Introducing Session Sharing Threat Detection: Defending Against Token Stealing Attacks
🌟 New Feature Alert 🌟
🎉 Happy New Year! 2️⃣ 0️⃣ 2️⃣ 5️⃣ We’re excited to introduce a new threat detection capability: Session Sharing. Building on Verosint’s existing ability to detect and respond to threats, this addition empowers you to stay ahead of token stealing attacks, a rising trend in Account Takeover (ATO) strategies.
What’s New?
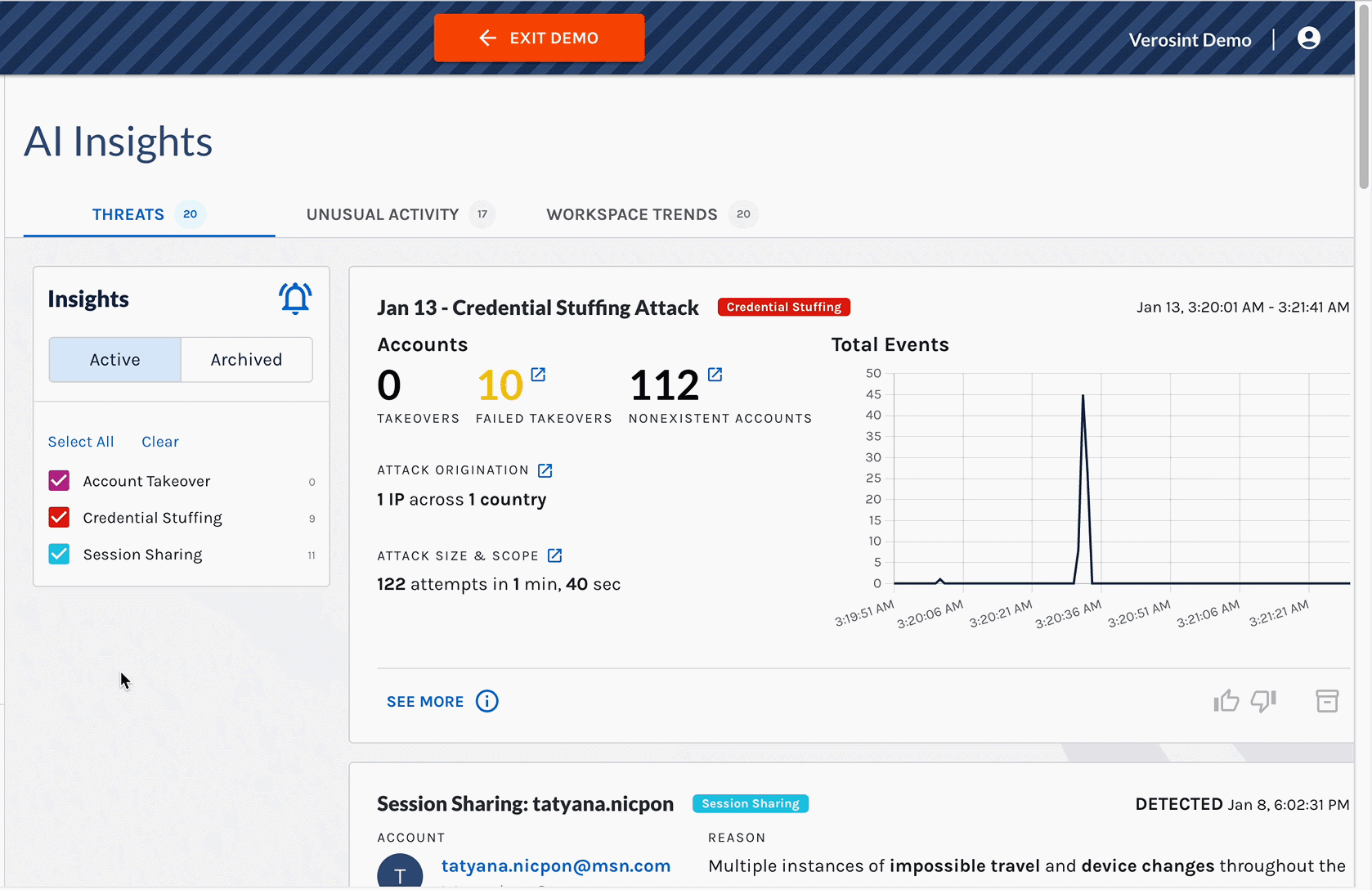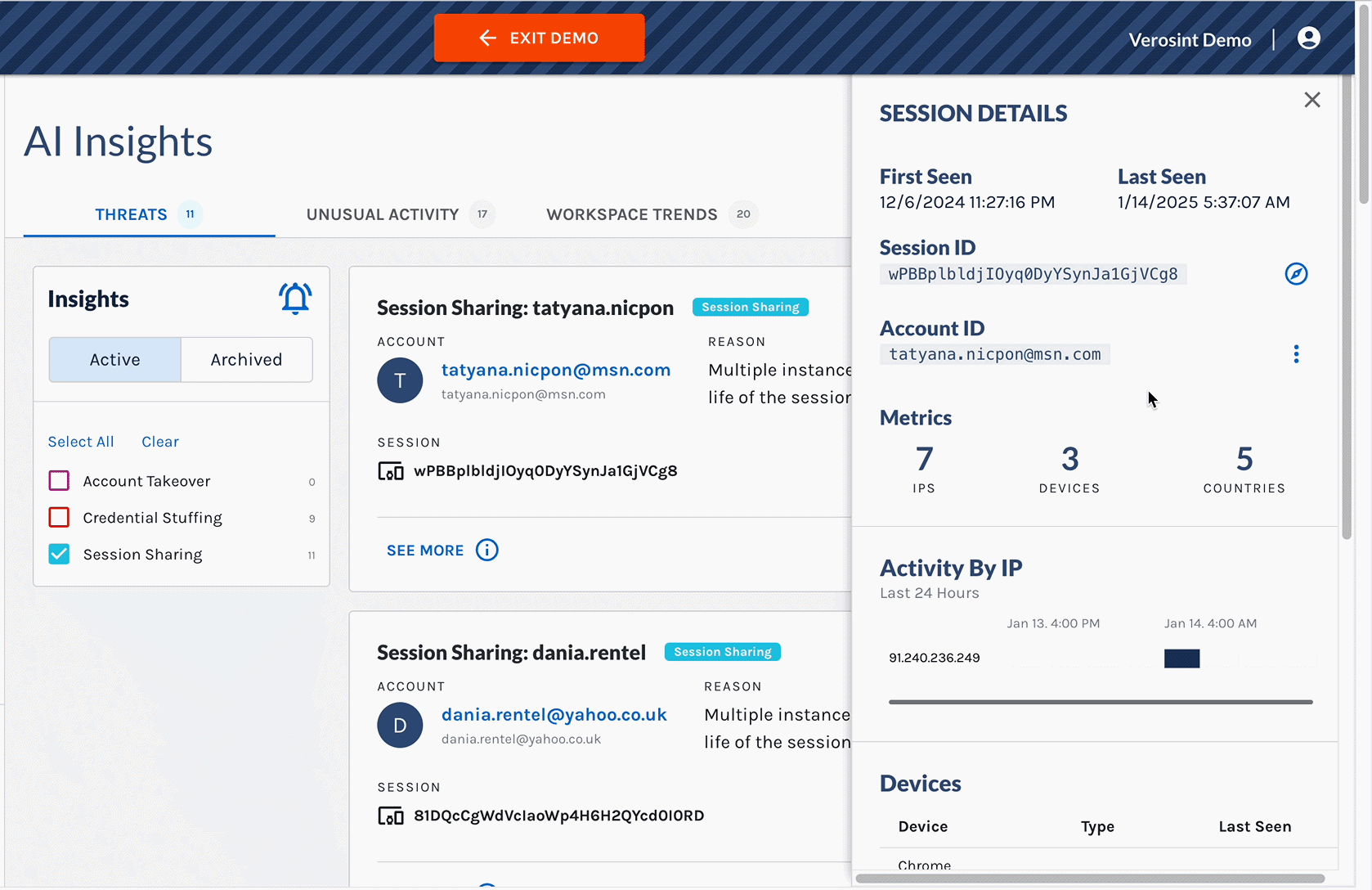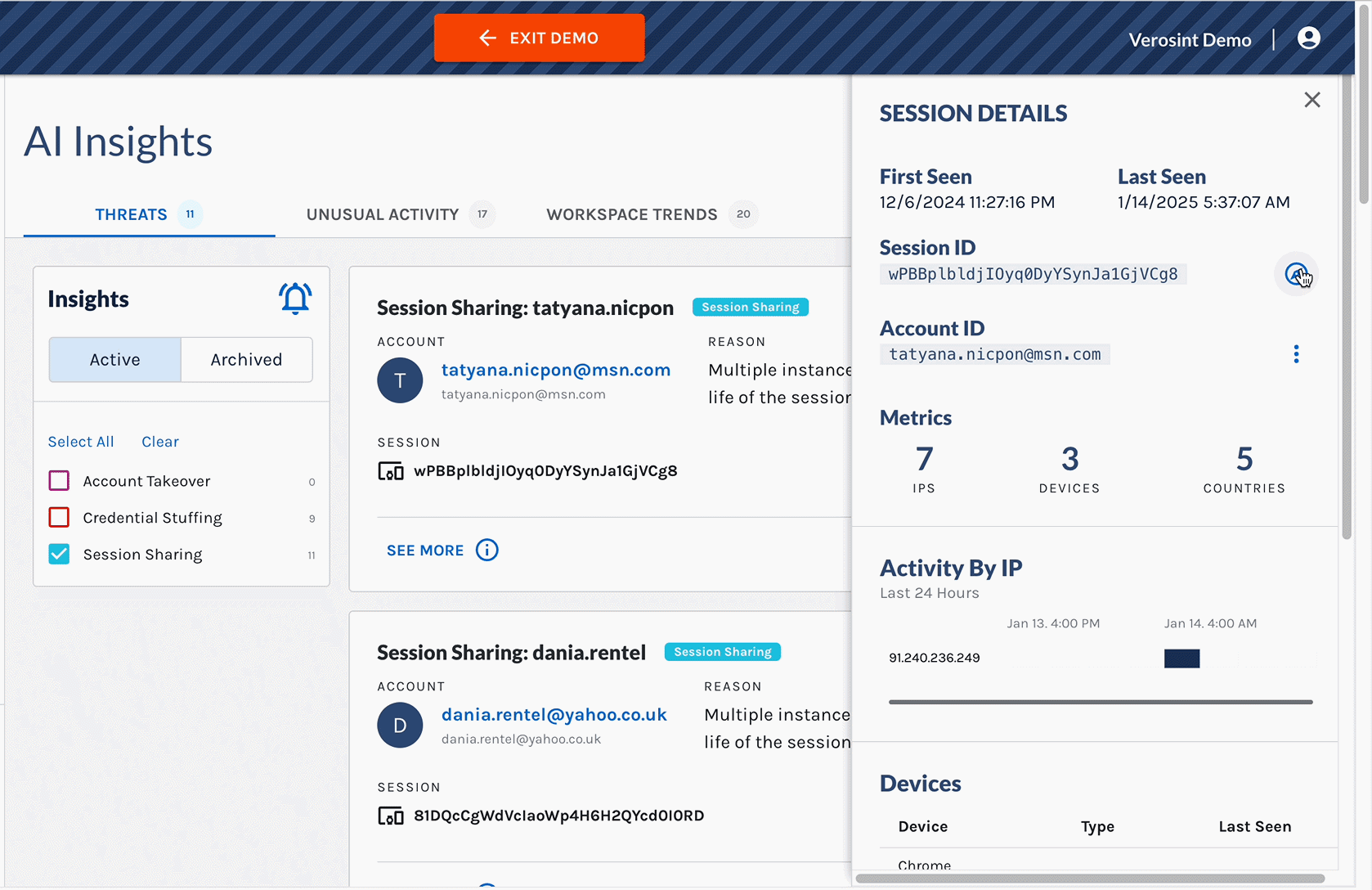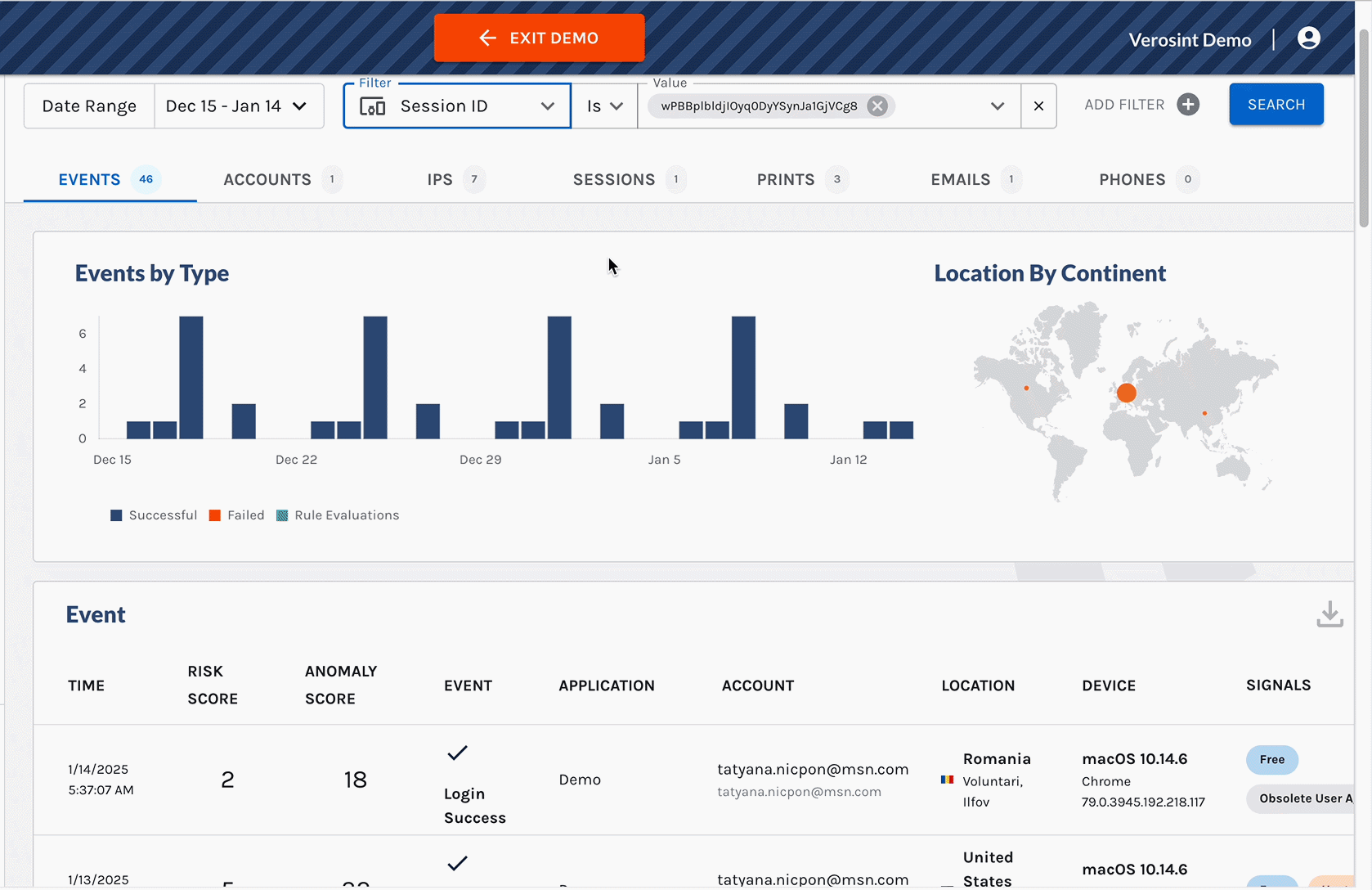
New Session Sharing threat detection in AI Insights
1️⃣ Session Sharing Threat Card & Details Panel
- A new Session Sharing threat card is now generated in AI Insights when Verosint detects multiple instances of impossible travel and device changes for a given session.
- From the threat card, you can access a Session Details Panel which provides more context for you to investigate and verify the threat.
2️⃣ Email Notifications for Session Sharing Threats
- Receive email alerts when Session Sharing is detected, ensuring you can respond promptly, even when not actively monitoring your Verosint workspace.
3️⃣ Session Sharing Risk and Session Details Panel in Event Explorer
- Got a hunch that session sharing is occurring in your workspace? Verify if by searching for the Session Sharing risk in the Event Explorer.
- You can also access the Session Details Panel in the Sessions tab of the Event Explorer. Click on a specific row to see key details of the session.
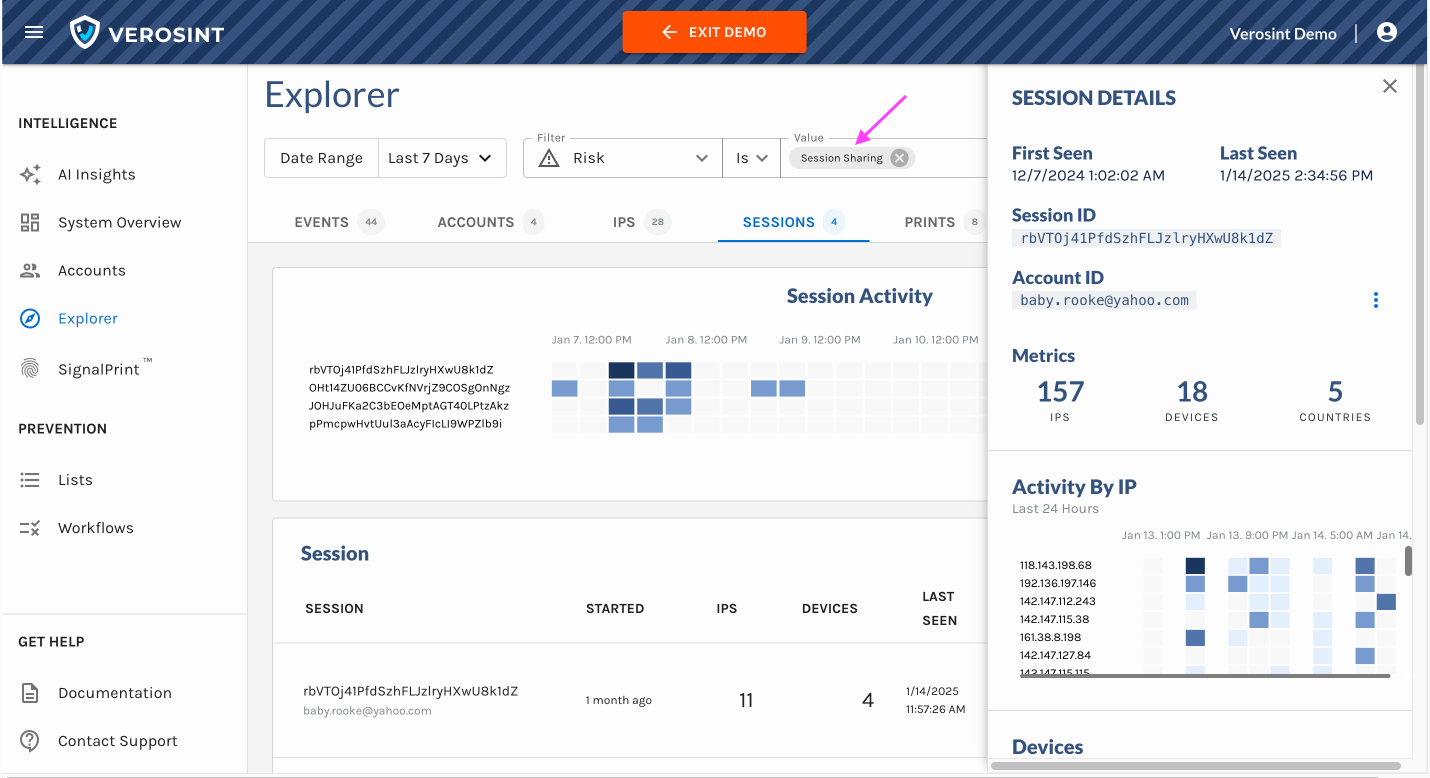
We've added Session Sharing to the list of Verosint Risks you can search by in Event Explorer
Why Does This Matter?
Token stealing is a growing attack vector because sessions are long-lived. These tokens are targeted by attackers to bypass authentication entirely, enabling session sharing, which significantly increases the risk of Account Takeover (ATO).
- Session Stealing = ATO Risk: By hijacking active sessions, attackers can assume legitimate user identities, making this a critical threat vector.
- Long-Lived Sessions Add Risk: Sessions often remain active for days or even months, creating an extended window of opportunity for attackers to exploit them.
By providing tools to detect and respond to Session Sharing, Verosint empowers you to take control of session security and defend against token-stealing attacks. Let us know how these tools work for you and share your feedback—we’re always looking to improve! 😊