Ping DaVinci
With Verosint and Ping DaVinci, you can protect against fraudulent activity and determine account risks in the following ways.
Send an Event
Verosint enables you to evaluate a login or registration event to determine risk to your systems. Each system access attempt typically contains the following information:
- Account information (Email address, IP address, Phone number).
- Timestamp of the event.
- Account ID (whatever you use as the unique identifier for this account, such as a username or email address).
- User agent (the browser information the account used to access your applications).
With this information, Verosint can determine if the account is potentially risky. For example, if the geographic location of the IP address and the area code or country code of the phone number aren’t the same, the account may be fraudulent. With multiple events, Verosint can determine potential account sharing or fraud based on geolocation and time of access.
Evaluate a Rule Set
Verosint enables Rule Sets to prevent fraud by enforcing restrictions and outcomes specific to your environment. For example, if you want to limit access to users in specific locations, you can create a Rule Set based on geography through IP address, internet provider and domain location, or phone number and area code. Or, you can trigger additional security checks in your registration flow if an account is found to be part of a recent data breach.
Create Rule Sets that are meaningful for your business. Then, use the following information to determine if an account meets or violates the defined criteria:
- The Rule Set ID (generated for each rule created in Verosint).
- An email address, phone number, or IP address for an account.
Resources
To add the Verosint DaVinci Connector, make sure you have an active Ping Identity account and a Verosint account. For details about creating Verosint rules and using DaVinci, see: Using Rule Sets .
Using the Verosint Connector in an Authentication Flow
An HTML form gathers data and stores it in variables.
For an Event Evaluation:
- Account information (Email address, IP address, Phone number).
- Timestamp of the event. This is not required, but you can use a Code Snippet connector with the following code to have a properly formatted timestamp:
// Supported language: Javascript module.exports = a = async ({params}) => { console.log('timestamp: ', new Date().toISOString()) return {'timestamp': new Date().toISOString()} } - Account ID (whatever you use as the unique identifier for this account, such as a username or email address).
- User agent (the browser information the account used to access your applications).
For a Rule Set Evaluation:
- The rule UUID (generated for each Rule Set created in Verosint).
- An email address, phone number, or IP address for an account.
Next, the connector directs the browser to the Verosint endpoint. The information is passed to the endpoint for the selected evaluation type and assessed. It is then passed along to the function call to determine the next step.
Using the HTTP Connector
Ping offers a generic HTTP connector to use with Verosint. Configure a POST method to the Verosint API with a valid Verosint API key:
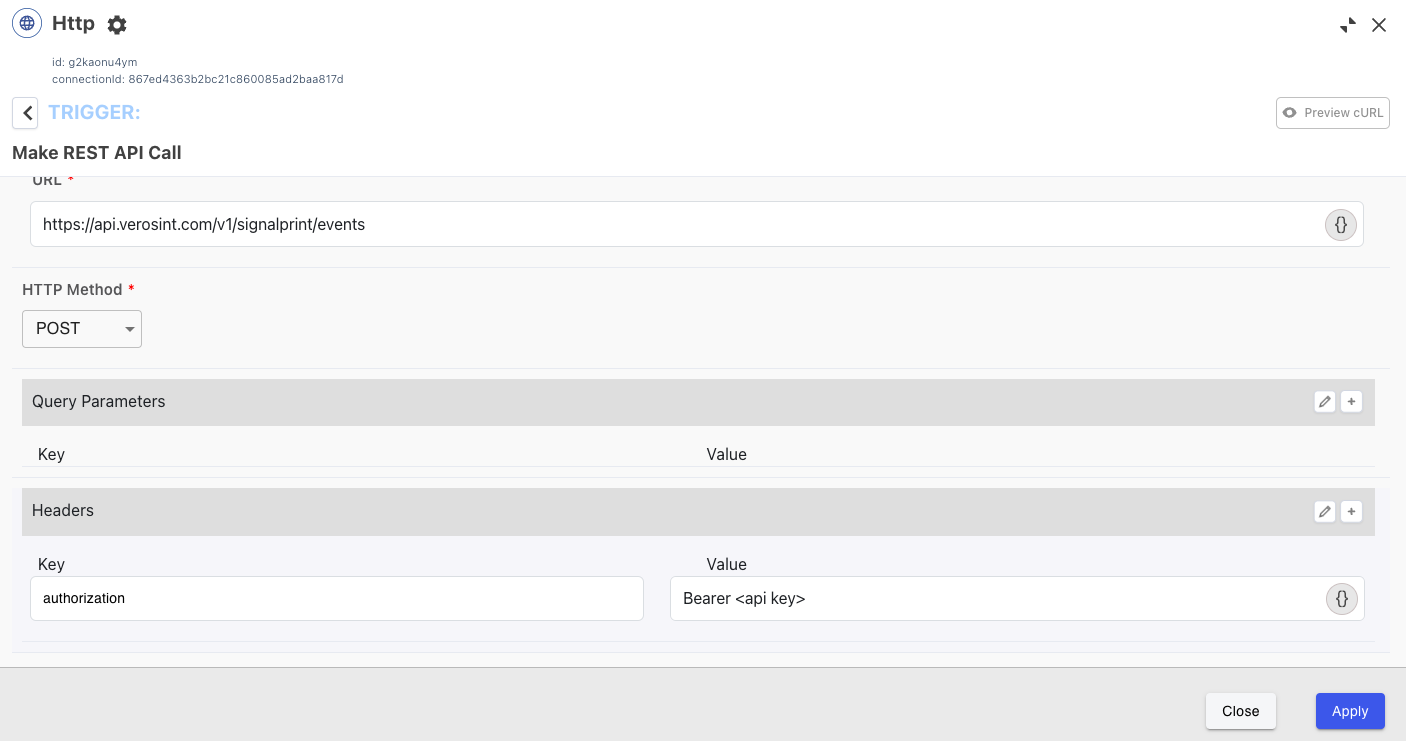
Populate the payload:
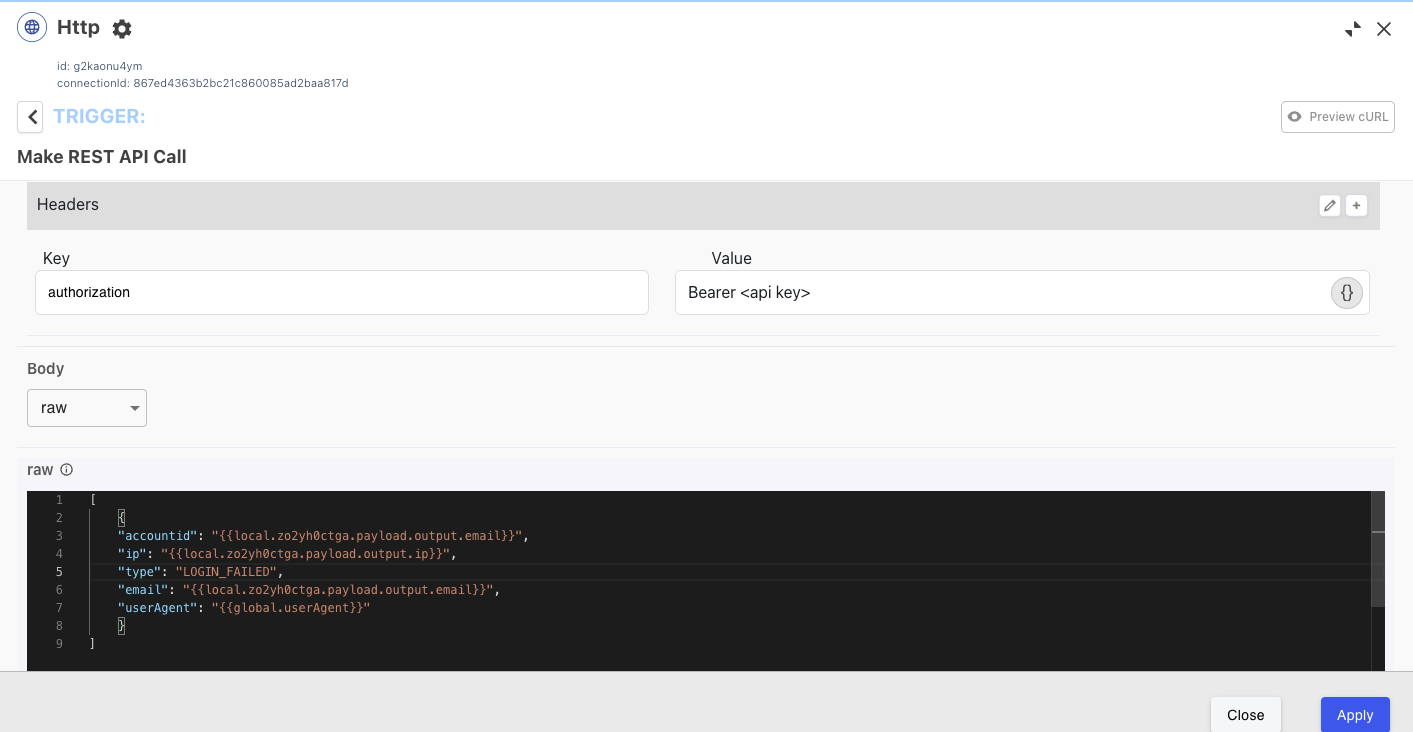
Updated 3 months ago