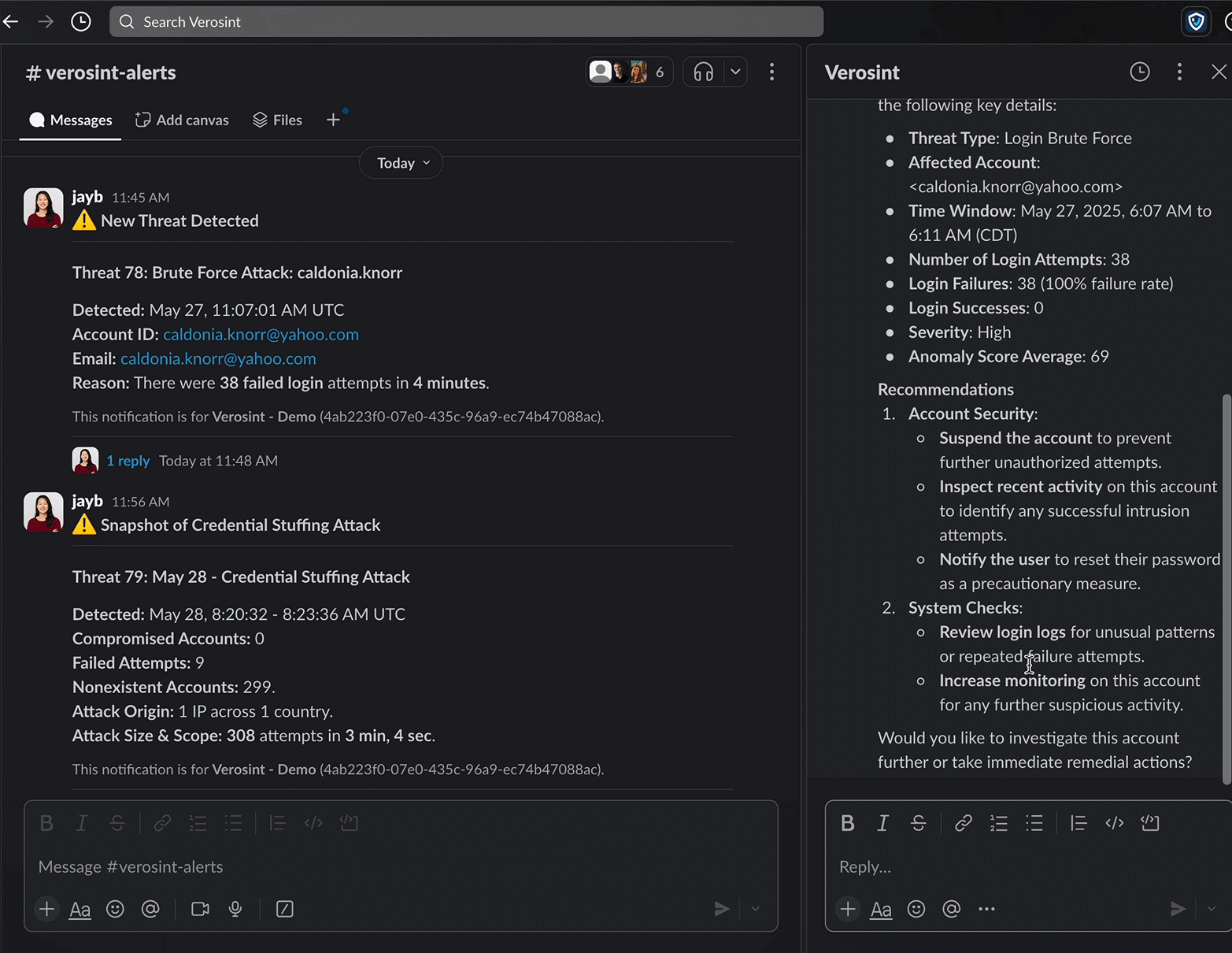
- Investigates and recommends appropriate actions
- Learns from each interaction and builds automated response playbooks
Vera is fast, contextual, and precise. And most importantly — Vera is useful and designed to improve your productivity and security from the minute you turn her on.
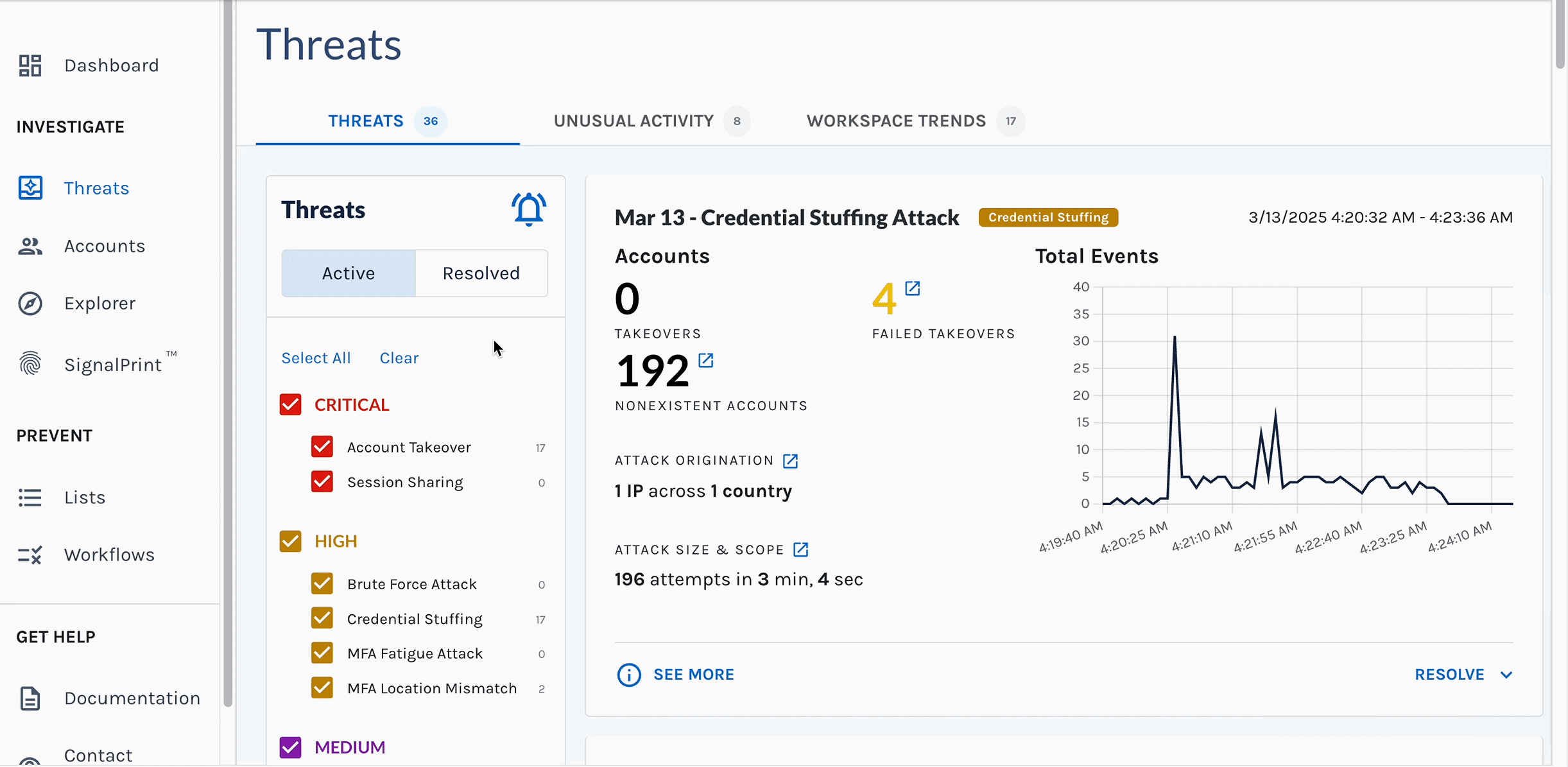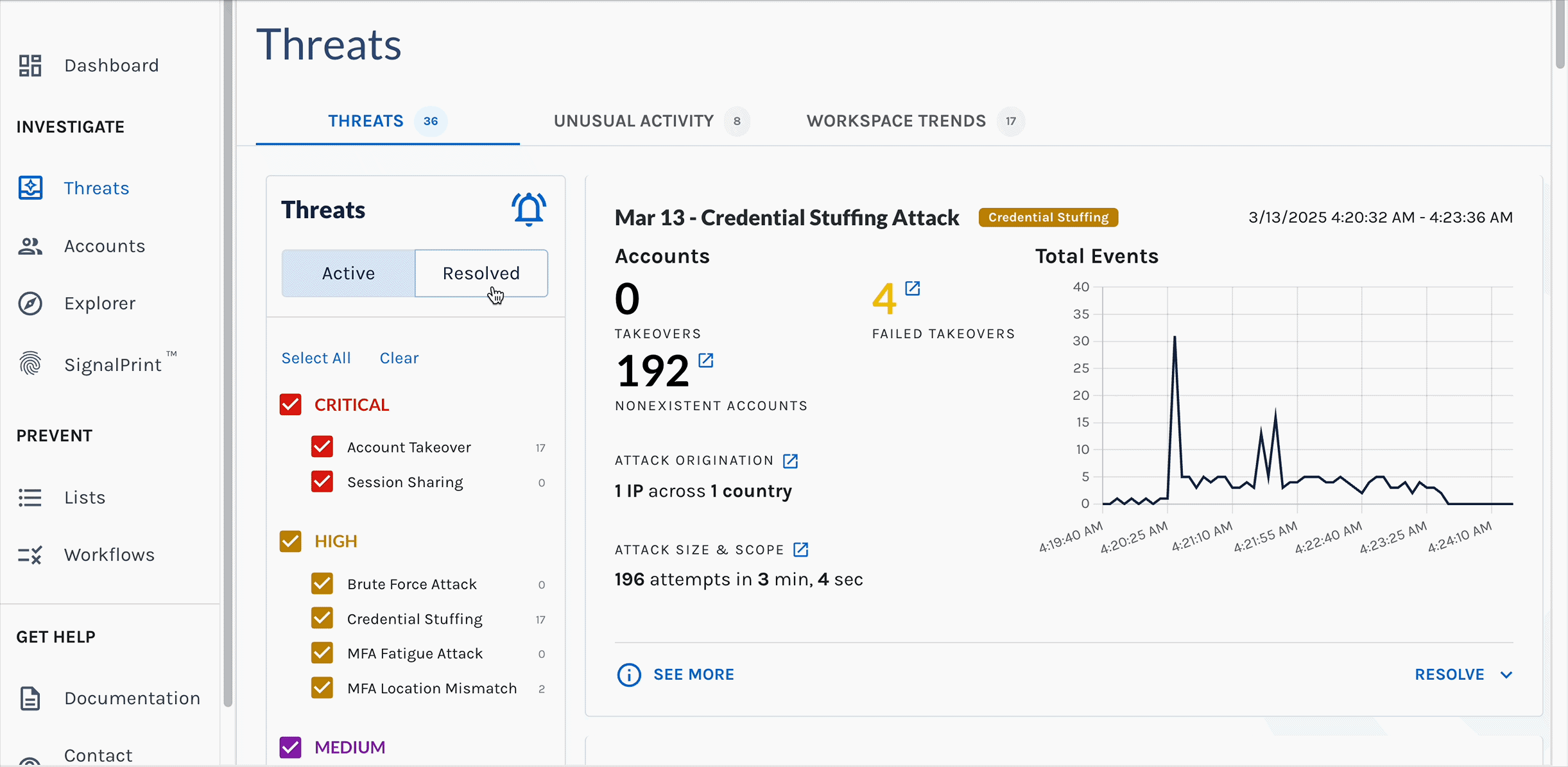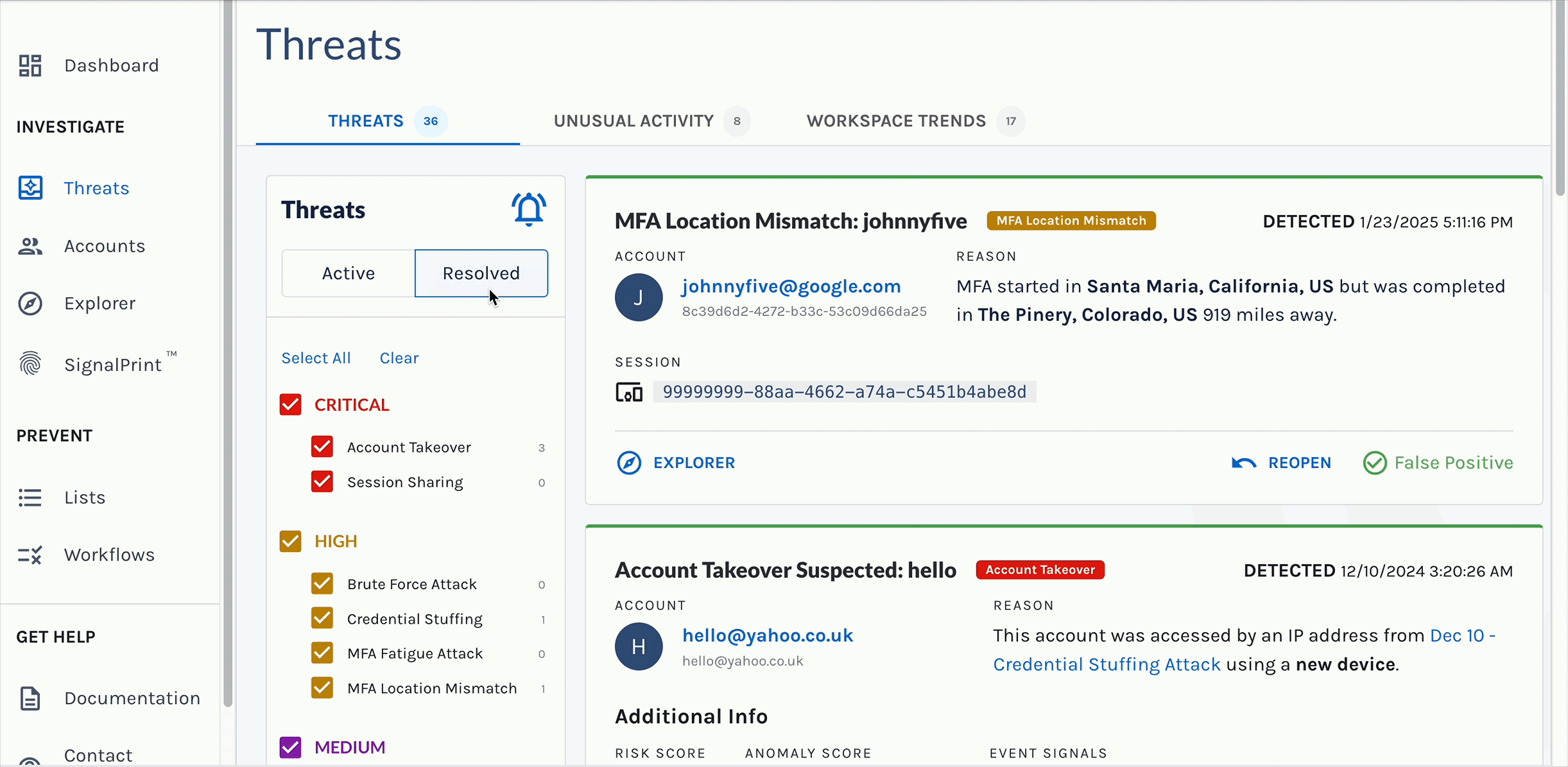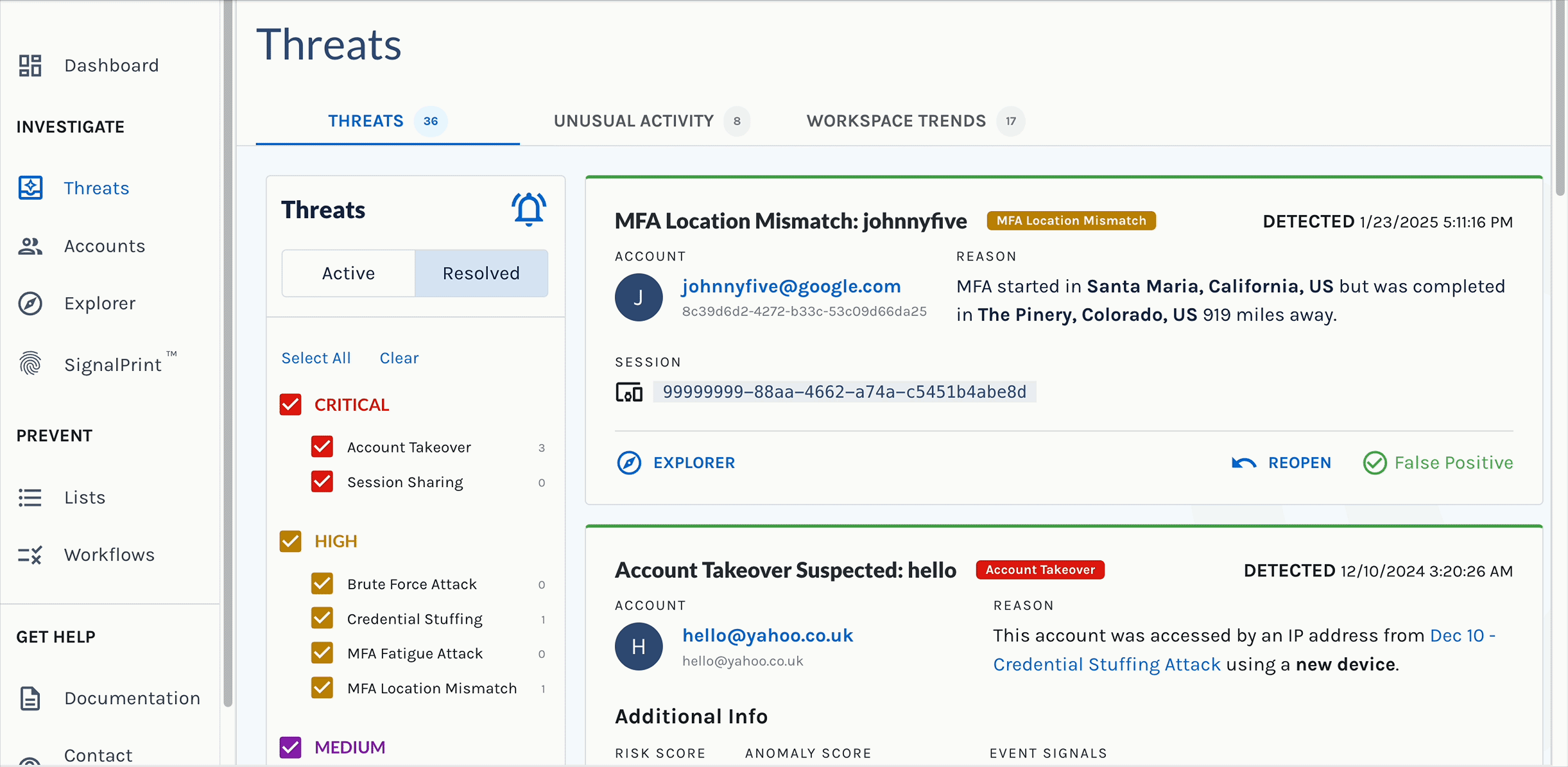
Vera allows organizations to respond to the onslaught of identity threats without stretching resources thin or expanding their headcount. Here's how Vera changes the game:
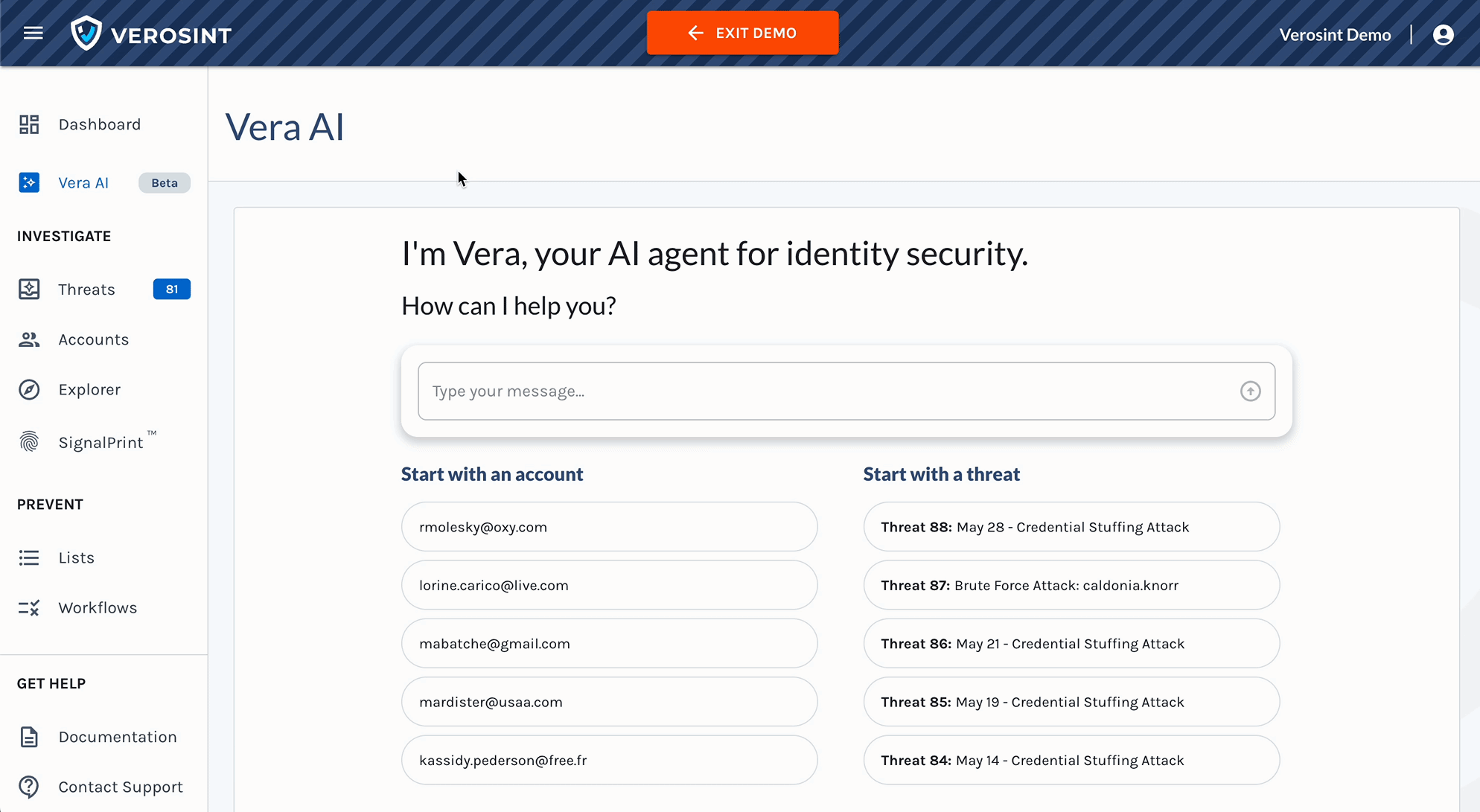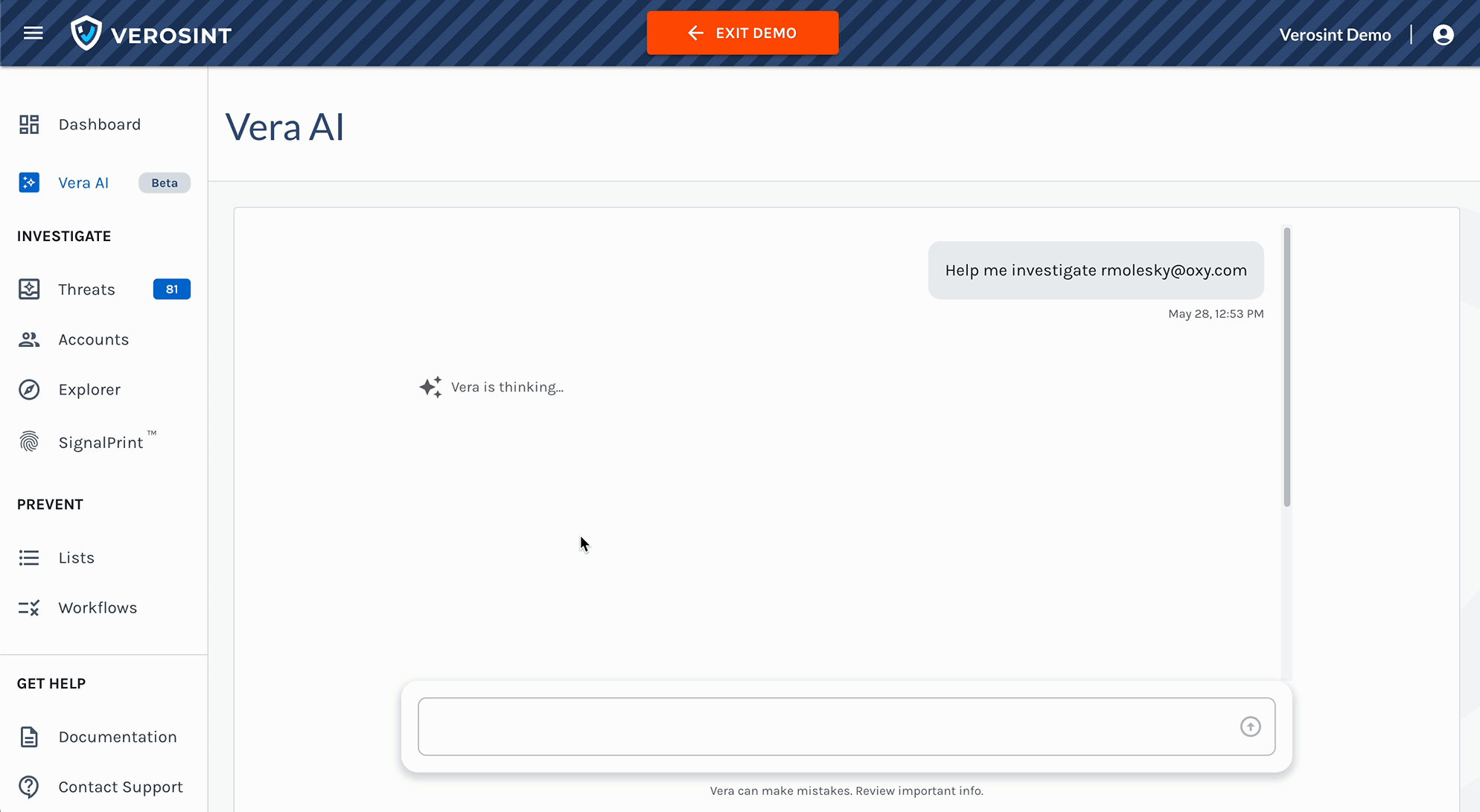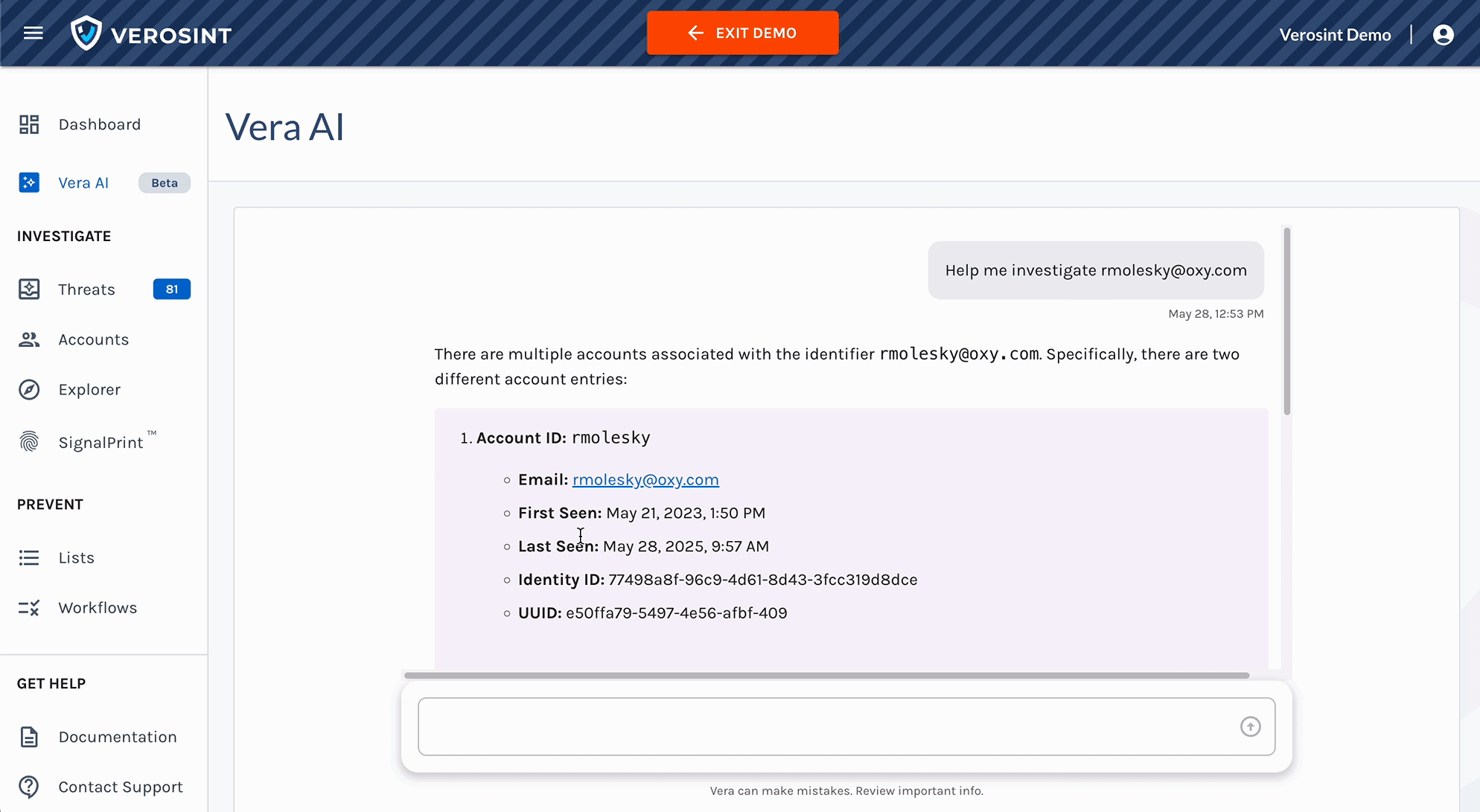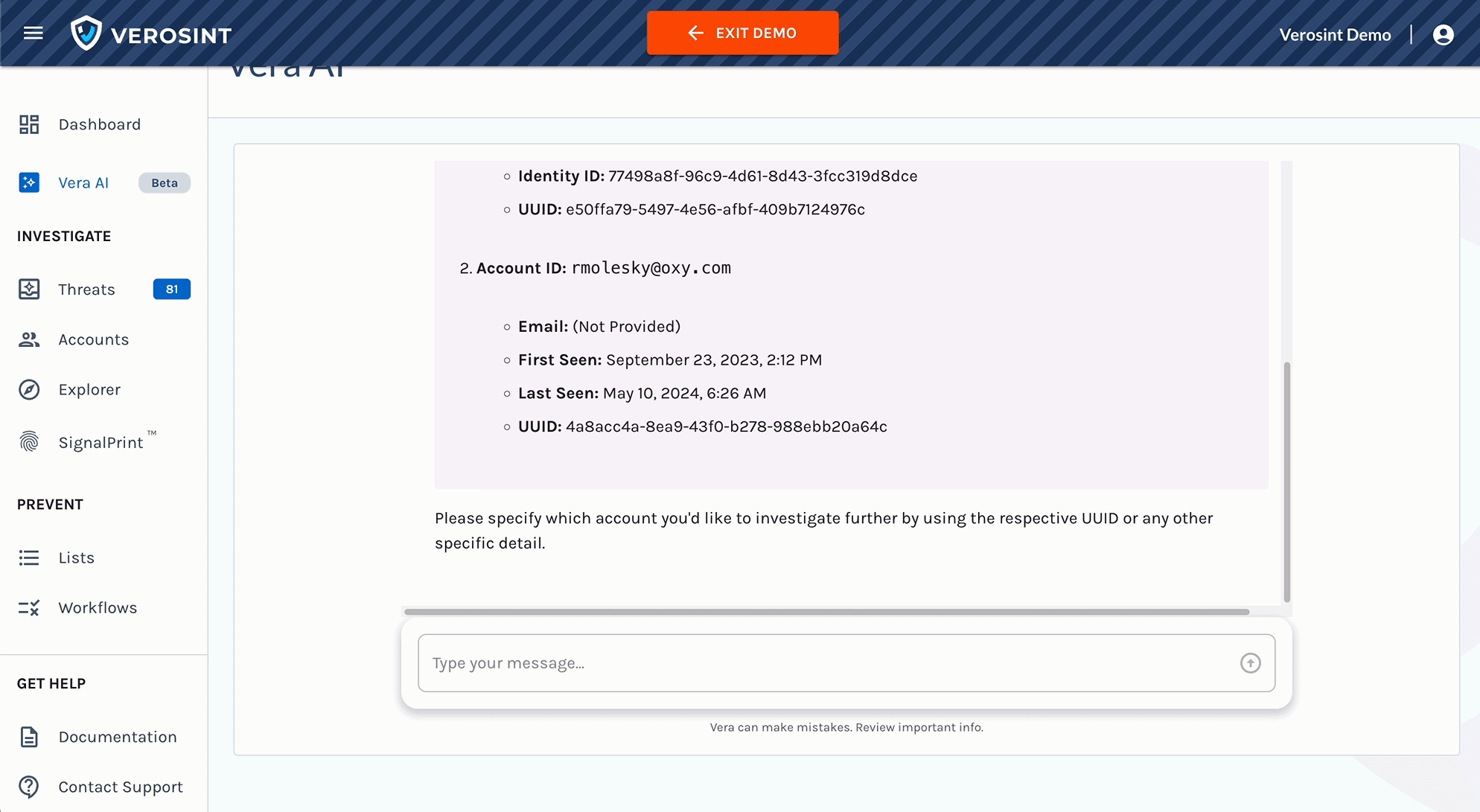
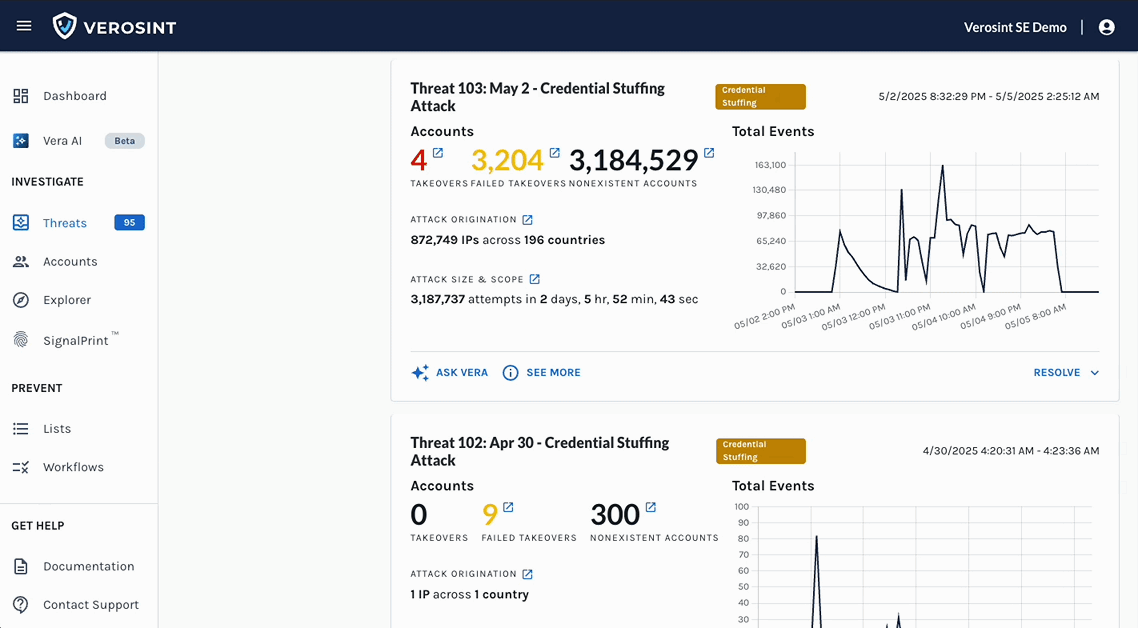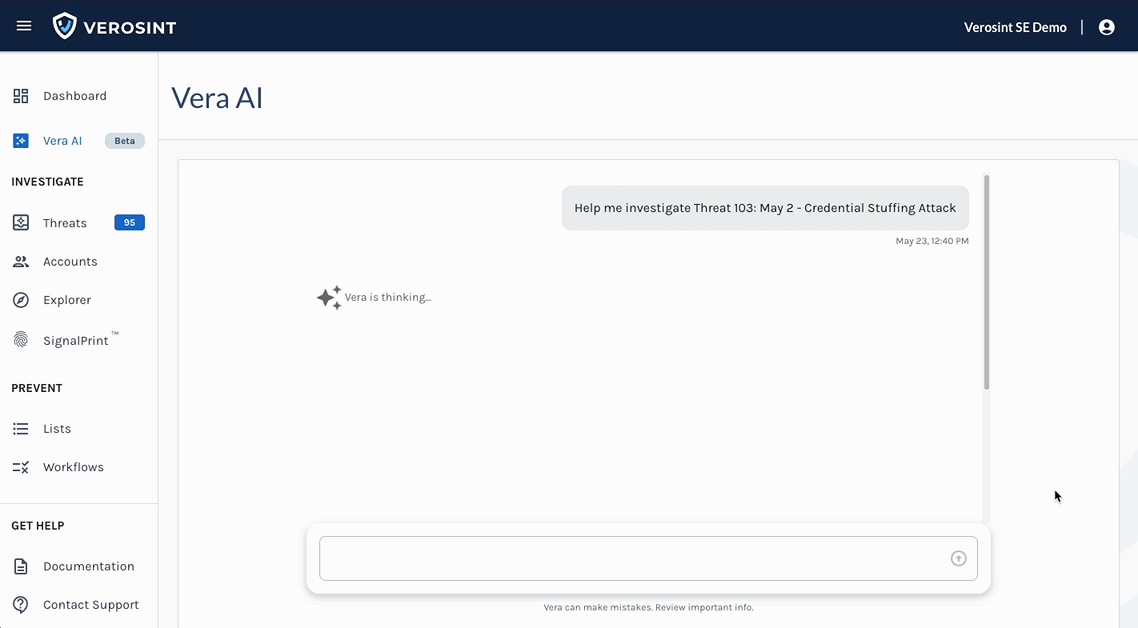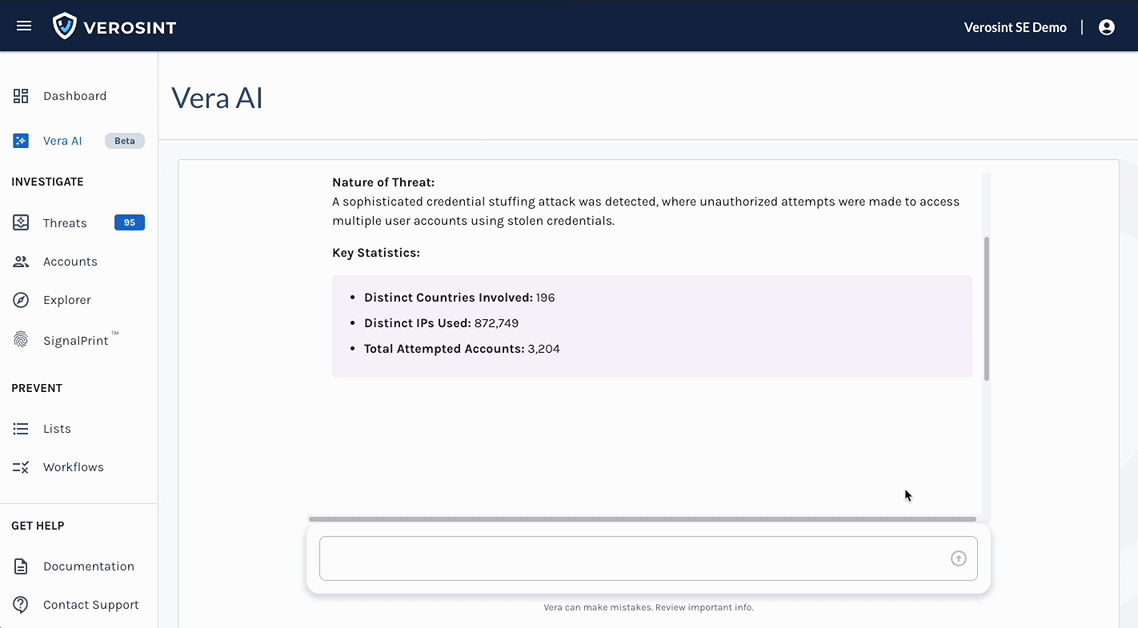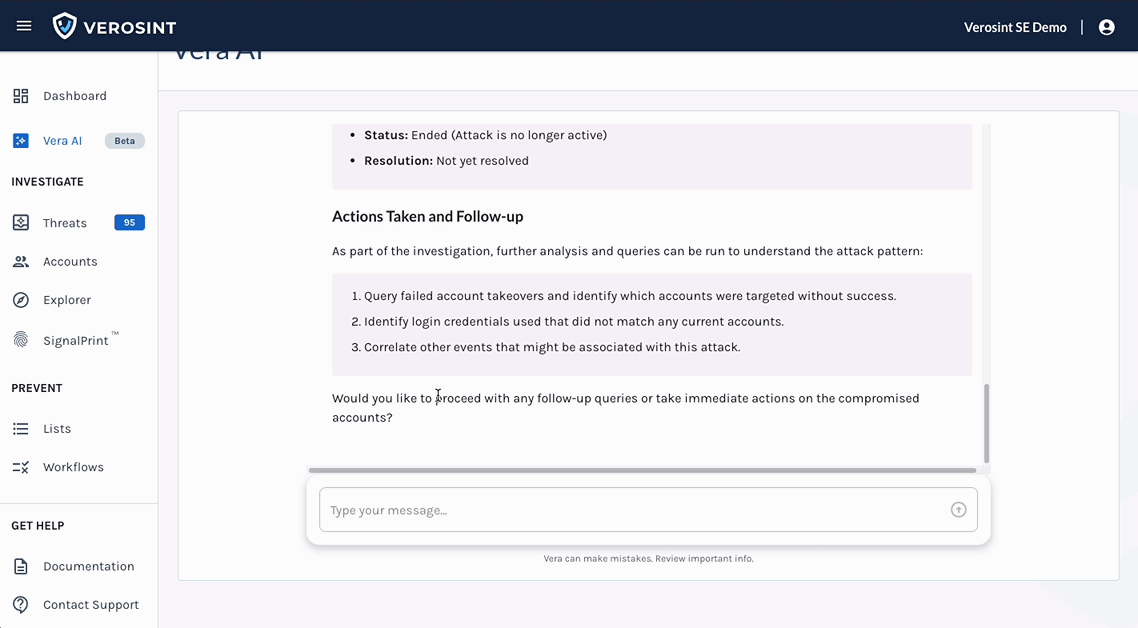
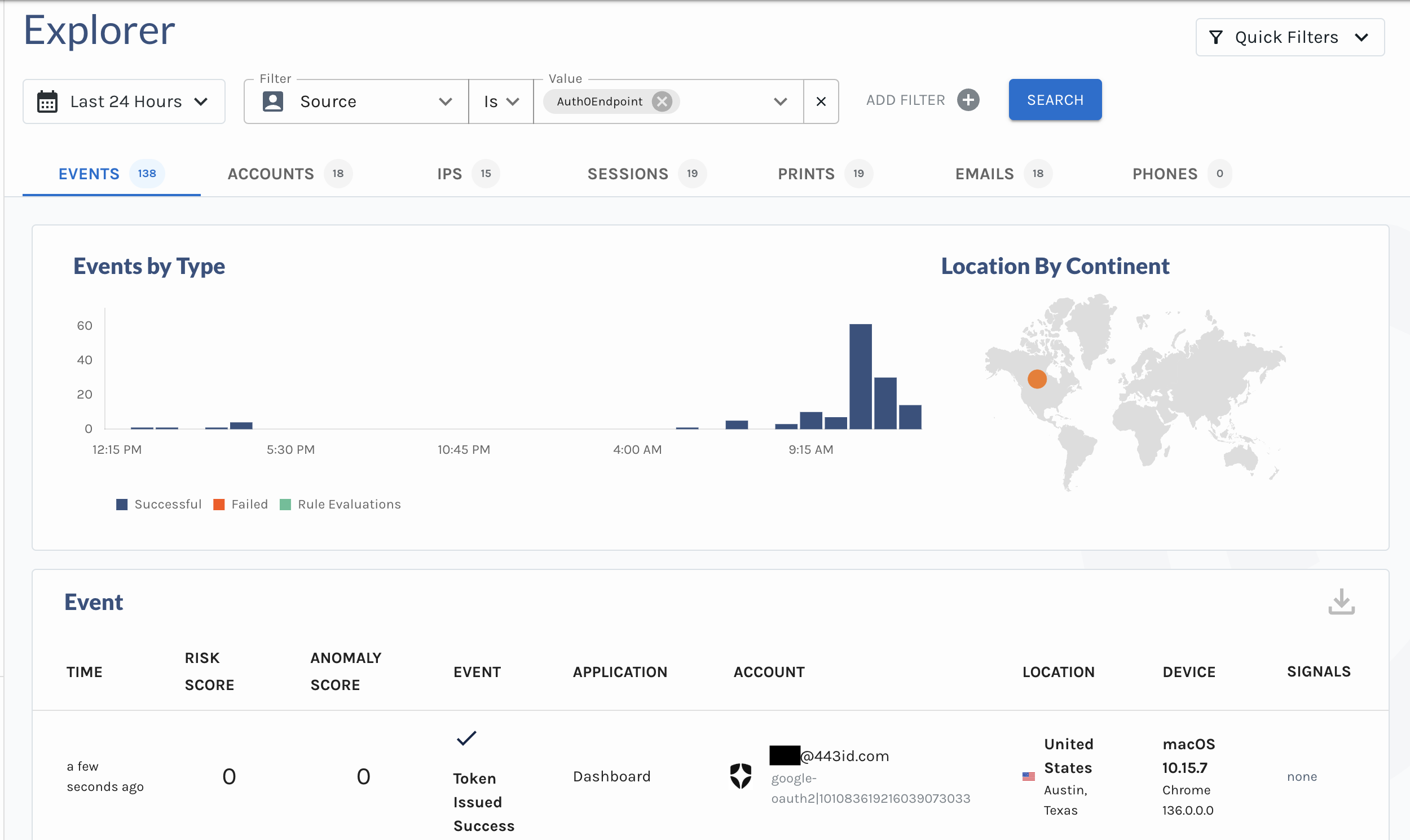
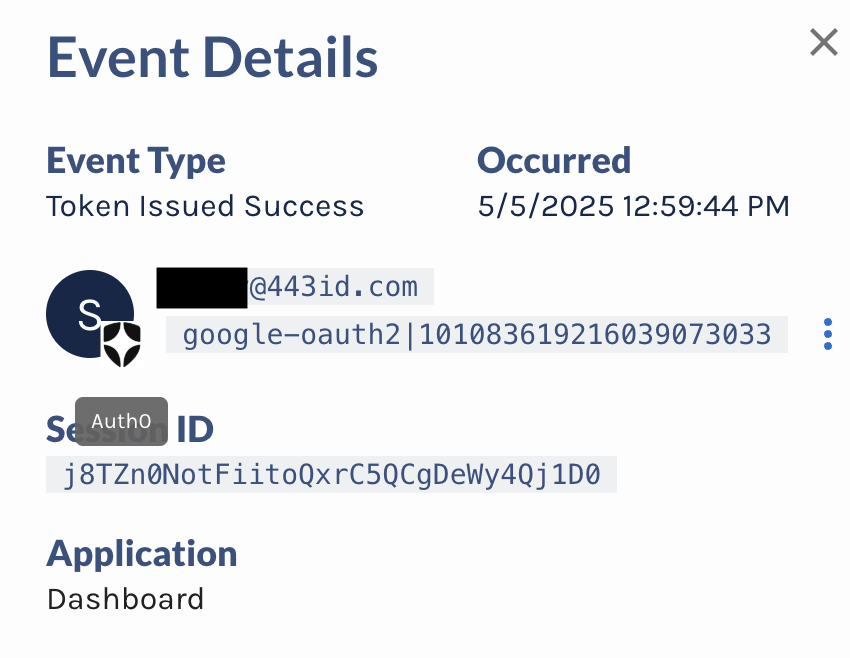
- Continuous Investigation: Investigate new identity security incidents instantly including bulk-analysis of prior events.
- Live Threat Triage and Response: Direct Vera to take targeted actions such as revoking sessions, suspending users, blocking IPs, or requiring adaptive authentication.
- On Demand Reporting and Visualization: Vera can generate custom incident reports and visual insights directly within the conversation.
- Slack and Teams Integration: Engage with Vera without leaving your existing productivity tools, responding as you would to a security analyst team member.
- Automated Playbook Creation: Vera recommends and builds automated response playbooks to continuously lower risk and improve response times.
If you're ready to set new standards for identity security efficiency and effectiveness, sign up for our Early Access program to get started with Vera.