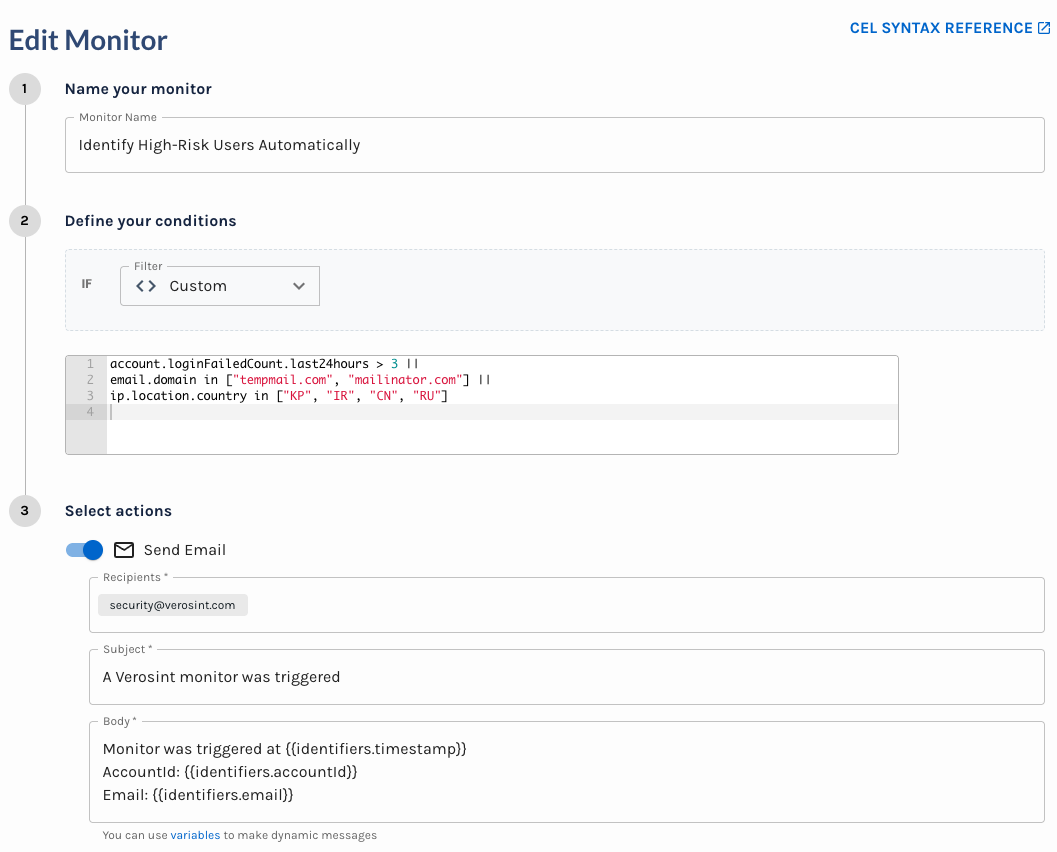
Ex: Identify High-Risk Users Automatically
Goal: Identify customers who display risky behavior patterns (e.g., repeated failed logins, signups from disposable emails, restricted geographies) and classify them into a “High Risk Users” list for further investigation or action.
Steps:
- Create a Monitor: Give your monitor a unique name, such as
Identify High Risk Users. - Define Conditions: Use the filter builder or custom CEL expressions to specify what activity you want to detect.
- For example, you could define the following set of conditions:
- Flags users with >3 failed logins in the last 24 hours, or
- Flags disposable email domains, or
- Flags logins coming from the specified high-risk countries (in this case, North Korea, Iran, China, or Russia).
- Configure Automated Actions: Send an email, Slack, or Teams notification to the Security team. In the future, you will be able to automatically add the associated account ID and email address to a "High Risk Users" list.
- Result: Identify and Trigger Security Alerts for High-Risk Users Automatically:
- Users who trigger any high-risk condition (more than 3 failed logins in 24 hours, disposable email domain, or login from a high-risk country: KP, IR, CN, RU) are automatically flagged.
- Security is alerted immediately, allowing the team to review, challenge, or block the account before it can cause harm.
- High-risk users are classified in real time, giving your team proactive visibility and control over potentially fraudulent or risky activity.
Identify high-risk users automatically and take action with this example monitor
Updated 5 months ago