Understand Scores and Labels
Verosint analyzes multiple factors to determine each type of potential threat. Specific signals for each account type are listed here, or you can review the complete list of Signal Definitions.
Multiple Accounts
A user with multiple accounts accessing an application is identified by analyzing a series of events with different account identifiers that share similar locations, devices (prints), timing, and browsers.
Search for these types of accounts with the print.multipleAccounts filter in the Event Explorer. You can then create a rule with “PRINT:MULTIPLE_ACCOUNTS” in event.risk to prompt for MFA or prevent these from accessing your systems.
Credential Stuffing and Account Takeover
Credential stuffing uses automated tools to try several username and password combinations obtained from data breaches. Attackers try to access user accounts by exploiting the fact that many people reuse the same credentials across multiple online platforms. Verosint determines a Credential Stuffing attack based on many login event failures over a short period of time, followed by a success. The IP address and ASN will generally be the same.
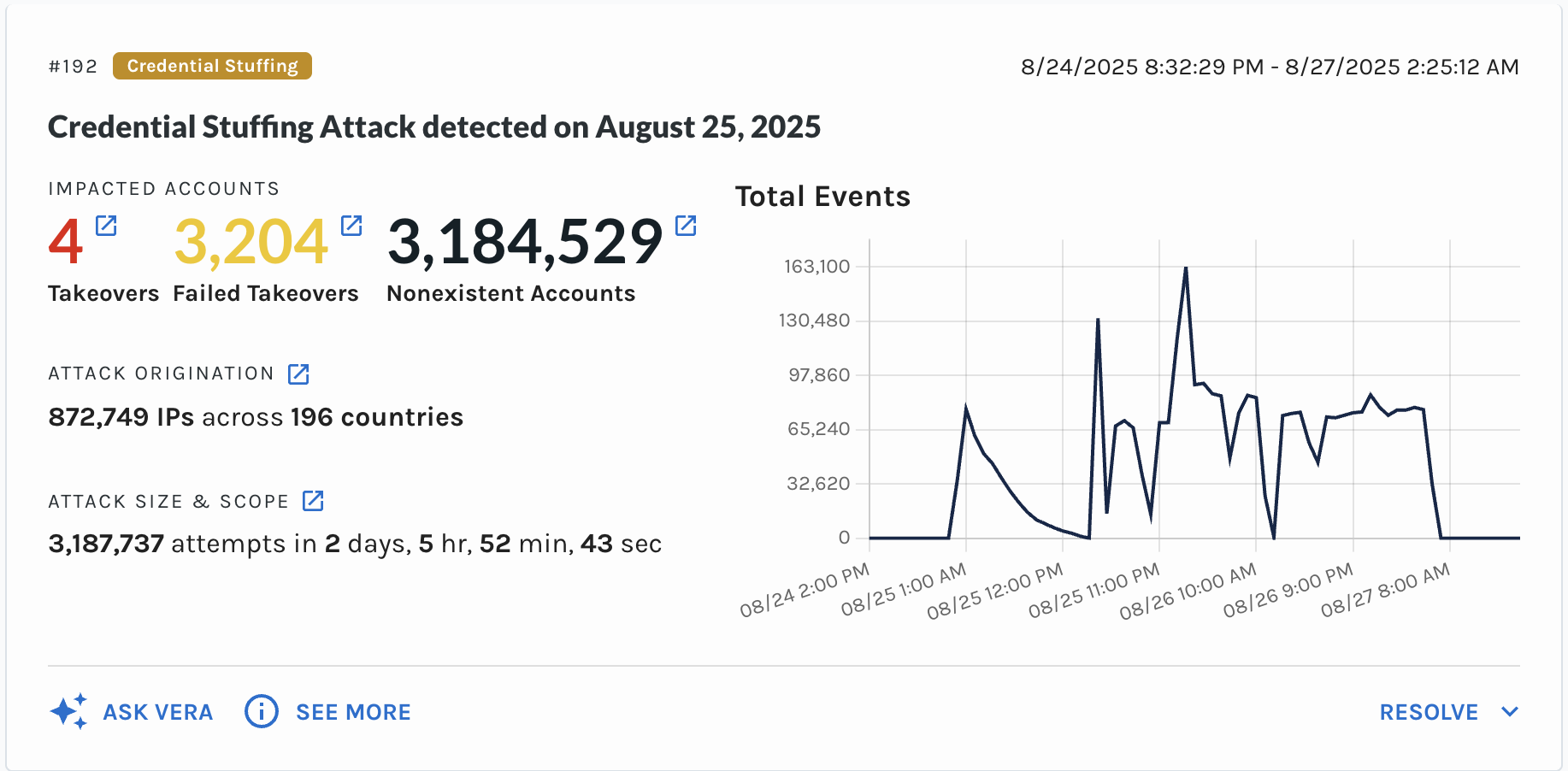
Example Credential Stuffing Attack
Quickly detecting credential stuffing is critical for reducing the number of account takeovers, in which third-party actors can use an account for malicious purposes. You can find events that indicate credential stuffing in the Event Explorer using the event.risks filter with the "EVENT_STUFFING_ATTACK" value, and accounts where account takeover was detected using the event.risks filter with the "ACCOUNT:TAKE_OVER" value.
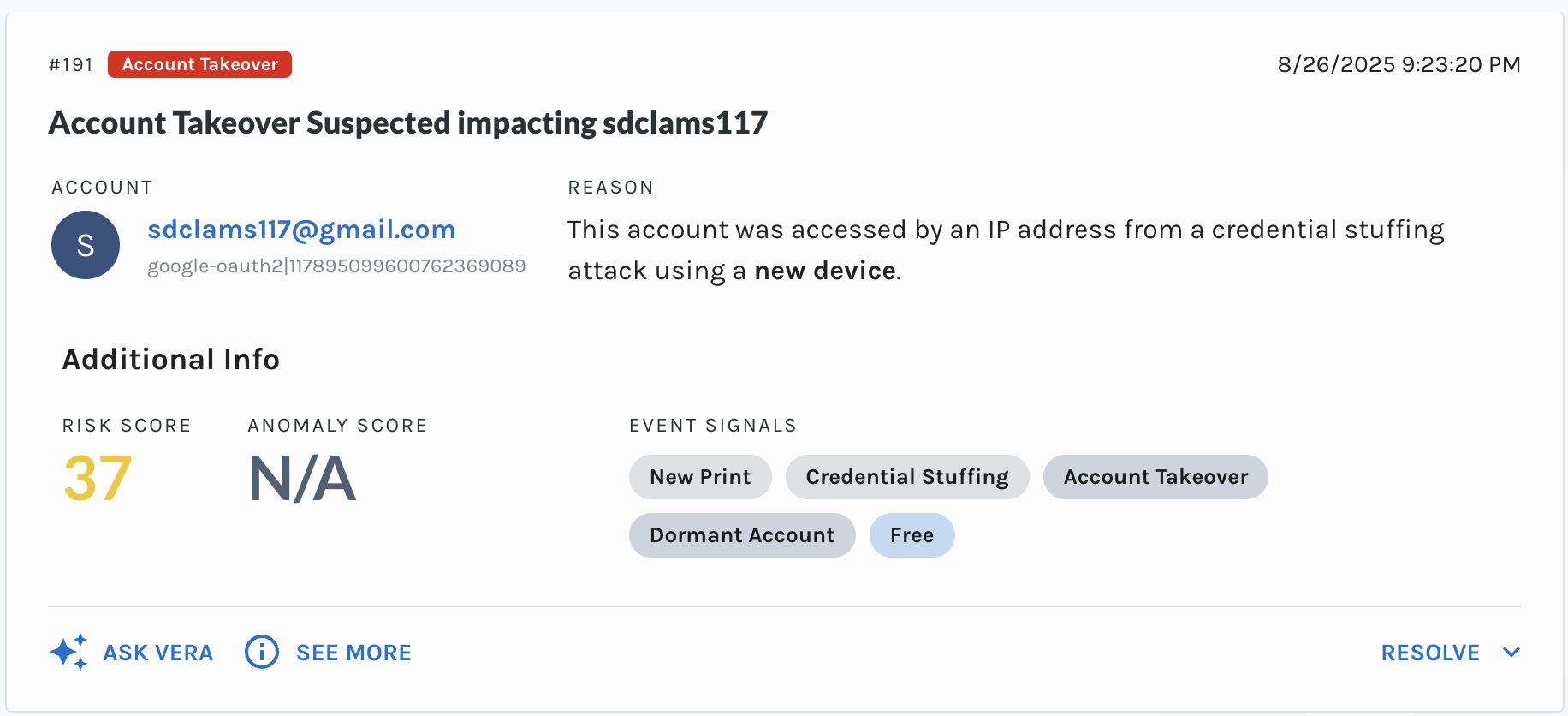
Example Account Takeover
To prevent credential-stuffing attacks, you can create a rule with the event.risks "ACCOUNT:TAKE_OVER" and "EVENT:STUFFING_ATTACK" signals to prevent the automated process from a successful login.
Outlier Account
Verosint looks at a set of events as a whole to determine if the behavior or characteristics of any account are outside of the normal characteristics of all others in a workspace. This calculation evaluates three days of event data for IP address, user agent, time, and location to determine patterns in the workspace. Accounts different from all others are labeled Outlier Account in the Event Explorer.
To prevent access to an outlier account, or require MFA for these accounts, you can create a rule with "ACCOUNT:OUTLIER_ACCOUNT" in event.risks.
Event Anomaly Scores and Event Risk Scores
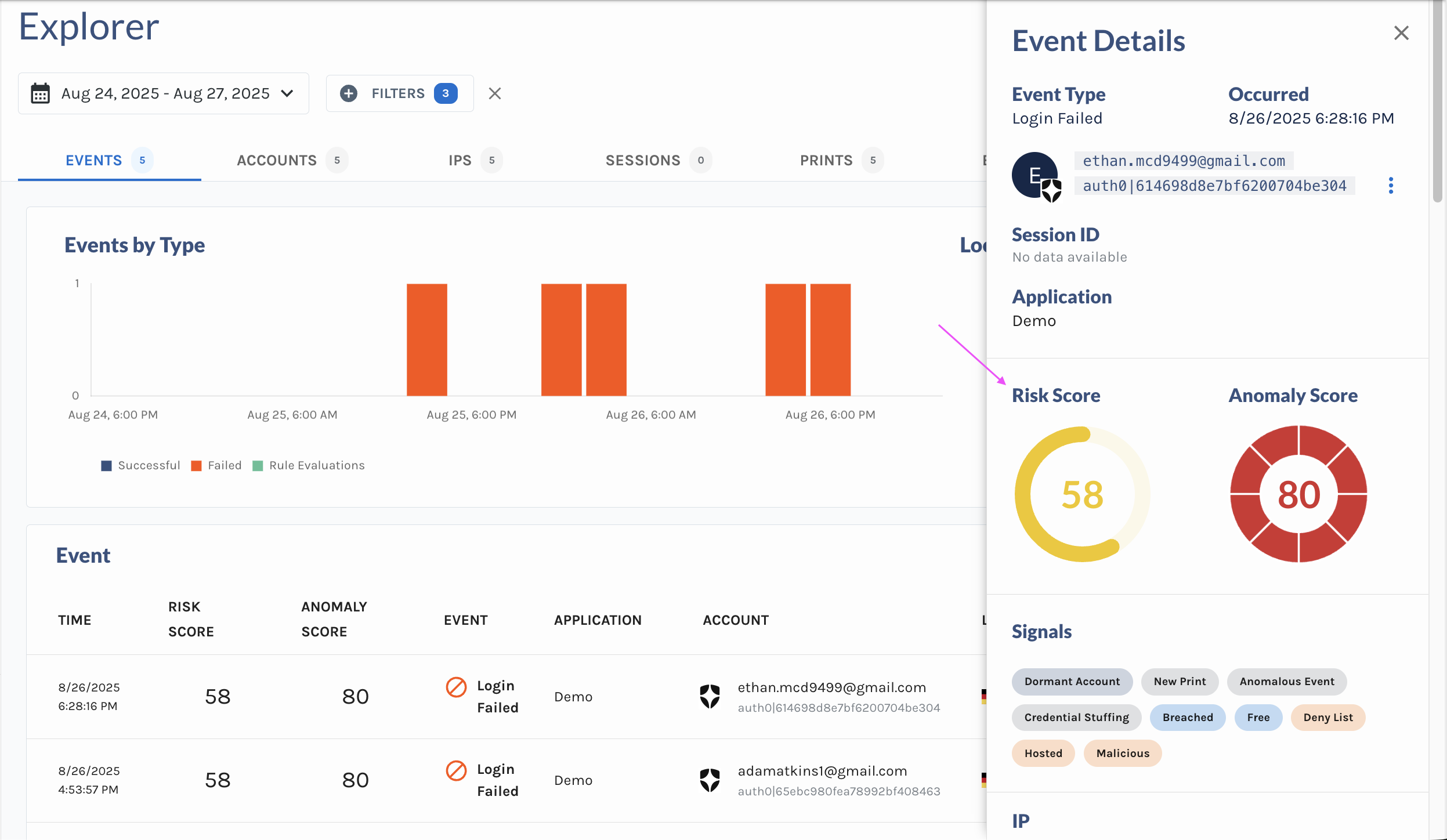
Verosint monitors the activity of each account over a 30-day time period for patterns and irregularities, and each event associated with the account is given an Event Risk and Event Anomaly Score (0-100, the least risky being 0). If an account logs in with a different pattern from its historical data, the login event will receive an Event Anomaly score.
An event that has an anomaly score of 75 or more is considered risky and labeled Anomalous.
The Risk score is a general calculation based on Verosint’s internal algorithms and OSINT data, which is constantly changing. If an event is given both a high Risk and Anomaly score, it’s likely to be a fraudulent event. You can sort the table in Event Explorer by the Risk and Anomaly column headings, or you can filter on events with "EVENT:ANOMALOUS_EVENT" in event.risks, or filter specific risk and anomaly types (event.anomalyScore, event.riskScore, ip.riskScore, email.riskScore, and phone.riskScore).
To create a rule based on anomaly scores, use "EVENT:ANOMALOUS_EVENT" in event.risks. For example, to filter events with an anomaly score higher than 75, you could add:
has(event.anomalyScore) && event.anomalyScore > 75
Updated 3 months ago