Webhook
Webhook integration allows threat notifications and rule set evaluations to be automatically sent to an external system over HTTPS.
Notification formatNote that the threat details follow a particular format in JSON detailed below. This payload is submitted in an HTTP PUT or POST request.
Steps to setup the Webhook integration:
-
Log in to Verosint and navigate to the workspace settings page.
-
Click Add next to the Webhook logo on the SIEM Logs card
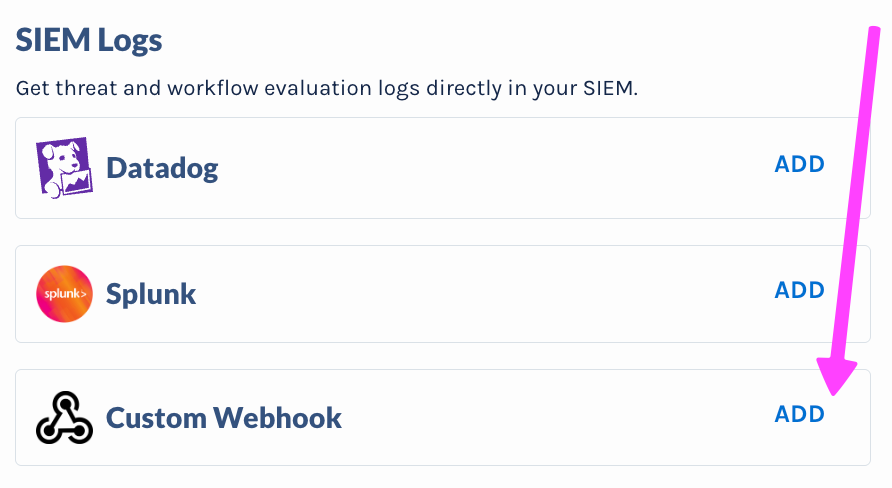
Adding Custom Webhook SIEM integration on the Settings page
-
Fill out the required details
- URL: The URL of the Webhook
- Authorization Token: The contents of the Authorization header if authorization is needed to invoke the Webhook. Leave it blank otherwise. Note that the value should include the entire header value. For example, if bearer tokens are used, then the value will be likely in the form of
Bearer tokenvalue. - Method: The HTTP method to use when invoking the Webhook (
POSTorPUT) - Verify SSL: Uncheck the setting if the Webhook would not pass normal SSL certificate validation. This is usually the case for self-signed certificates.
- Events to Send: The event types to send.
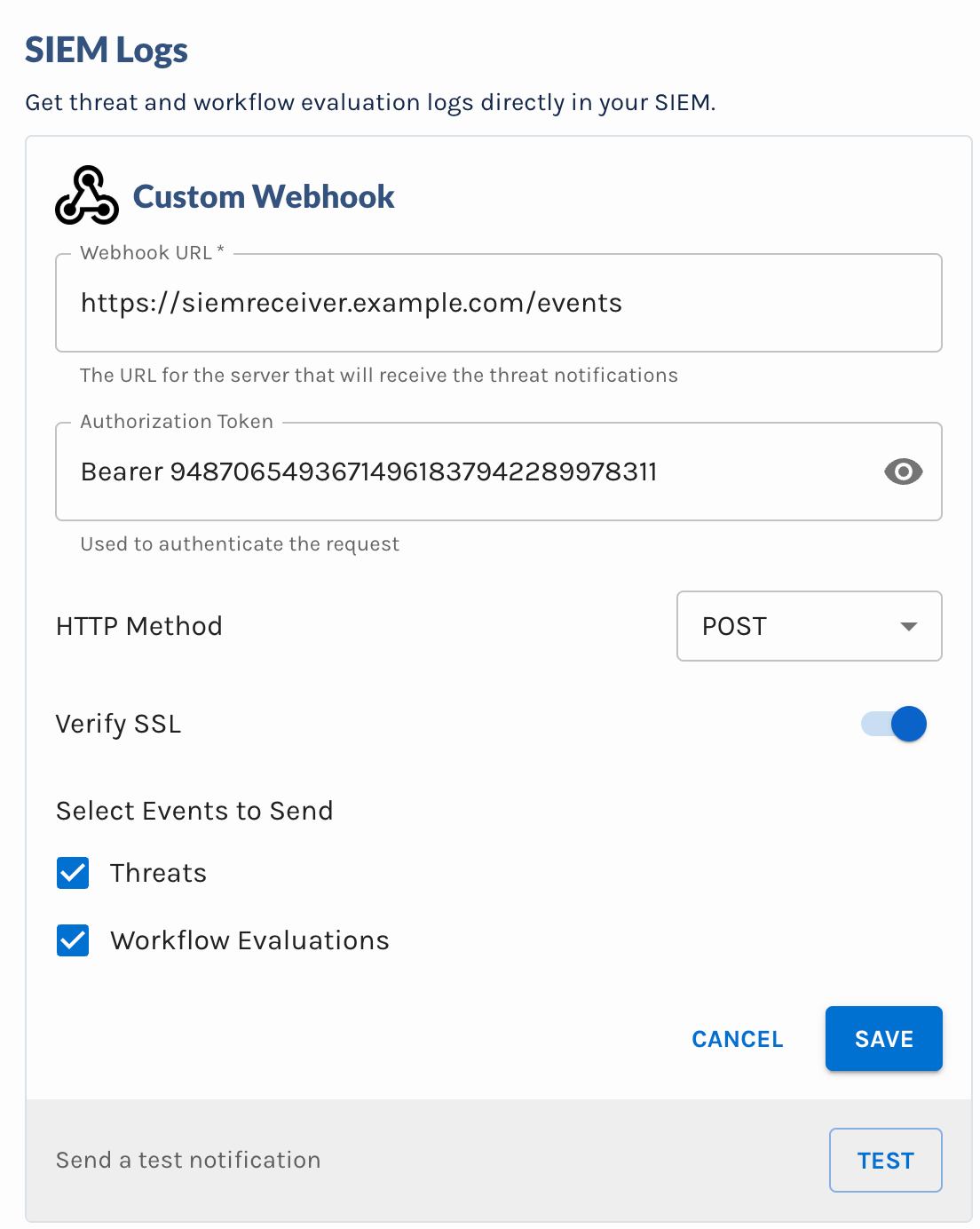
Configuration Panel of the Custom Webhook SIEM Integration
Connection ValidationNote that Verosint will only test if the host and port can be reached over a TCP connection when saving the configuration. To test that the notifications via the configured Webhook is working as expected, click the Test button.
Message Formats
Threat Notification
Threat notifications are submitted in the HTTP request body of the Webhook notification following the JSON format. The description of the properties in the JSON document are provided below.
| Property Name | Description |
|---|---|
| timestamp | RFC3339 formatted timestamp in the Coordinated Universal Time |
| url | The URL where the details of the threat are available in the Verosint application |
| host | Set to api.verosint.com to indicate the source of the threat |
| threat | The threat object |
Threat Object
Property Name | Description |
|---|---|
id | The unique identifier of the threat |
startedAt | The time the threat started |
endedAt | The time the threat ended (may be missing if the threat is still ongoing or the end date is not applicable) |
type | The type of the threat:
|
status | The status of the threat: |
details | The details of the threat. This is a JSON object where the payload depends on the type of threat. |
Example Threat Notification Message
{
"host": "api.verosint.com",
"threat": {
"details": {
"accountId": "auth0|70931ebabcd42b1111cdef9c",
"email": "[email protected]",
"sessionId": "J9NTABC8TbXrWTEyhyGiMob7VLR6Lkmz"
},
"endedAt": "2025-02-10T13:15:40.664338-06:00",
"id": "4ae61183-a630-4852-a3a8-93dfd6eda598",
"startedAt": "2025-02-10T12:15:40.664338-06:00",
"status": "ENDED",
"type": "SESSION_SHARING"
},
"timestamp": "2025-02-10T19:15:40Z",
"url": "https://app.verosint.com/4ab223f0-07e0-435c-96a9-ec74b47088ac/ai-insights?id=4ae61183-a630-4852-a3a8-93dfd6eda789"
}Rule Set Evaluation
Rule Set evaluations are submitted in the HTTP request body of the Webhook notification following the JSON format. The description of the properties in the JSON document are provided below.
| Property Name | Description |
|---|---|
| timestamp | RFC3339 formatted timestamp in the Coordinated Universal Time |
| host | Set to api.verosint.com to indicate the source of the rule set evaluation |
| event | The event object (see below) |
Rule Set Event
The following properties are available in the event property.
General Information
| Property Name | Description |
|---|---|
clientUUID | The unique identifier of the Verosint workspace |
applicationUUID | The unique identifier of the Verosint application |
requestId | The unique identifier of the rule set evaluation request |
processedAt | The RFC3339 formatted timestamp indicating the time of the rule set evaluation |
Signals
| Property Name | Description |
|---|---|
account | The account specific signals |
email | The email specific signals |
event | The event specific signals |
identifiers | The event specific identifiers . Note: some of the identifiers are added during rule set evaluation. Some identifiers are provided by the caller of the API. |
ip | The IP address specific signals |
phone | The phone number specific signals |
userAgent | The browser specific signals |
Evaluation
The evaluation property has the following information
| Property Name | Description |
|---|---|
evaluationId | The unique identifier of the evaluation |
outcome | The outcome of the evaluation. Note that this may be one of the default values such as Allow or Deny, but custom outcomes specific to the workspace may be present in this field |
reason | The reason given for the evaluation. The outcome is also displayed inside the reason by default enclosed in square brackets |
Example Rule Set Evaluation Message
{
"timestamp": "2025-04-23T16:48:30Z",
"host": "api.verosint.com",
"event": {
"clientUUID": "39657d02-7a29-49ae-9863-6d5a4b8529ea",
"applicationUUID": "085ece1a-9842-4023-b196-03730025955b",
"requestId": "01JSF835S9FTMR9RYW5T6HPR9M",
"processedAt": "2025-04-23T16:48:30.796Z",
"account": {
"connectedAccounts": {
"count": 0
},
"daysSinceFirstSeen": 0
},
"email": {
"breachInfo": {
"count": 9,
"daysSinceLastBreach": 67,
"mostRecentBreachDate": "2025-02-15T00:00:00Z",
"yearsSinceLastBreach": 0
},
"domain": "example.com",
"domainRegistrationInfo": {
"daysSinceDomainRegistered": 10843,
"domainRegistrationDate": "1995-08-14T04:00:00Z",
"yearsSinceDomainRegistered": 29
},
"riskScore": 15
},
"evaluation": {
"evaluationId": "01JSHRT2BKE44WMB4GDYVQ8GJY",
"outcome": "Allow",
"reason": "[Allow] no rules applied"
},
"event": {
"riskScore": 18,
"risks": [
"EVENT:NEW_PRINT",
"EMAIL:BREACHED",
"EMAIL:FREE"
]
},
"eventSource": "",
"eventType": "RULE_SET_EVALUATED",
"identifiers": {
"accountId": "testaccount",
"email": "[email protected]",
"eventId": "89f8b23d-366f-4691-d2a6-b9f489213f6b",
"ip": "172.56.89.244",
"phone": "+17374448110",
"printId": "5ddedba5-7b9d-427e-8a6c-77021c1e205d",
"timestamp": "2025-04-23T16:48:30.796Z",
"userAgent": "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/135.0.0.0 Safari/537.36"
},
"ip": {
"asn": "AS21928",
"asnInfo": {
"size": "2x-large"
},
"aso": "T-Mobile USA, Inc.",
"geo": {
"latitude": 30.26715,
"longitude": -97.74306
},
"location": {
"city": "Austin",
"continent": "NA",
"country": "US",
"region": "Texas",
"regionCode": "TX"
},
"locationId": "4671654",
"network": {
"cidr": "172.56.0.0/16",
"size": "medium"
},
"riskScore": 0,
"timezone": "America/Chicago",
"type": "isp"
},
"phone": {
"carrier": "BANDWIDTH.COM-NSR-10X/1",
"carrierIdentificationCode": "152725",
"location": {
"country": "US"
},
"riskScore": 0,
"type": "FIXED_LINE_OR_MOBILE"
},
"userAgent": {
"browser": {
"name": "Chrome",
"version": "135.0.0.0"
},
"daysSinceRelease": 0,
"device": {
"type": "desktop"
},
"os": {
"name": "macOS",
"version": "10.15.7"
},
"riskScore": 0
}
}
}Updated 3 months ago