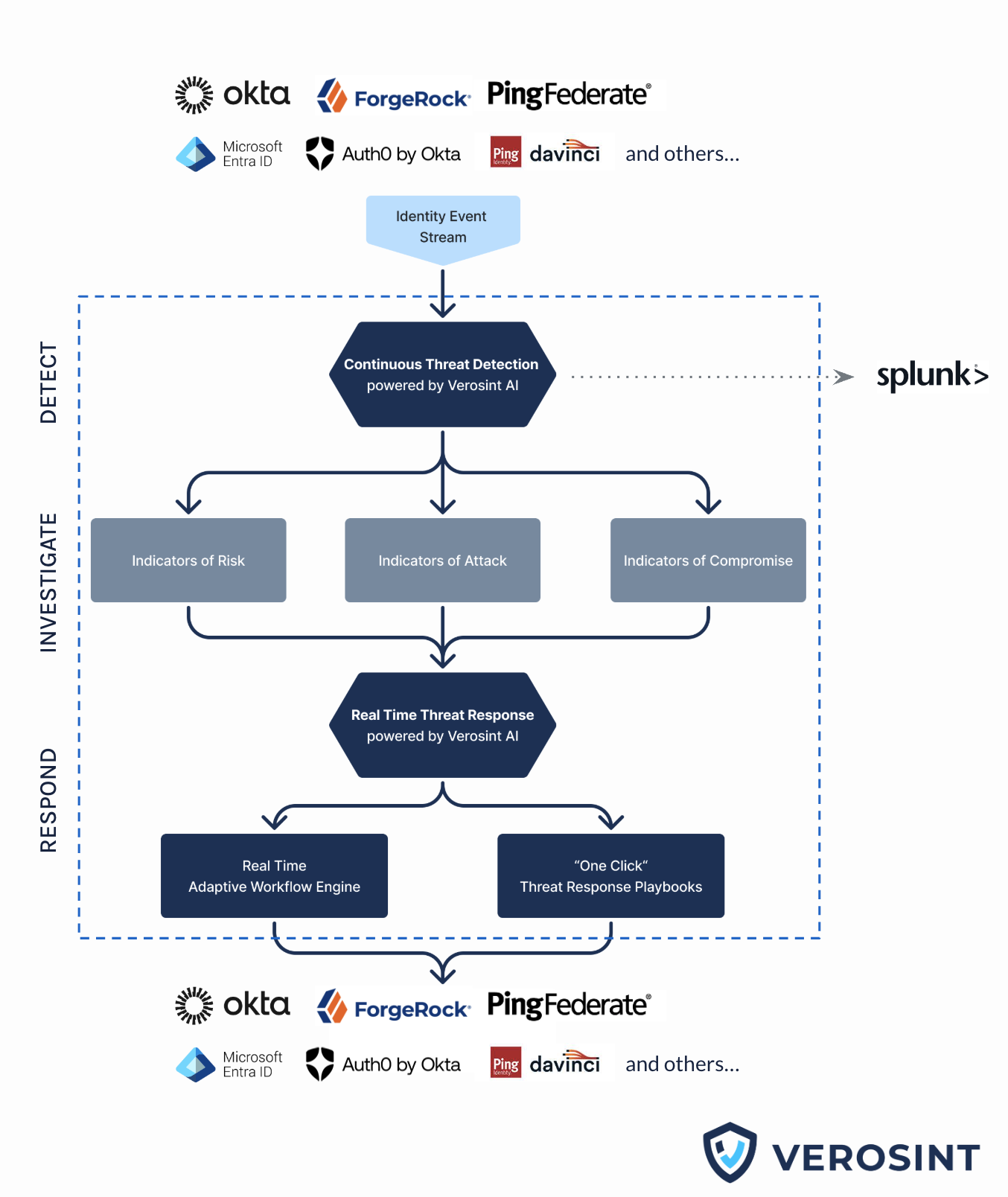
How Verosint Works
Verosint's Threat Detection, Investigation, and Response platform provides real-time, intelligent ITDR for both workforce and customer identities.
- Fastest MTTD & MTTR: Detect and respond to Identity based threats faster than anyone else in the industry
- Detect Advanced Threats: Spot session hijacking, credential stuffing, account takeovers and more
- Investigate Efficiently: Our customers say investigating incidents has gone from days to minutes with our AI Insights, unparalleled visibility and intelligence
- Remediate Quickly: Automatically resolve identity threats with our integrated remediation playbooks
- Easy to Deploy: Deploys in 60 minutes or less
How Verosint Works
In real time, Verosint collects authentication events from your identity provider and enriches them with risk intelligence based on the account's IP, Email, Device, and behavioral pattern. With that enriched data, Verosint continuously detects identity threats and classifies them into three categories: indicators of risk, attack, and compromise.
All this threat intelligence is accessible via advanced investigation tools like Account Intelligence and Explorer, empowering your team to thoroughly investigate any detected threat.
Finally, Verosint makes it easy to remediate threats in real time through our threat response playbooks and adaptive rule set engine.
Updated 3 months ago